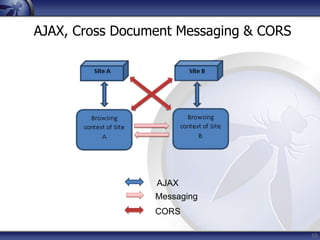
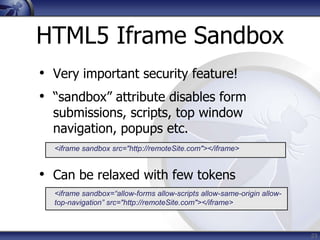
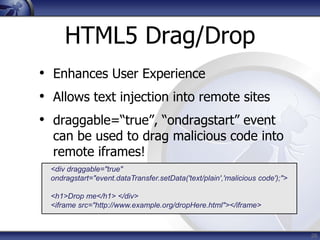
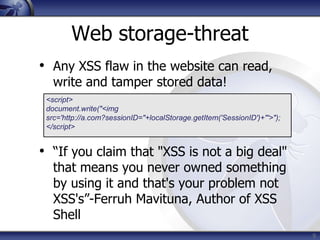
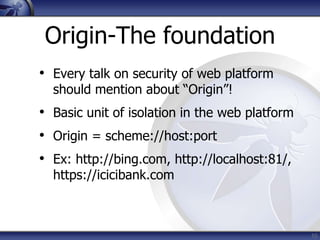
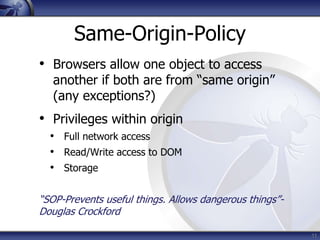
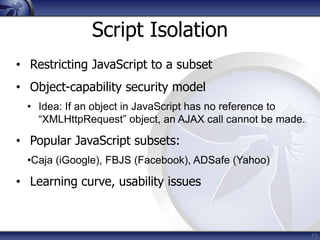
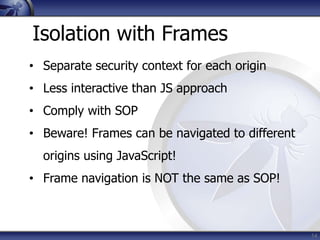
The document discusses security considerations for HTML5. It notes that while HTML5 specifications are not inherently flawed, bad code can introduce new vulnerabilities. It outlines several attack vectors like XSS, history tampering, web storage manipulation, and clickjacking. It also discusses mitigations like script isolation, cross-document messaging, sandboxing, and CORS, noting their limitations. The document aims to raise awareness of the expanded client-side attack surface in HTML5.






![History tampering
• Then - history.go(), .forward(), .back()
• Now – history.pushState(data, title, [url])
history.replaceState(data, title, [url])
• Overflowing user’s history
for(i=0;i<50;i++){
history.pushState({}, "", “/youAreTrapped.html"); }
• URL spoofing
• Redirection to infected sites
7](https://image.slidesharecdn.com/html5security-krishna-120522003138-phpapp02/85/Html5-security-7-320.jpg)



![Messaging API-Beware of origin & framing!
//Posting message to a cross domain partner.
frames[0].postMessage(“Hello Partner!”, "http://localhost:81/");
//Retrieving message from the sender
window.onmessage = function (e) {
if (e.origin == 'http://localhost') {
//sanitize and accept data
}
};
17](https://image.slidesharecdn.com/html5security-krishna-120522003138-phpapp02/85/Html5-security-17-320.jpg)