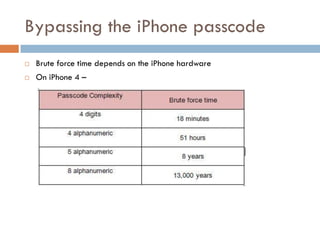
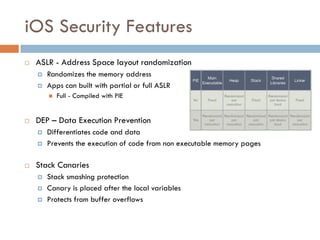
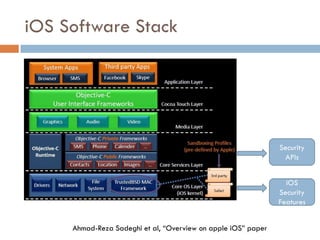
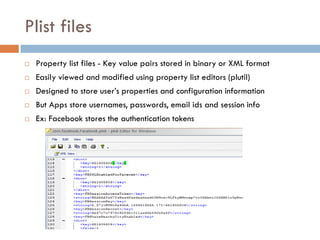
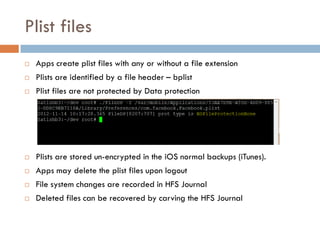
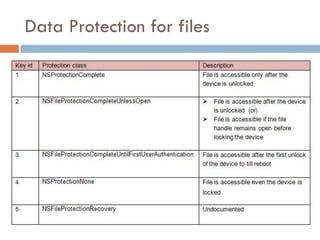
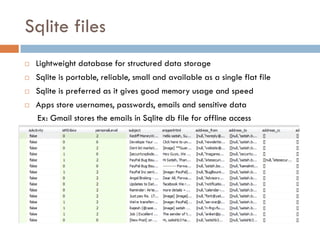
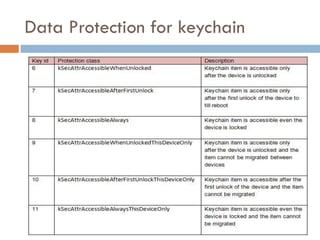
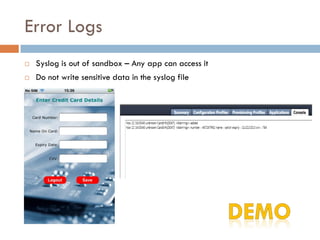
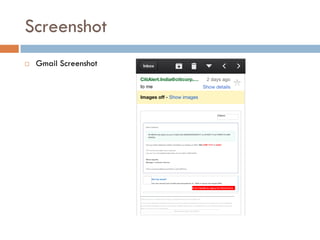
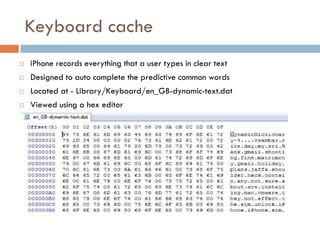
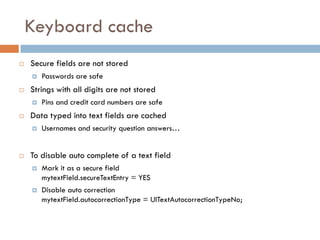
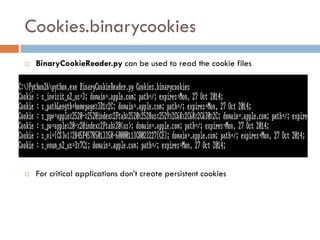
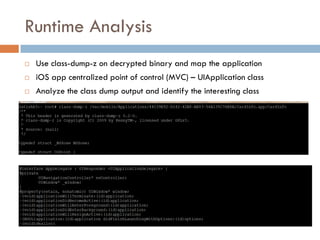
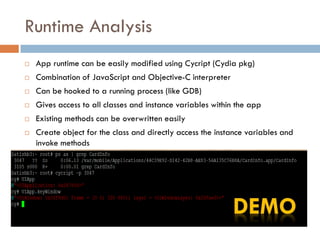
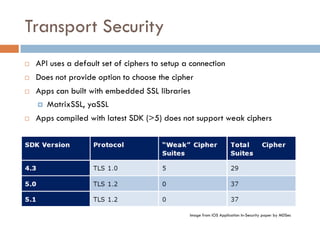
This document provides an overview of iOS security concepts and loopholes, and how they can be exploited to hack iOS applications or steal user data. It discusses various local storage mechanisms like plist files, SQLite databases, and the keychain that applications use, and how unencrypted or poorly secured data stored in these locations could potentially be compromised. It also covers other issues like screenshot caching, error logs, and the keyboard cache that could potentially leak sensitive data. Strategies for developing more secure applications to avoid such issues are also presented.