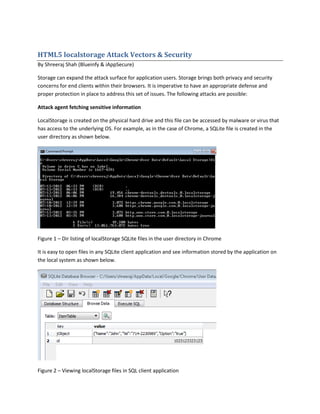
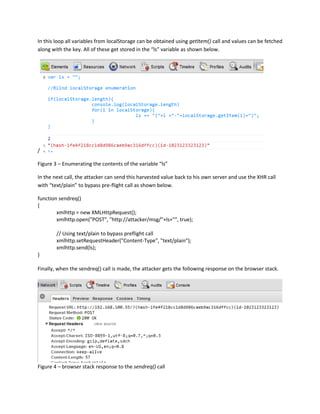
Local storage can expand the attack surface for web applications by allowing sensitive data to be accessed through malware or viruses. It is also vulnerable to cross-site scripting (XSS) attacks, where malicious code could harvest and transmit stored data. Additionally, lack of privacy controls enables persistent user tracking across domains and invasion of privacy. Proper security defenses and protections are needed to mitigate risks from local storage.