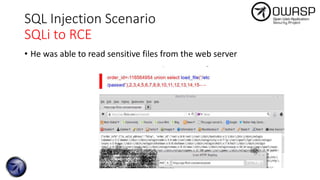
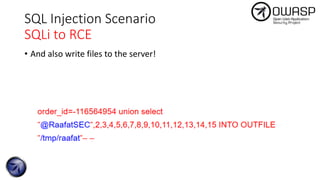
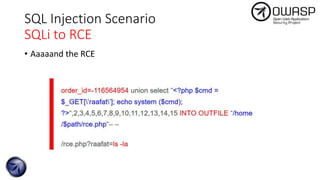
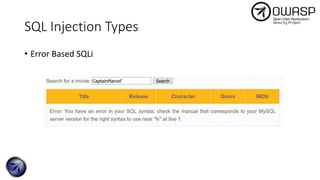
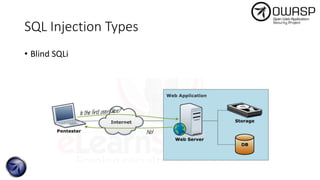
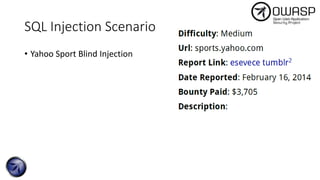
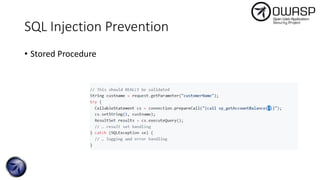
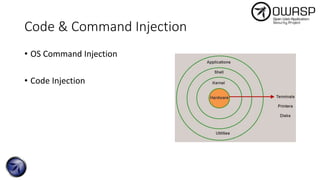
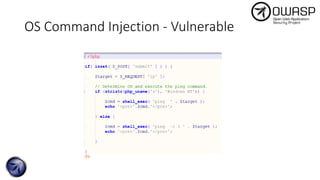
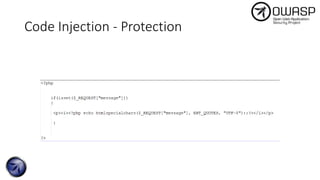
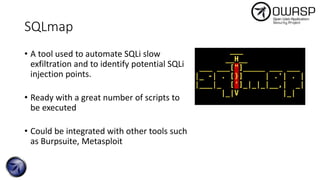
The document discusses SQL injection attacks, detailing various types such as inband, blind, and time-based injections, along with real-world scenarios including exploits. It emphasizes the importance of the Open Web Application Security Project (OWASP) in raising awareness about application security, and provides prevention techniques like prepared statements and input validation. Additionally, tools like sqlmap are introduced for automating the identification of SQL injection vulnerabilities.





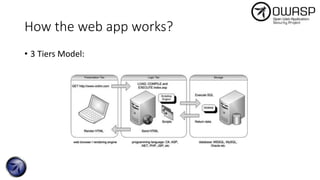




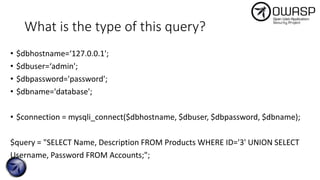
![What about this?
$id = $_GET['id'];
$connection = mysqli_connect($dbhostname, $dbuser, $dbpassword,
$dbname);
$query = "SELECT Name, Description FROM Products WHERE ID='$id';";
$results = mysqli_query($connection, $query);
display_results($results);](https://image.slidesharecdn.com/a1-injectionattacks-190319015732/85/OWASP-Top-10-Day-1-A1-injection-attacks-12-320.jpg)