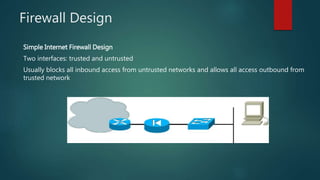
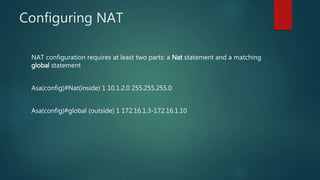
The document outlines the fundamentals of firewalls, including their types, deployment modes, and access control mechanisms. It discusses the evolution of firewalls to include features like VPNs and NAT, and emphasizes the importance of security levels and access control lists (ACLs) in managing network traffic. Additionally, it covers high availability features and the configurations necessary for network address translation (NAT) to function effectively within firewall designs.