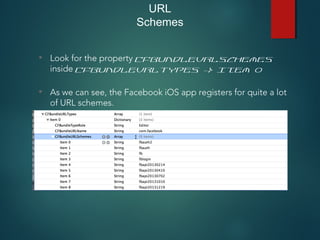
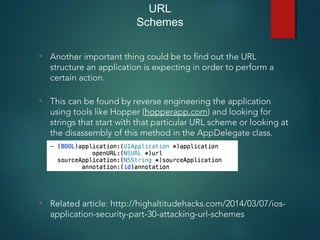
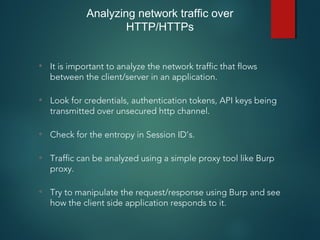
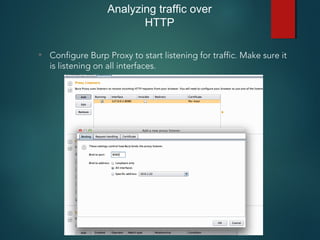
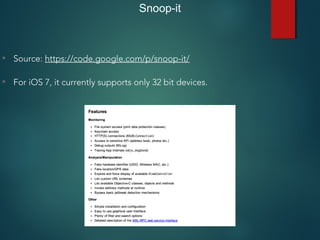
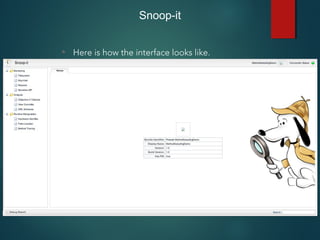
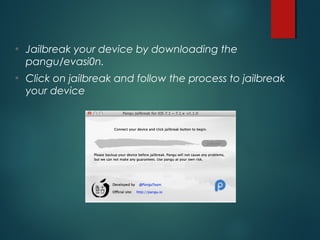
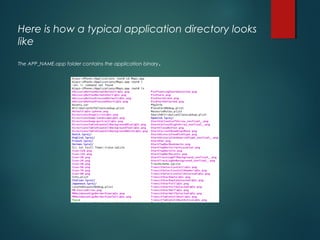
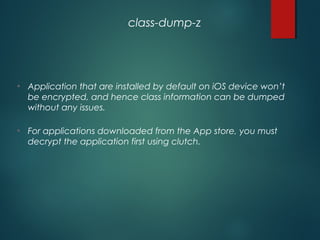
This document provides an overview of setting up an iOS penetration testing environment and common techniques for analyzing iOS applications. It discusses jailbreaking a device and installing useful tools. It also covers understanding the iOS file system and Objective-C runtime, using tools like Cycript and class-dump-z to enable runtime analysis and manipulation. The document describes insecure data storage techniques like plist files, NSUserDefaults, and CoreData that store unencrypted data. It also discusses analyzing network traffic and automated testing.






![Usage: otool -l [binaryName]](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-9-320.jpg)

![Usage: class-dump-z [binaryName]](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-12-320.jpg)
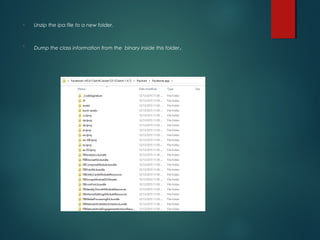
![Usage: clutch [App Name]
• Just using the clutch command will display a list of applications that can be decrypted.
• Use “clutch [App Name]” to decrypt the application. The decrypted ipa file will be stored in the location as shown below.](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-13-320.jpg)

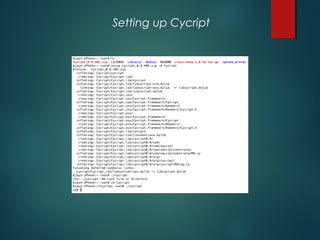
![Runtime analysis using Cycript
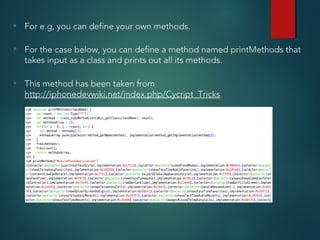
• You can hook into the runtime of an application by using the command
“cycript -p [PID]”
• Some cool things that you can do with Cycript can be found here
http://iphonedevwiki.net/index.php/Cycript_Tricks](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-17-320.jpg)
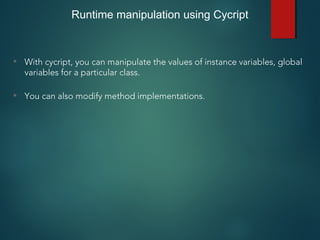
![Runtime manipulation demo
• In this case, we are manipulating the instance variable “urlToLoad” in the
view controller RuntimeManipulationDetailsVC for DamnVulnerableiOSApp
(http://damnvulnerableiosapp.com)
• The first step is to get a reference to the view controller.
• Once you get the reference, you can modify any of it’s variables.
• For e.g
UIApp.keyWindow.rootViewController.topViewController.topViewControlle
r.urlToLoad = [NSString stringWithFormat:@"http://google.com"];](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-21-320.jpg)
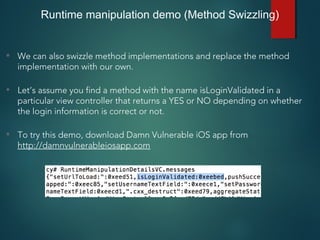
![• We can modify this method’s implementation to always return TRUE.
• As you can see, the code on the R.H.S is actually Javascript, this is the
beauty about Cycript, it can contain both Objective-C and javascript syntax.
Runtime manipulation demo (Method Swizzling)
• RuntimeManipulationDetailsVC.messages['isLoginValidated'] =
function() {return TRUE;}](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-23-320.jpg)
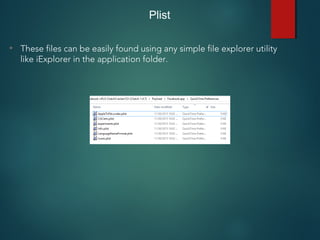
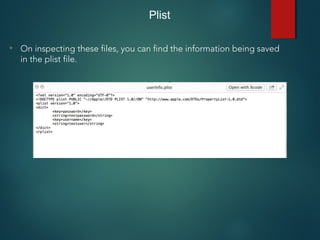
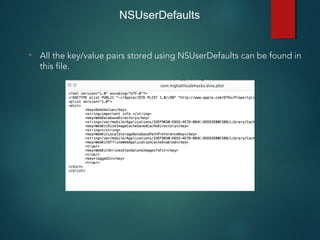
![NSUserDefaults
• Used for storing properties, objects that can persist even after an
application restart.
• Information is saved unencrypted inside the application sandbox in
a plist file with the name [BUNDLE_ID].plist inside the folder
Library -> preferences .
• Developers make a common mistake of storing critical data using
NSUserDefaults.](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-30-320.jpg)
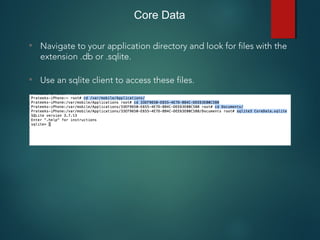
![NSUserDefaults
• All the information stored using NSUserDefaults can be found
inside the file [BUNDLE_ID].plist inside the folder Library ->
Preferences.](https://image.slidesharecdn.com/iosapplicationpentesting-151221082157/85/iOS-Application-Pentesting-31-320.jpg)