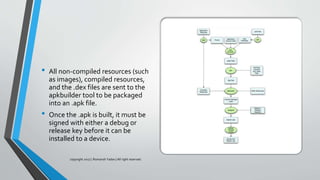
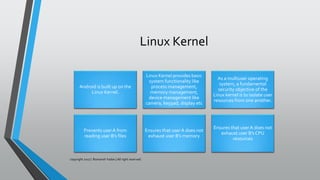
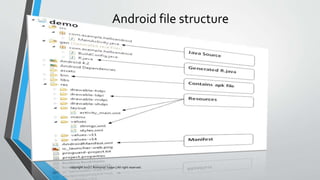
The document discusses mobile security, specifically focusing on Android apps and penetration testing methods. It outlines the importance of mobile application security testing to identify vulnerabilities and threats, alongside the frameworks and tools available for testing. Additionally, it covers Android architecture, data handling, and common security vulnerabilities categorized by the OWASP Top 10 for mobile security.