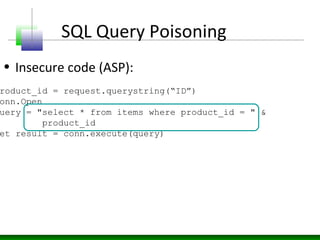
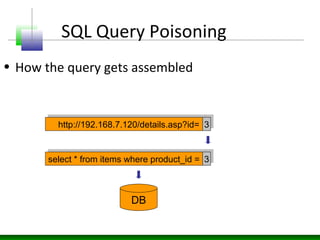
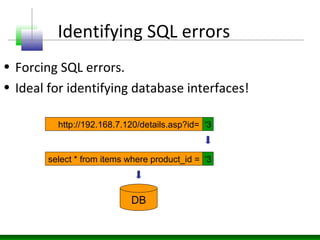
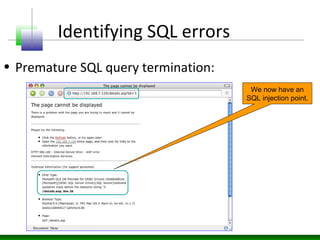
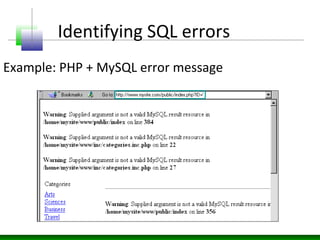
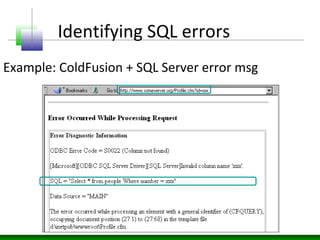
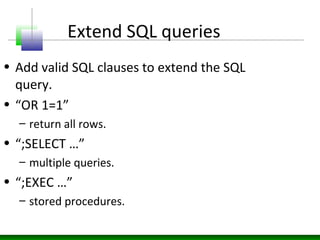
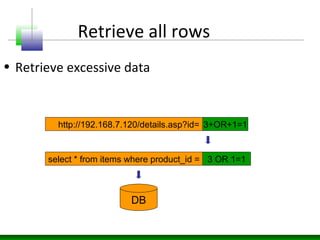
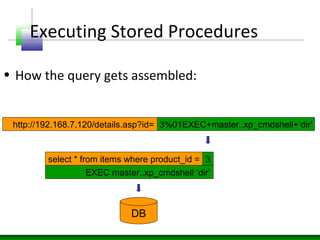
This document discusses SQL injection vulnerabilities and techniques for exploiting them. It explains how user-supplied parameters can be manipulated to alter SQL queries and access unauthorized data or execute stored procedures. Some methods covered include adding SQL syntax like OR 1=1 to return all rows, using semicolons to concatenate queries, and prematurely terminating queries with characters like single quotes. The document also provides examples of forcing SQL errors to identify vulnerabilities and tips for retrieving excessive data or invoking stored procedures during an SQL injection attack.