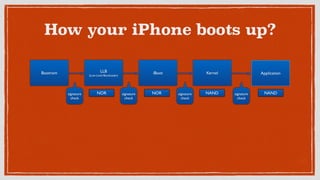
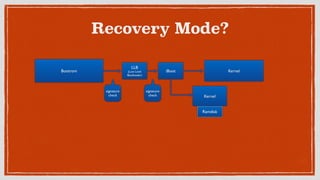
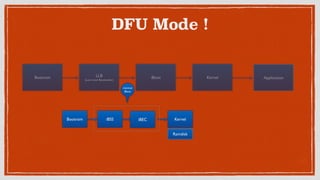
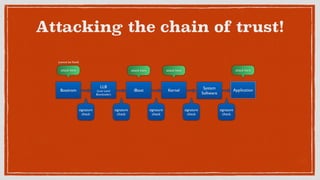
This document discusses security issues and vulnerabilities in the iOS operating system. It begins with an overview of the iOS hardware and software architecture, including the security features like sandboxing and code signing. It then explains what a jailbreak is and how it attacks the chain of trust to bypass these protections. The document outlines several ways sensitive data can be accessed, such as through property lists, SQLite databases, keychains, logs, and cached files. It also discusses client-side vulnerabilities like SQL injection, XSS, and logging of sensitive information. Finally, it promotes learning about mobile security through tools like OWASP iGoat and the speaker's company AppKnox.




![NSLog [@“Agenda”];
Quick overview of iPhone iOS Platform.
iOS Security Structure
What is a Jailbreak?
iOS App (IN)Securities](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-5-320.jpg)



![***[Sandboxing]***
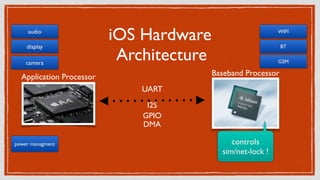
NAND Flash
FTL: converts logical partition to NAND flash architecture
looks like BLOCK device
System Partition / (Read Only)
User Partition /private/var
NAND
FTL
Block Device
/ (RO)
(System Partition)
/private/var (RW)
(User Partition)](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-10-320.jpg)
![***[Sandboxing]***
3rd Party lives only on User Partition
Apps run as mobile user
Kernel Signature checks executables
in system-call execve()
%{ How did you Jailbreak it? }%
NAND
FTL
Block Device
/ (RO)
(System Partition)
/private/var (RW)
(User Partition)](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-11-320.jpg)





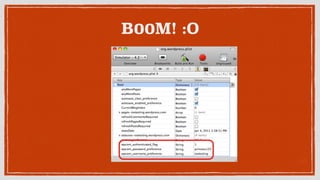




![SQL Injection Client-Side
SQL injection is a problem on the client side too!
BAD:
NSString *sql = [NSString stringWithFormat:@"SELECT name FROM products
WHERE id = '%@'", id]; const char *query = [sql UTF8String];
GOOD:
const char *sql = "SELECT name FROM products WHERE id = ?";
sqlite3_prepare_v2(database, sql, -1, &sql_statement, NULL);
sqlite3_bind_text(&sql_statement, 1, id, -1, SQLITE_TRANSIENT);](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-30-320.jpg)
![XSS Client-Side
Can occur whenever user controlled Objective C variables populated in to
WebView
stringByEvaluatingJavaScriptFromString
NSString *javascript = [[NSString alloc] initWithFormat:@"var myvar="%@";",
username];
[mywebView stringByEvaluatingJavaScriptFromString:javascript];](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-31-320.jpg)
![Vulnerable Obj-C Methods
NSLog()
[NSString stringWithFormat:]
[NSString initWithFormat:]
[NSMutableString appendFormat:]
[NSAlert informativeTextWithFormat:]
[NSPredicate predicateWithFormat:]
[NSException format:]
NSRunAlertPanel](https://image.slidesharecdn.com/pluggedin71-140612041433-phpapp02/85/iOS-Vulner-ability-32-320.jpg)