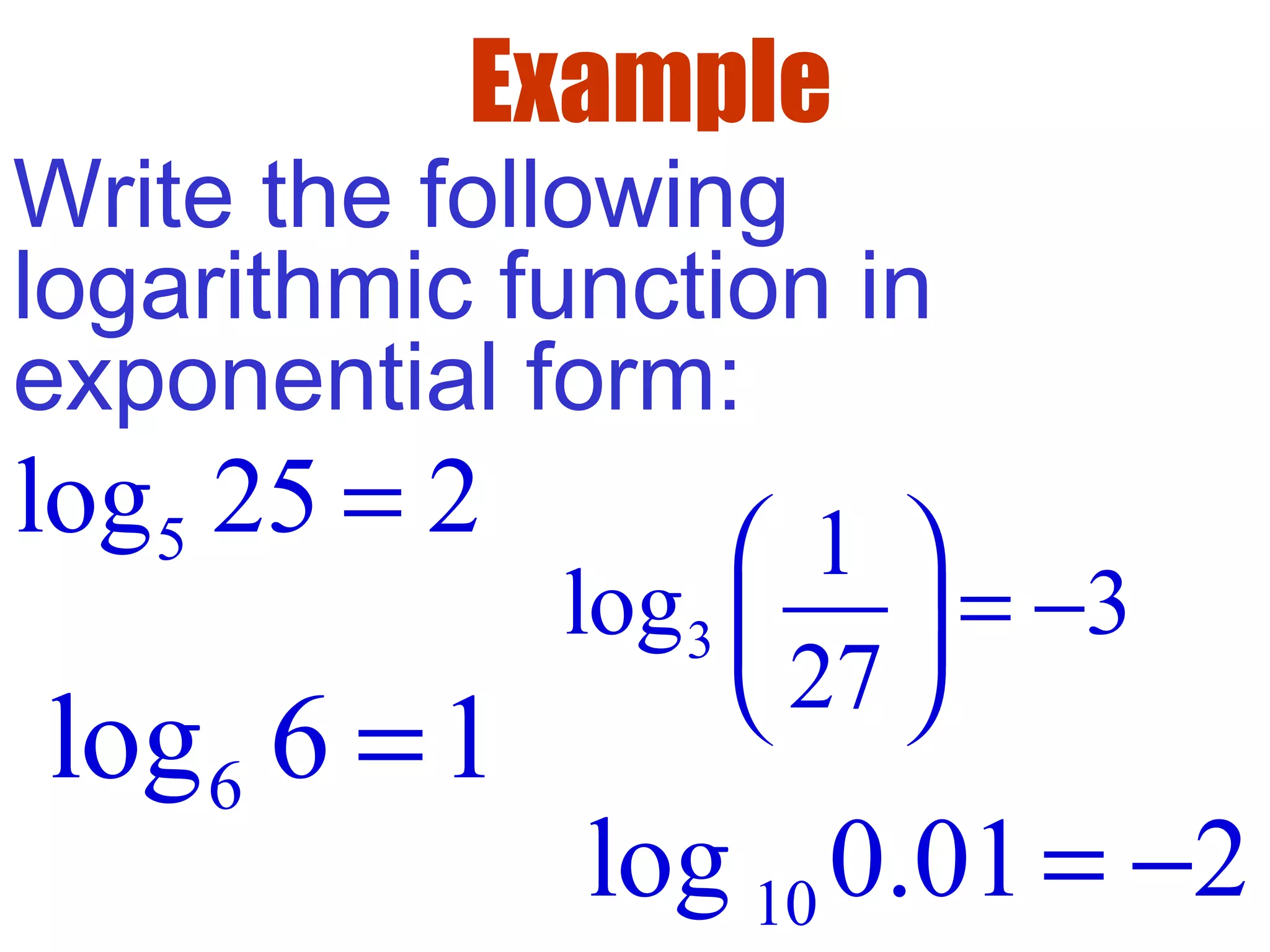
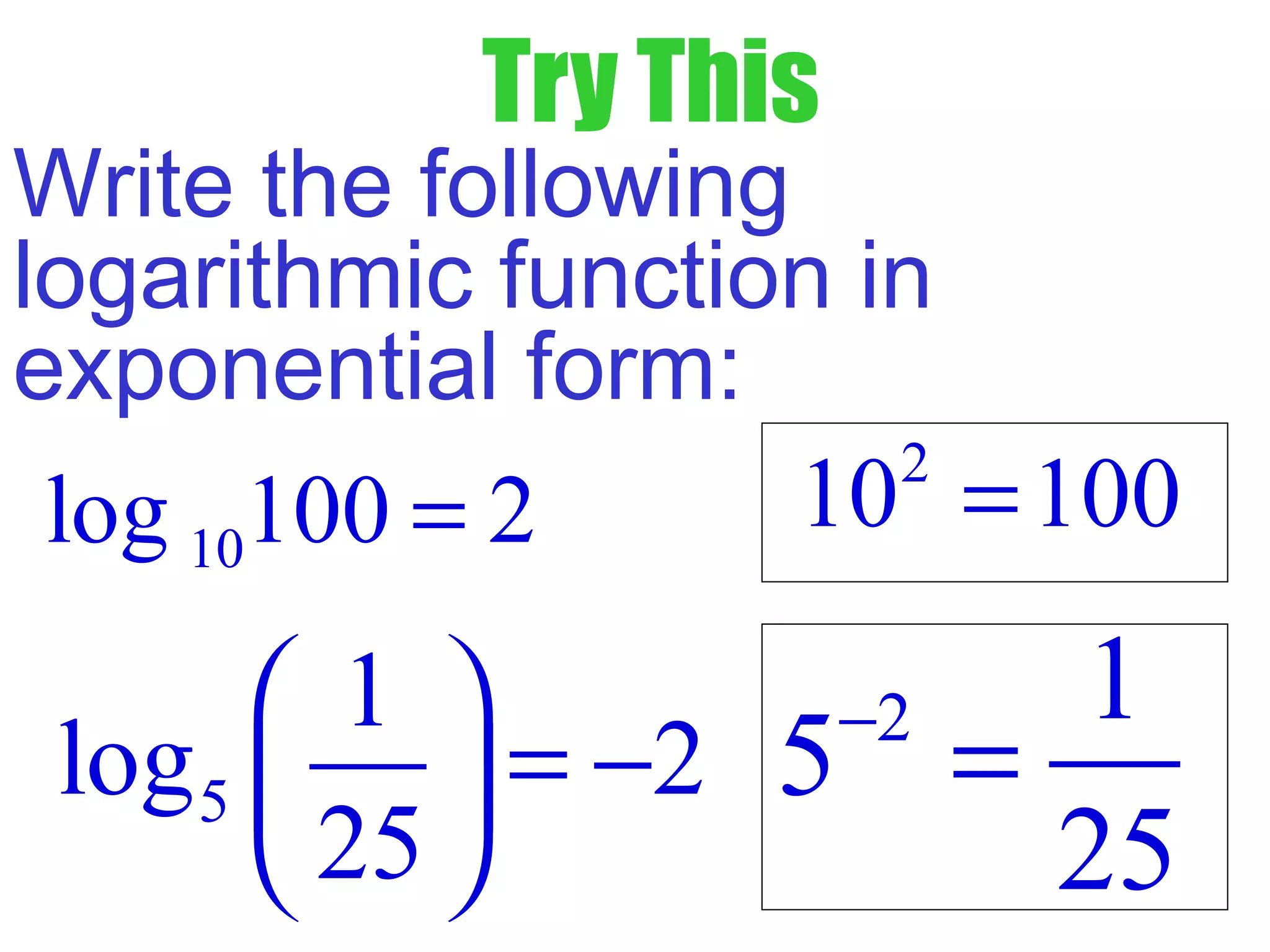
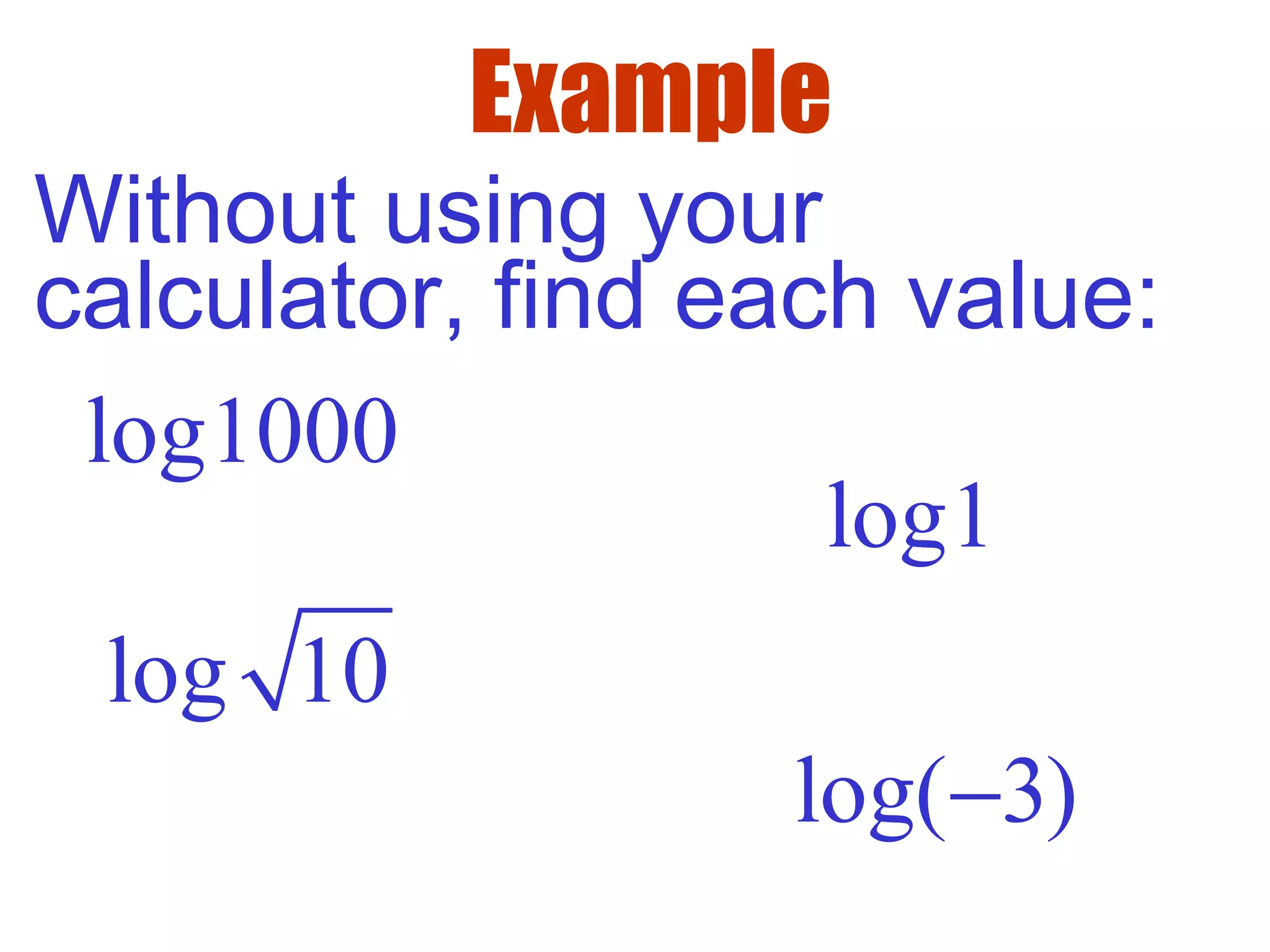
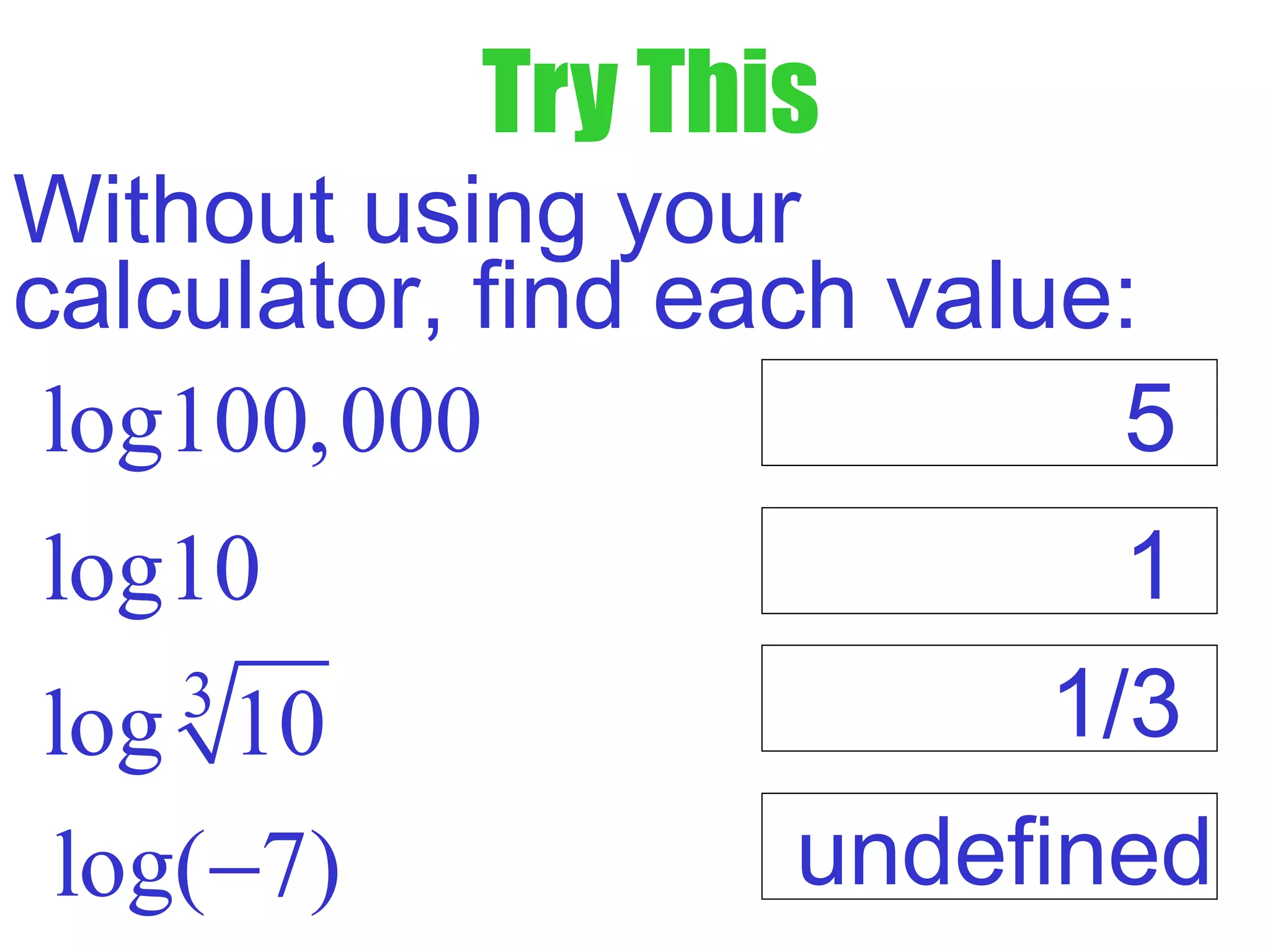
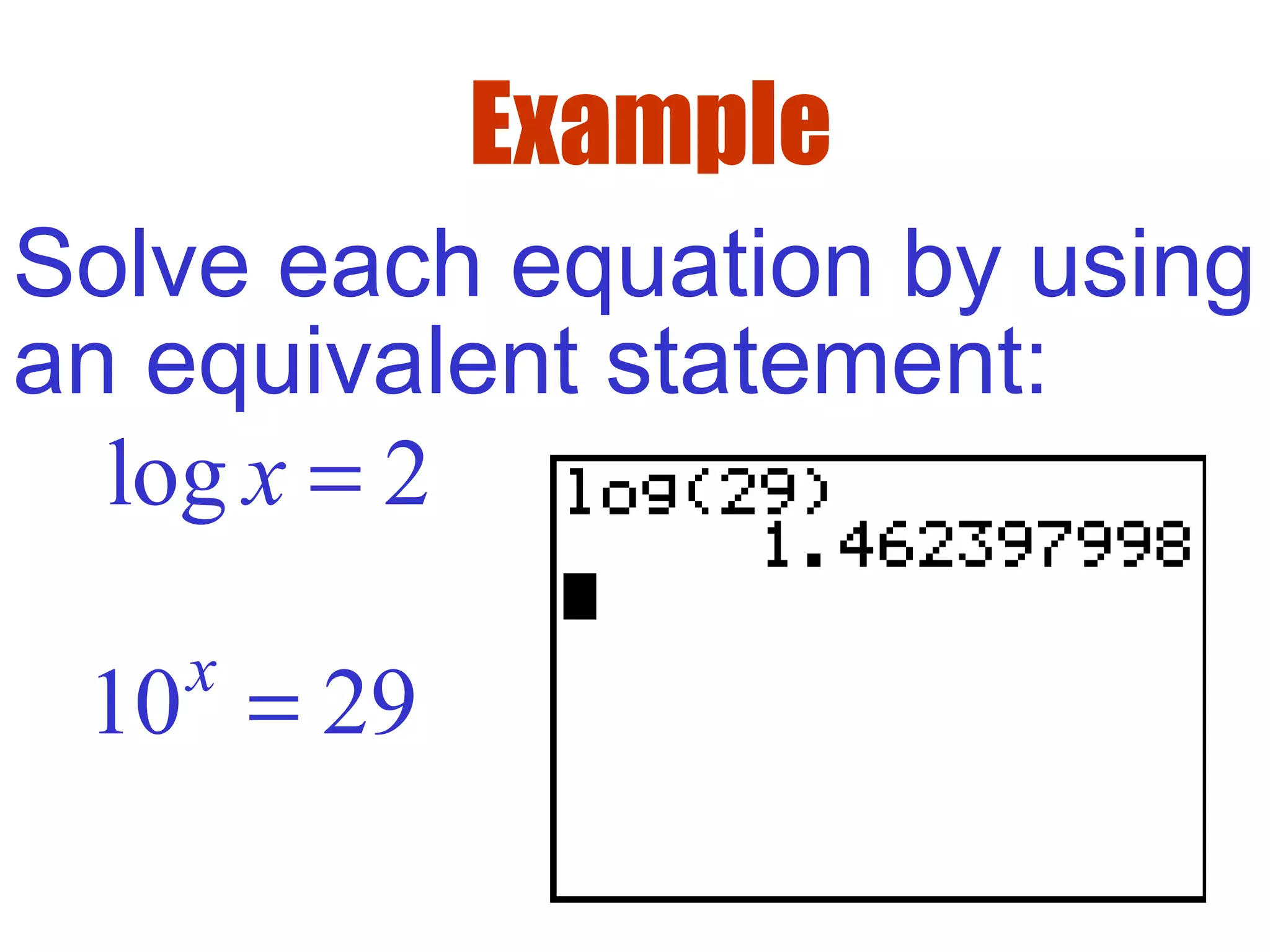
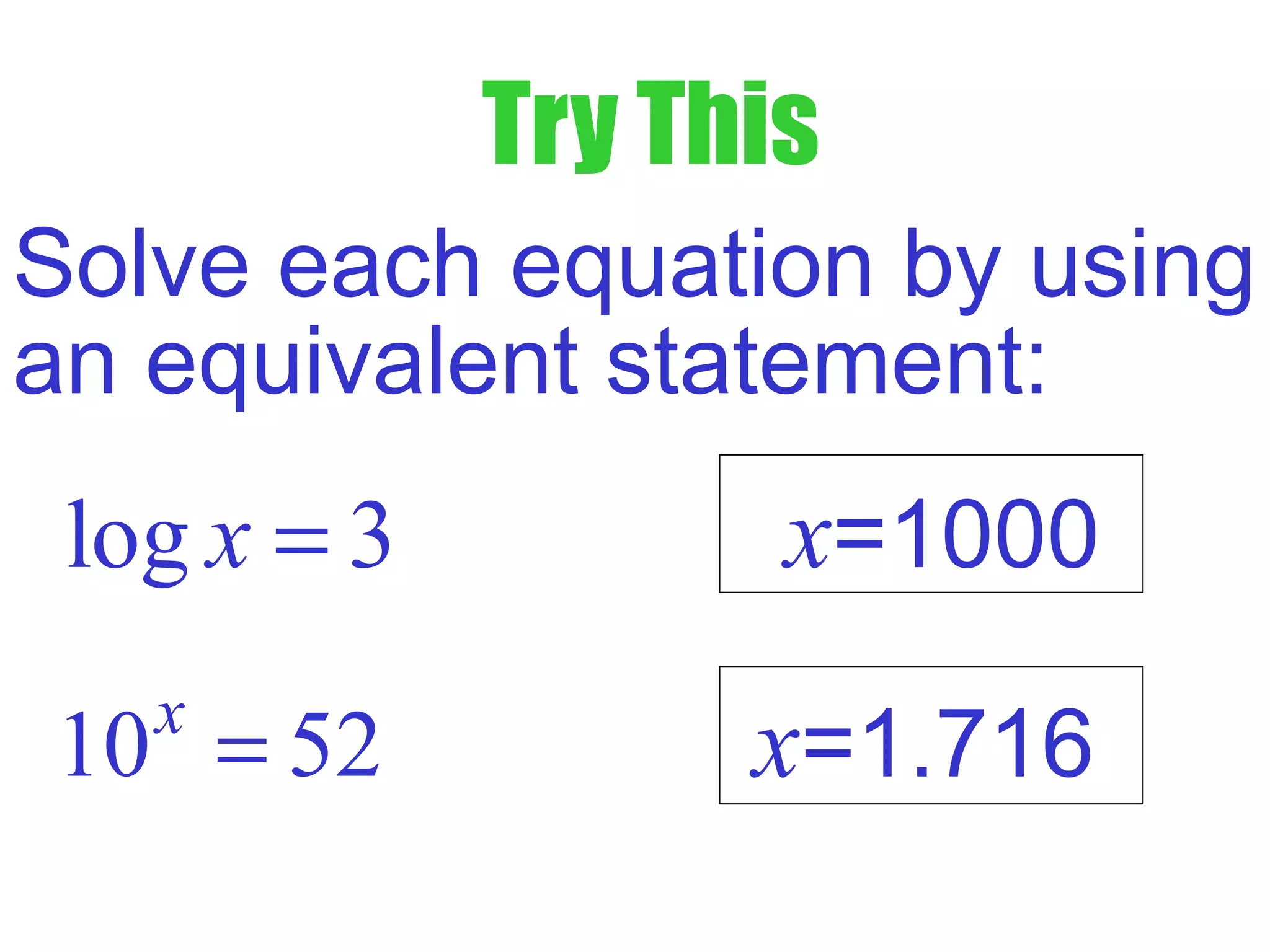
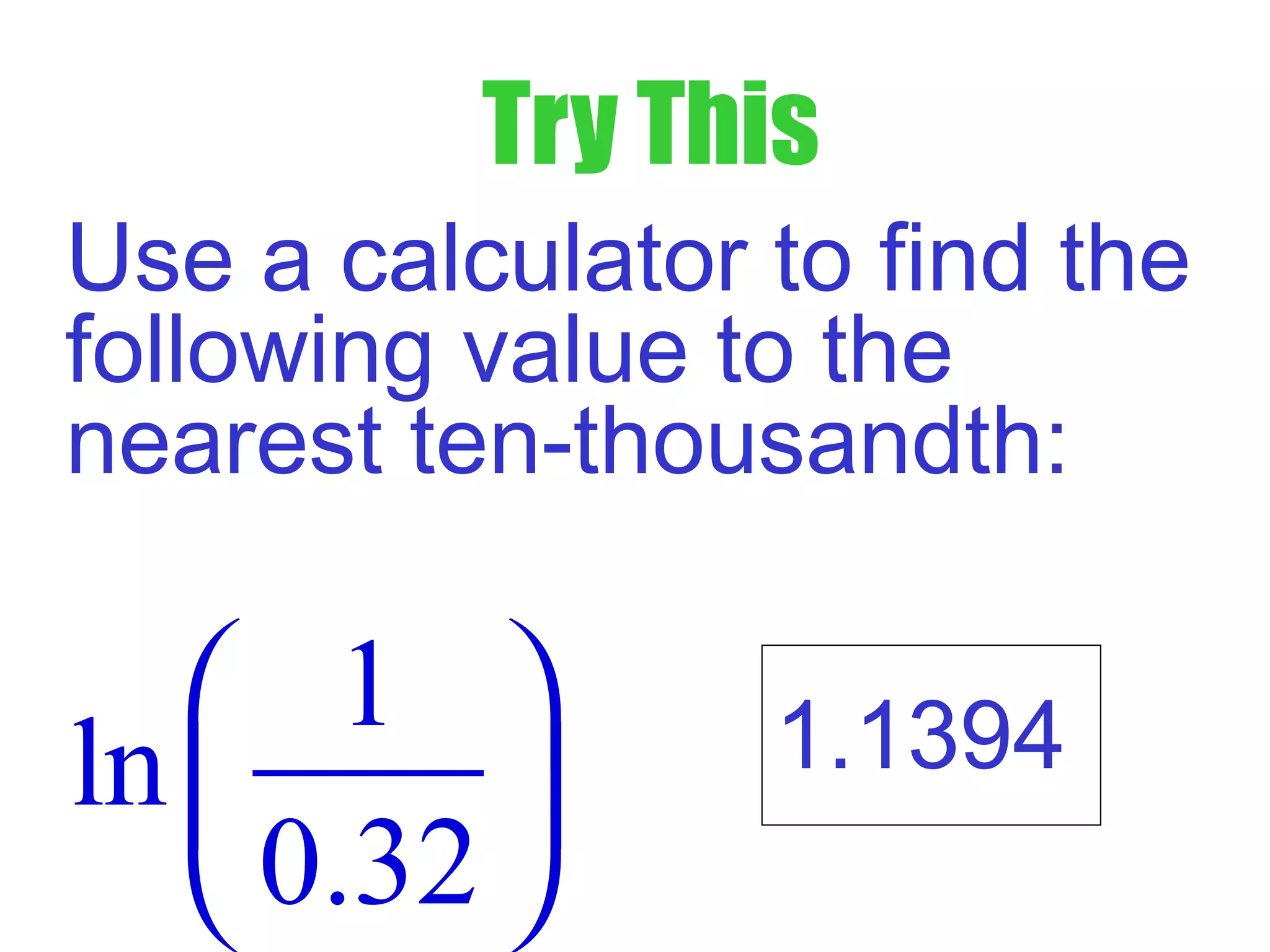
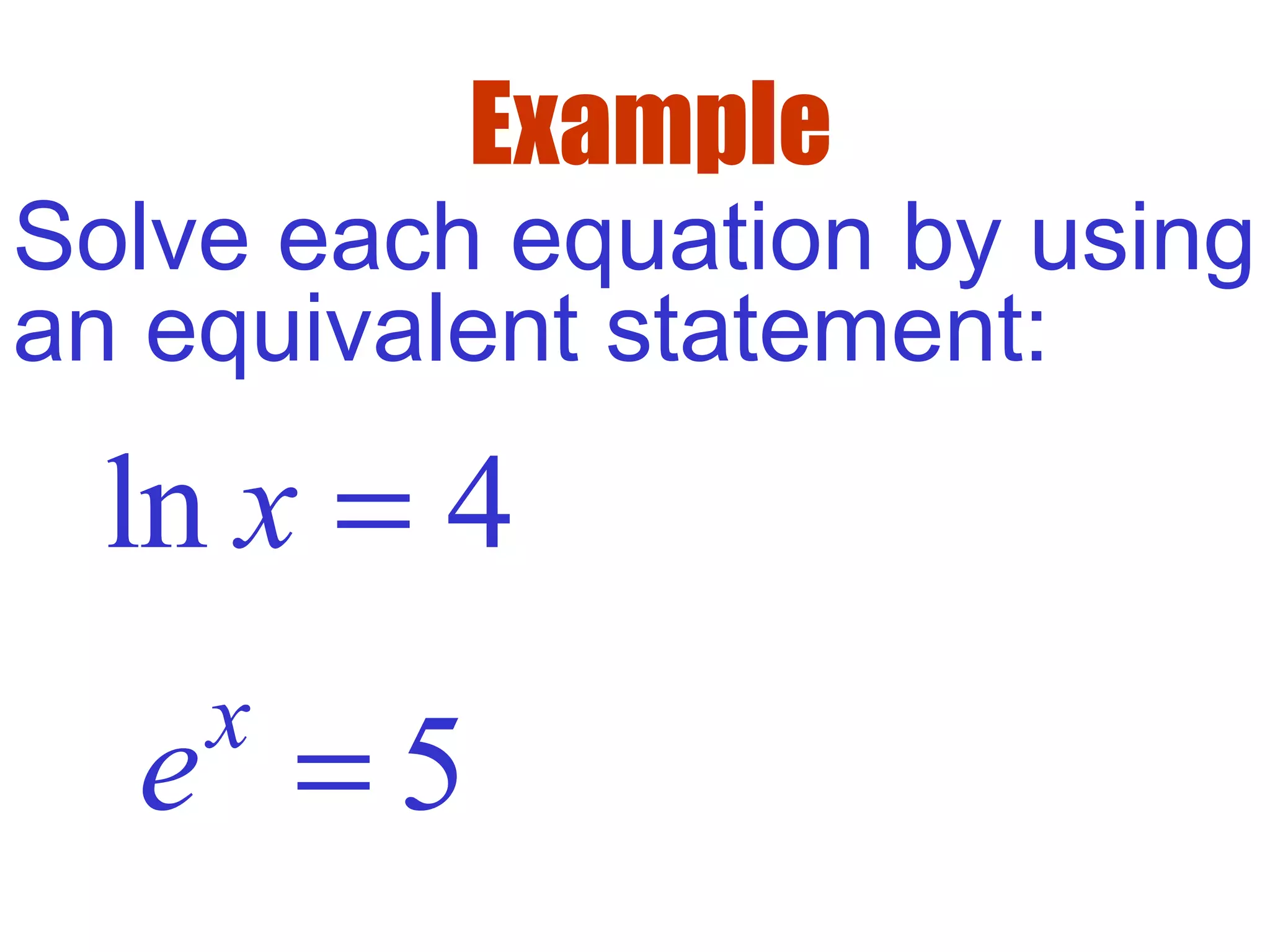
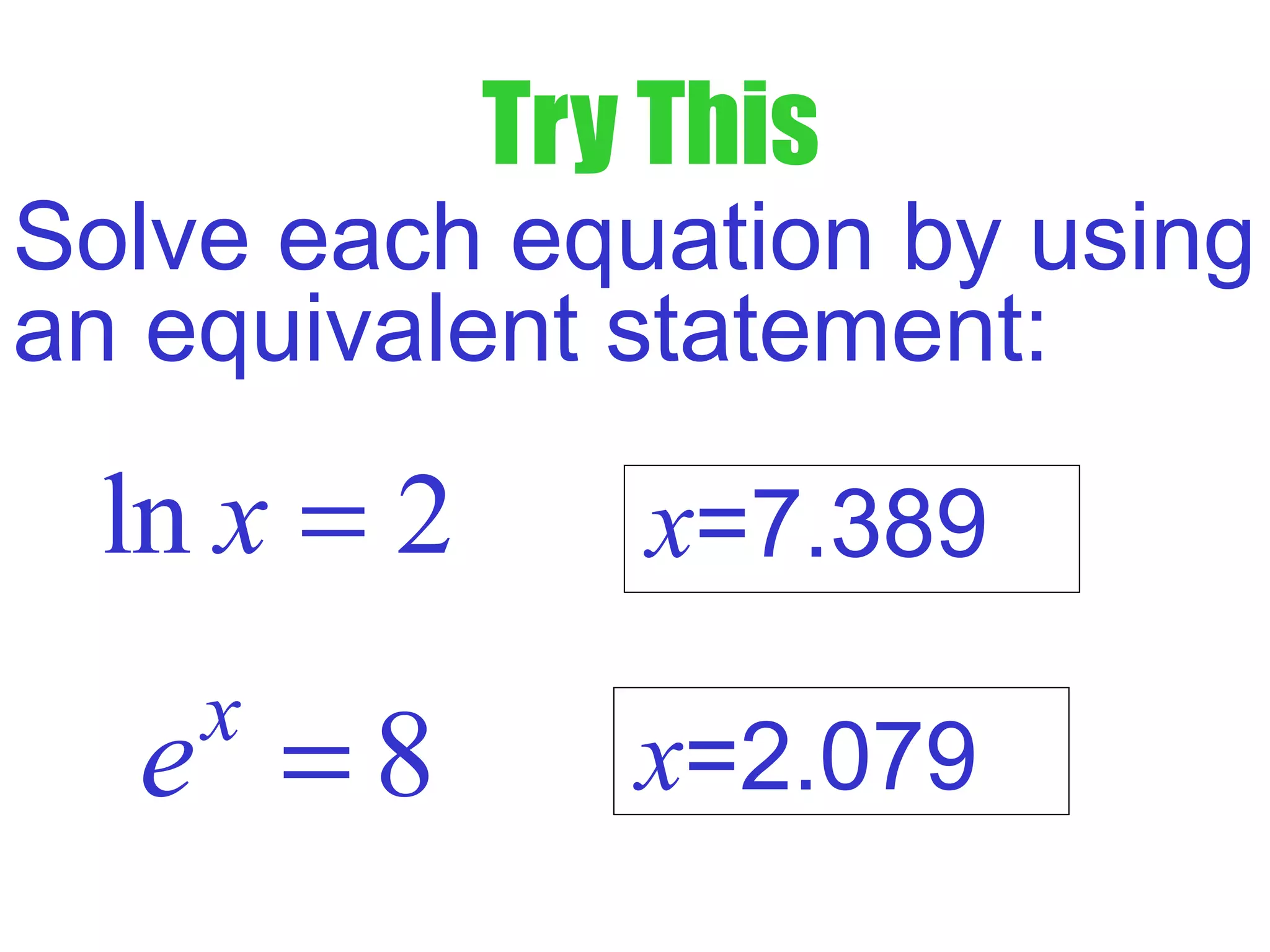
This document defines common (base 10) and natural (base e) logarithms and explains how to evaluate, solve equations involving, and graph logarithmic functions. It also discusses important properties of logarithms including:
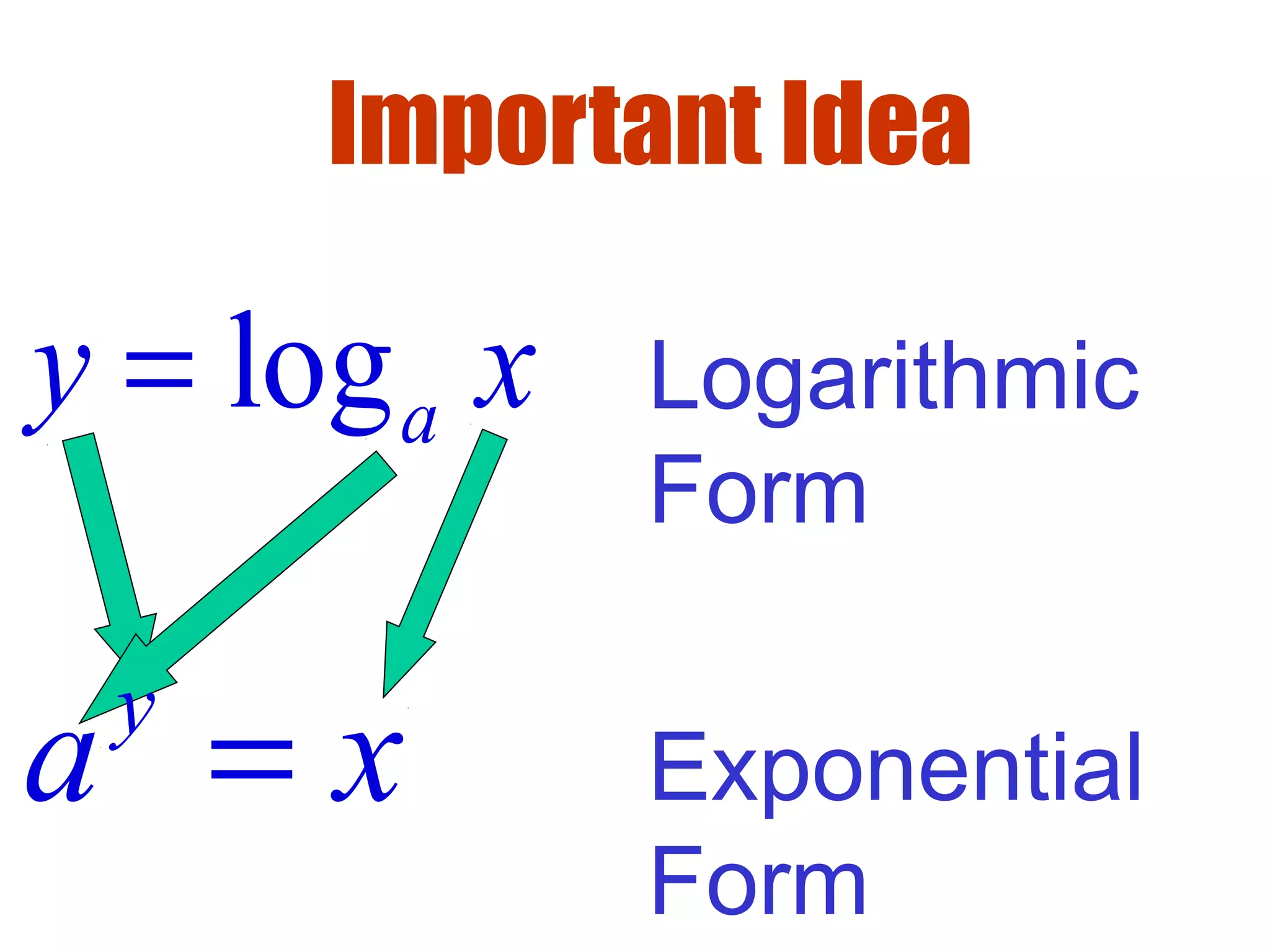
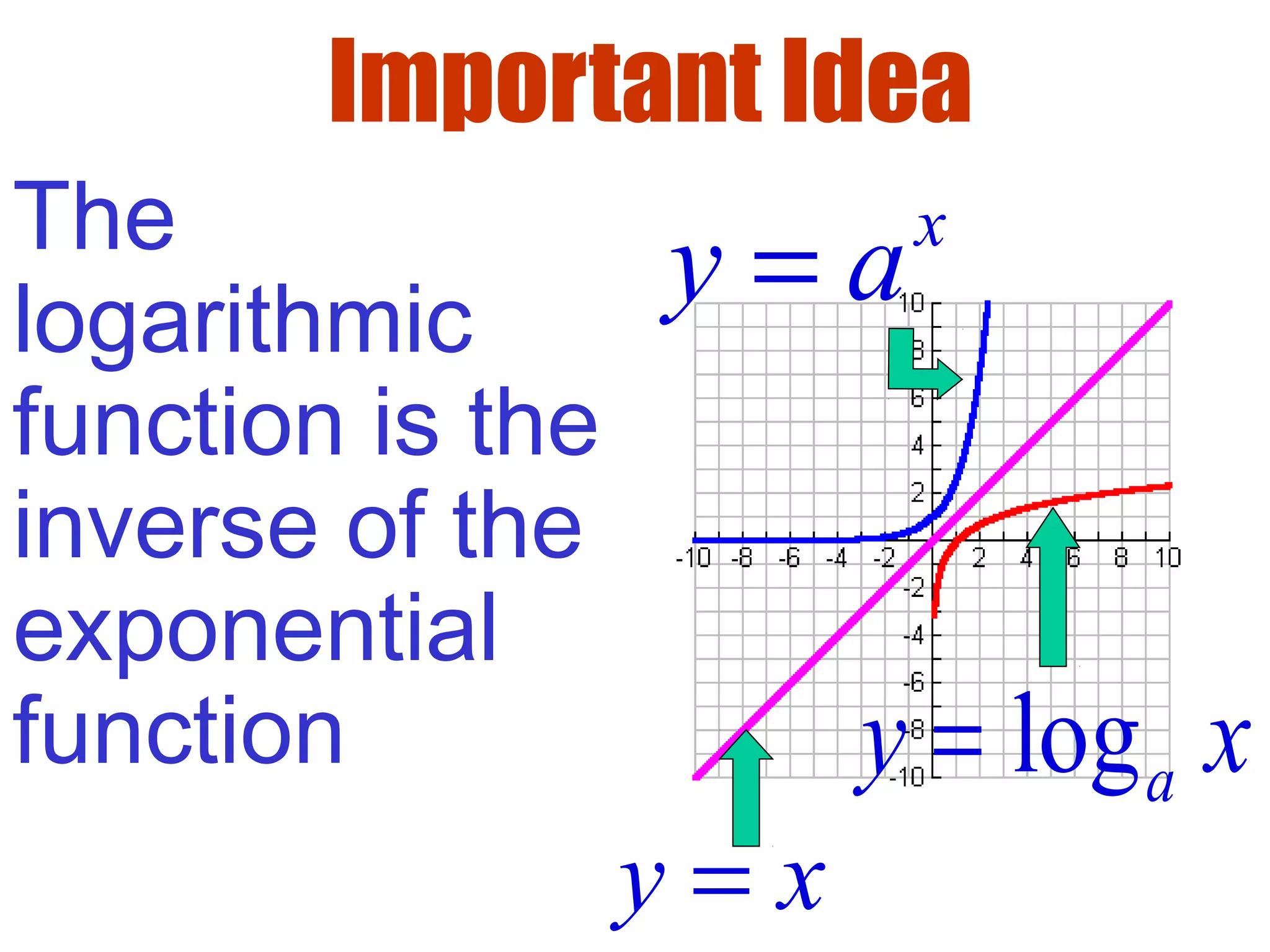
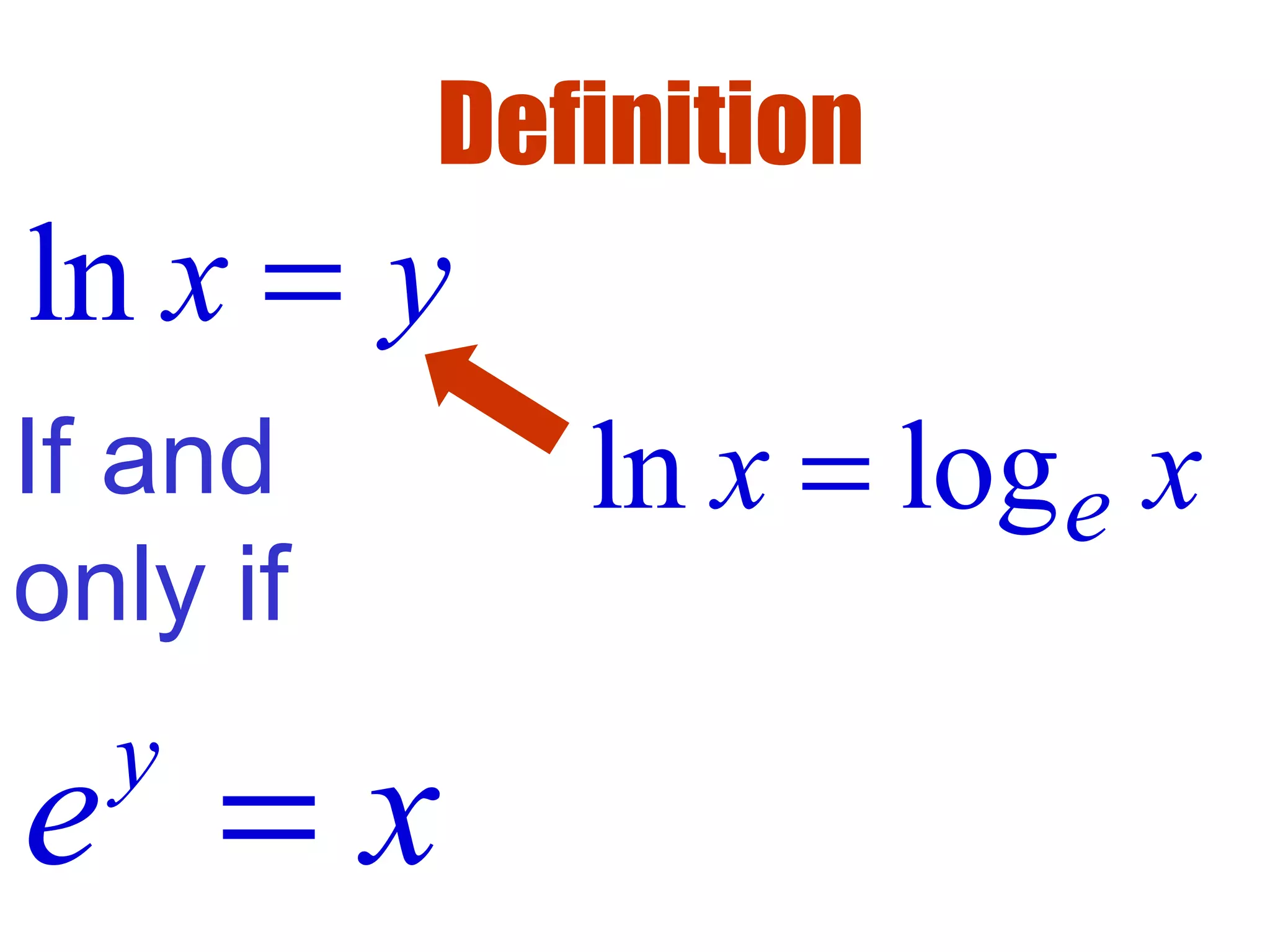
- Logarithms are the inverse functions of exponentials.
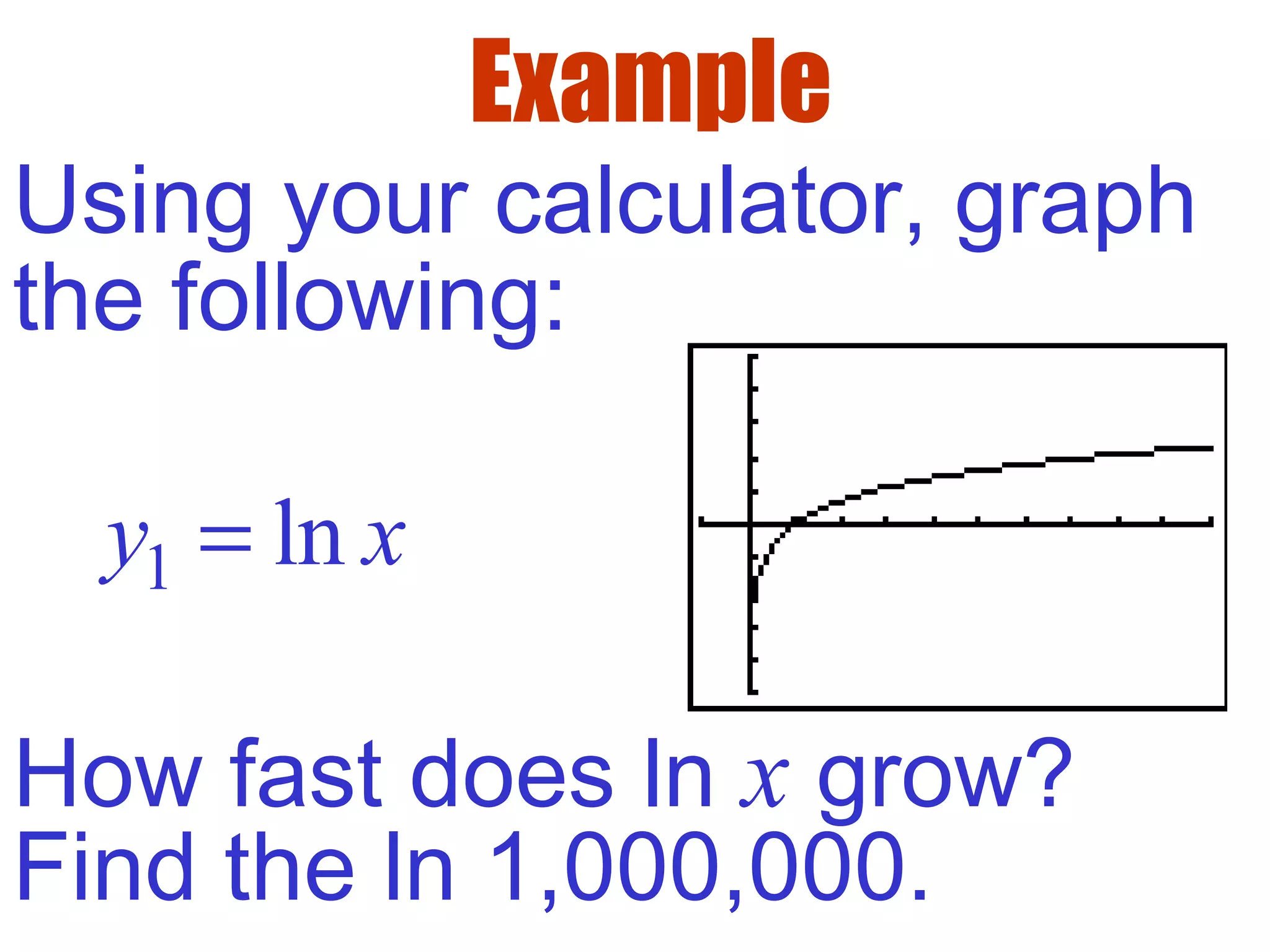
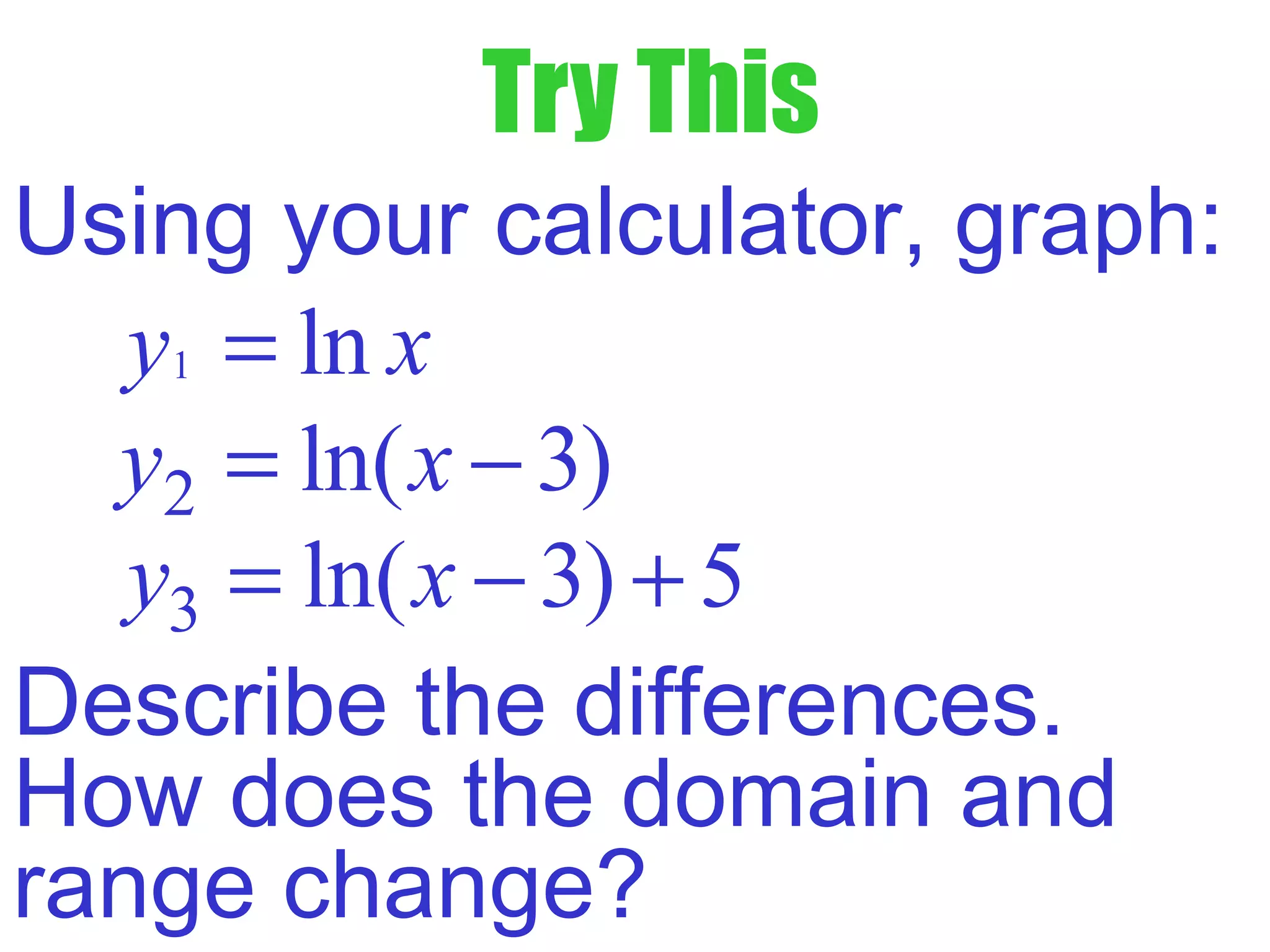
- The natural logarithm ln(x) is the logarithm with base e, where e is an important mathematical constant approximately equal to 2.718.
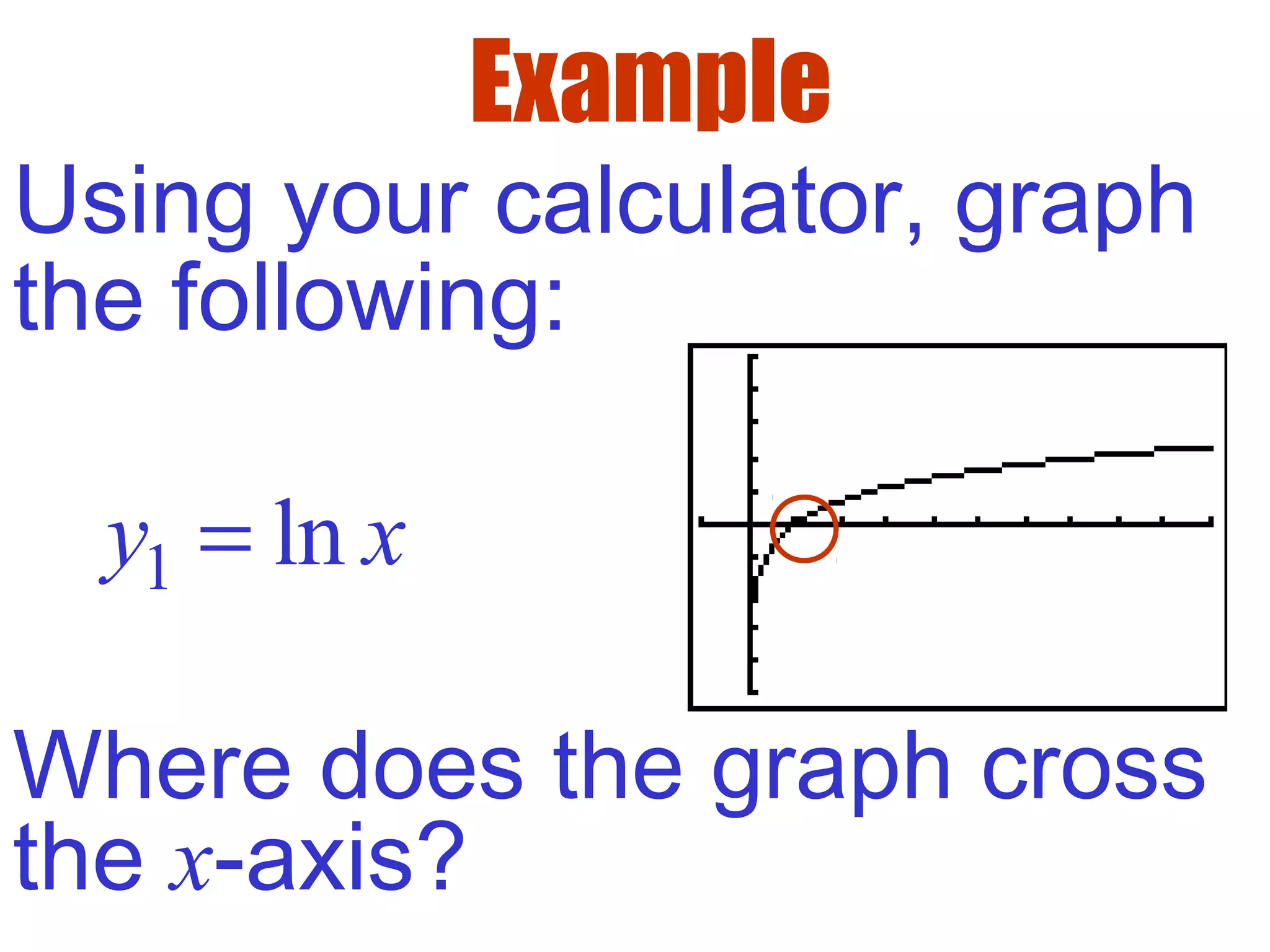
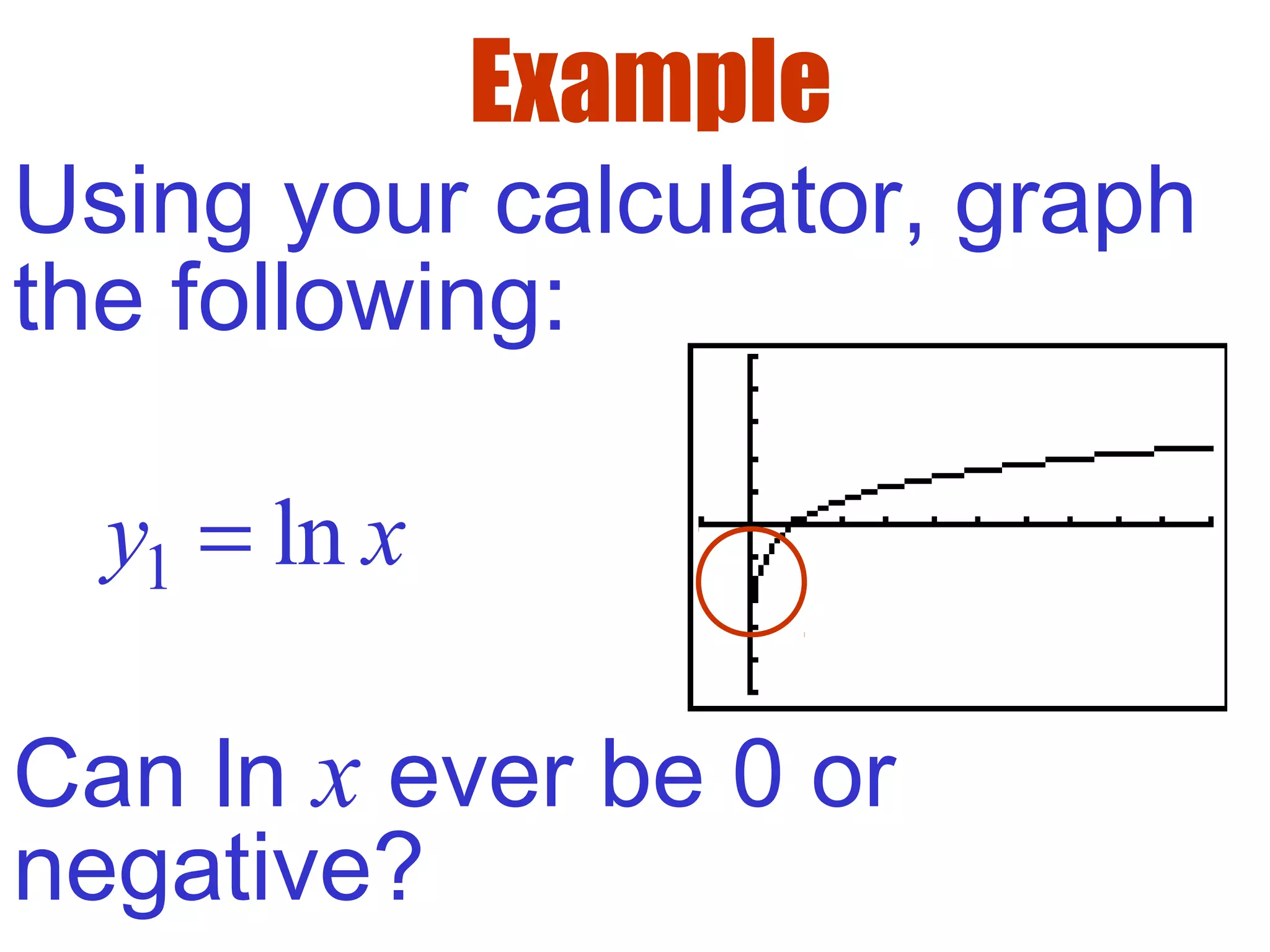
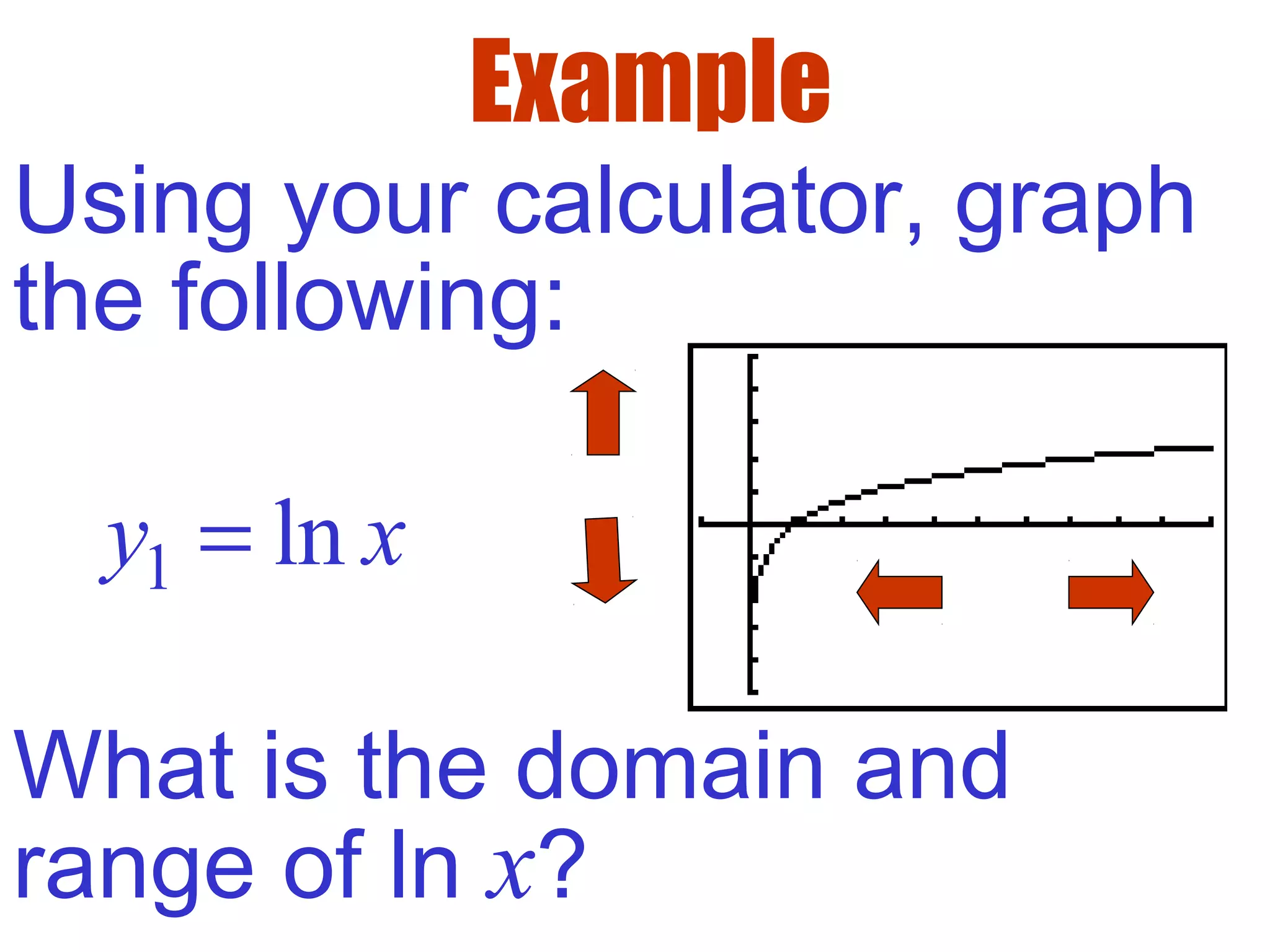
- The domain of ln(x) is x > 0, since it is undefined for non-positive values. The range extends from -∞ to ∞.