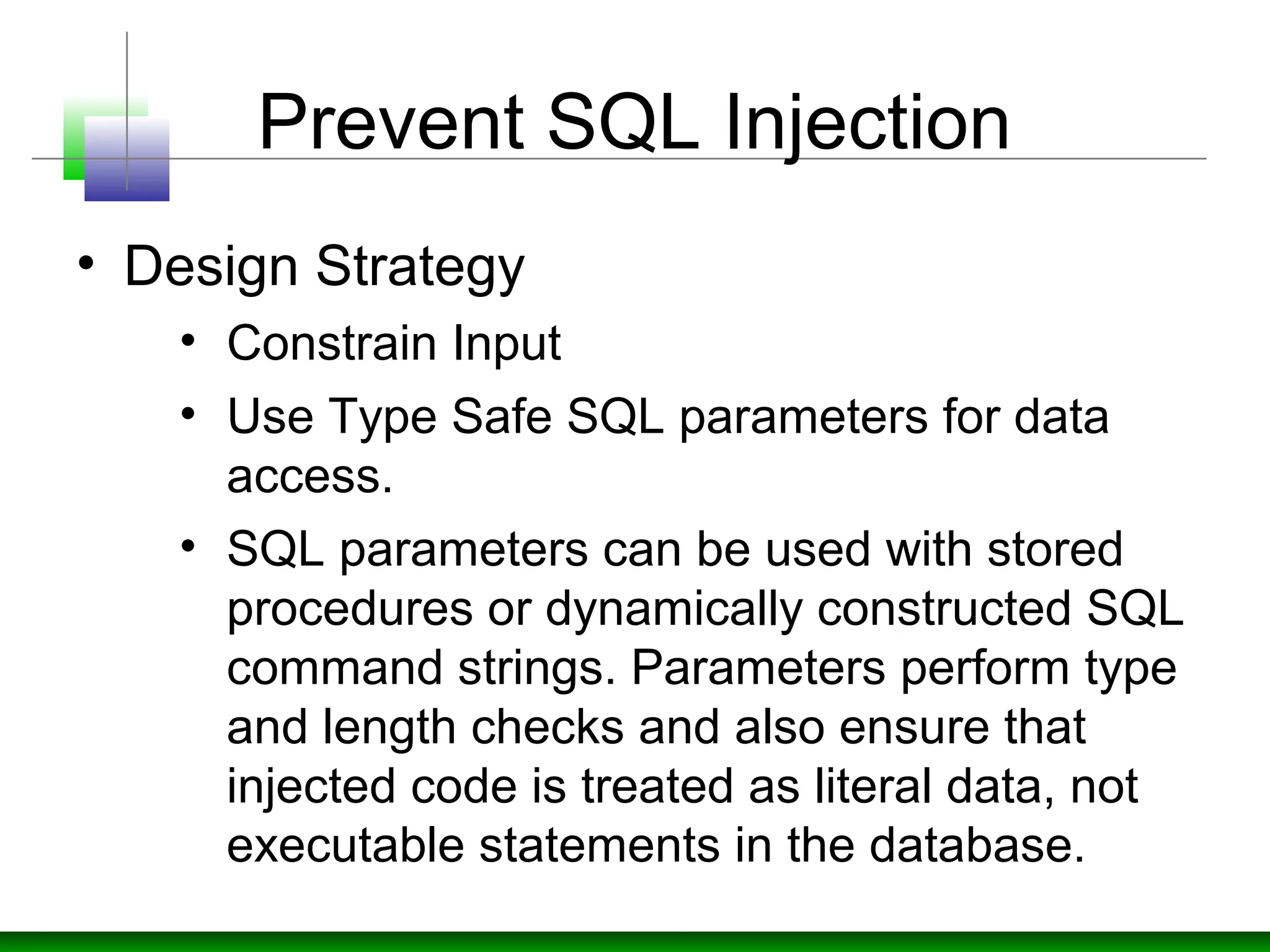
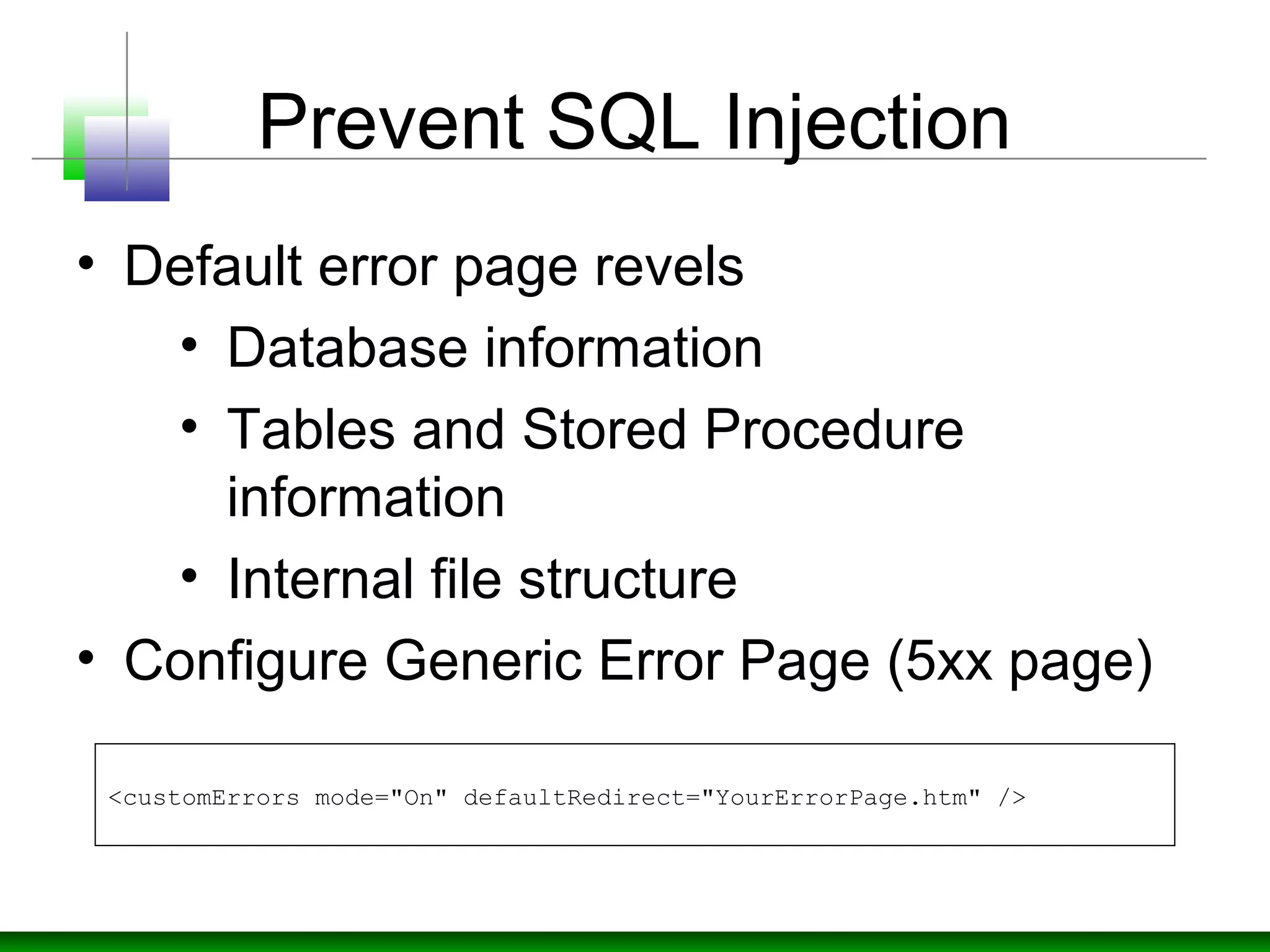
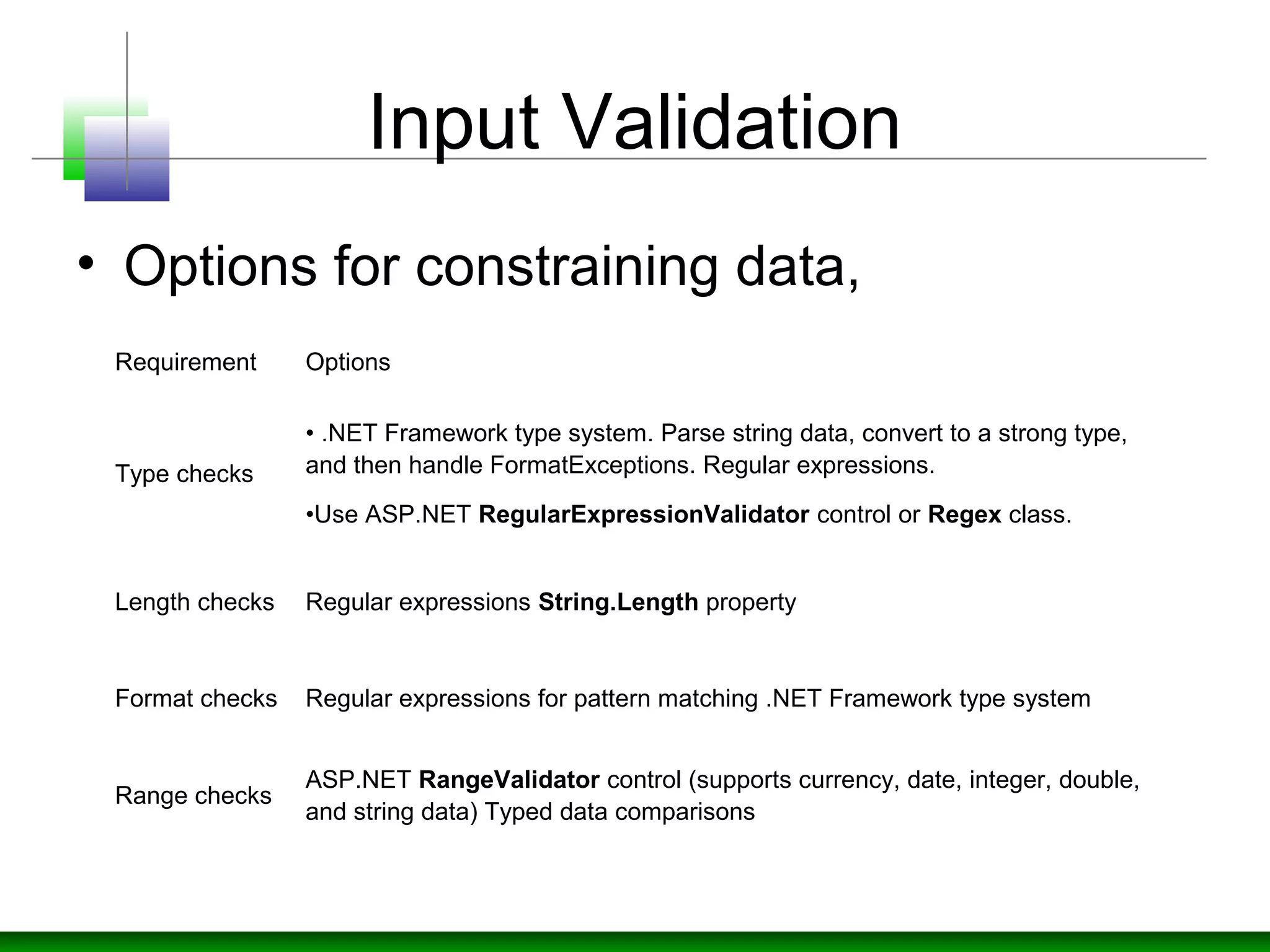
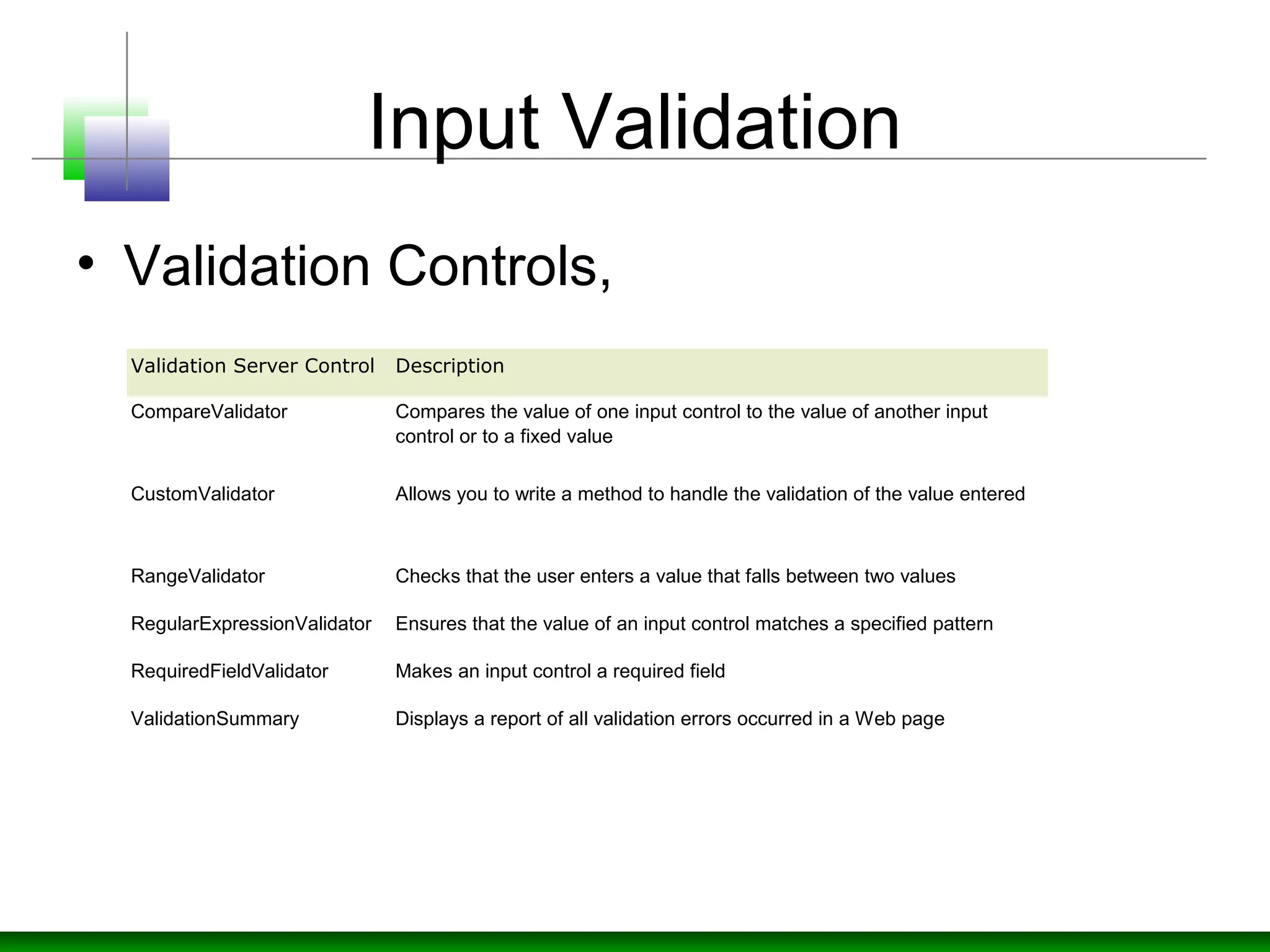
The document discusses strategies for defending against input injection attacks, including SQL injection. It recommends centralizing input validation and assuming all input is malicious. Specific strategies covered include constraining, rejecting, and sanitizing input through techniques like type checks, length checks, format checks, range checks, and whitelisting valid characters. It also discusses using validation controls and regular expressions for validation. The document recommends input validation libraries like ESAPI and using prepared statements with SQL parameters to prevent SQL injection.





![Input Validation
• Regex (System.Text.RegularExpressions)
Regular expressions are much easier to understand if you use the
following syntax and comment each component of the expression
using #. To enable comments, you must also specify
RegexOptions.IgnorePatternWhitespace, which means that non-escaped
white space is ignored.
Regex regex = new Regex(@"
^ # anchor at the start
(?=.*d) # must contain at least one
digit
(?=.*[a-z]) # must contain one lowercase
(?=.*[A-Z]) # must contain one uppercase
.{8,10} # From 8 to 10 characters in
length
$ # anchor at the end",
RegexOptions.IgnorePatternWhitespace);](https://image.slidesharecdn.com/7-151026084613-lva1-app6892/75/Defending-against-Injections-8-2048.jpg)
![Input Validation
• String Fields (Name, Address..)
• For Social Security Number the
expression would be "d{3}-d{2}-d{4}"
<form id="WebForm" method="post" runat="server">
<asp:TextBox id="txtName" runat="server"></asp:TextBox>
<asp:RegularExpressionValidator id="nameRegex "runat="server"
ControlToValidate="txtName"
ValidationExpression="[a-zA-Z'.'-'s]{1,40}"
ErrorMessage="Invalid name">
</asp:regularexpressionvalidator>
</form>](https://image.slidesharecdn.com/7-151026084613-lva1-app6892/75/Defending-against-Injections-9-2048.jpg)


![Input Validation
• Sanitizing Inputs
• Strips out a range of potentially unsafe
characters, including < > " ' % ; ( ) &.
private string SanitizeInput(string input)
{
Regex badCharReplace = new Regex(@"([<>""'%;()&])");
string goodChars = badCharReplace.Replace(input, "");
return goodChars;
}](https://image.slidesharecdn.com/7-151026084613-lva1-app6892/75/Defending-against-Injections-14-2048.jpg)
![Input Validation
• Validating HTML controls
private void Page_Load(object sender, System.EventArgs e)
{
// Note that IsPostBack applies only for
// server forms (with runat="server")
if ( Request.RequestType == "POST" ) // non-server forms
{
// Validate the supplied email address
if( !Regex.Match(Request.Form["email"],
@"w+([-+.]w+)*@w+([-.]w+)*.w+([-.]w+)*",
RegexOptions.None).Success)
{
// Invalid email address
}
// Validate the supplied name
if ( !RegEx.Match(Request.Form["name"],
@"[A-Za-z'- ]",
RegexOptions.None).Success)
{
// Invalid name
}
}
}](https://image.slidesharecdn.com/7-151026084613-lva1-app6892/75/Defending-against-Injections-15-2048.jpg)





![Input Validation
• ESAPI Sample
public void Test_StringRuleRange()
{
IValidator validator = Esapi.Validator;
// Test range
string id = Guid.NewGuid().ToString();
StringValidationRule rule = new StringValidationRule() { MinLength = 1,
MaxLength = 10 };
validator.AddRule(id, rule);
Assert.IsTrue(validator.IsValid(id, "a"));
Assert.IsFalse(validator.IsValid(id, ""));
Assert.IsFalse(validator.IsValid(id, "12345678901"));
}
public void Test_IsValidPrintable()
{
IValidator validator = Esapi.Validator;
Assert.IsTrue(validator.IsValid(BuiltinValidationRules.Printable, "abcDEF"));
Assert.IsTrue(validator.IsValid(BuiltinValidationRules.Printable, "!
@#R()*$;><()"));
char[] bytes = new char[] { (char)(0x60), (char)(0xFF), (char)(0x10), (char)
(0x25) };
Assert.IsFalse(validator.IsValid(BuiltinValidationRules.Printable, new
String(bytes)));
}](https://image.slidesharecdn.com/7-151026084613-lva1-app6892/75/Defending-against-Injections-23-2048.jpg)