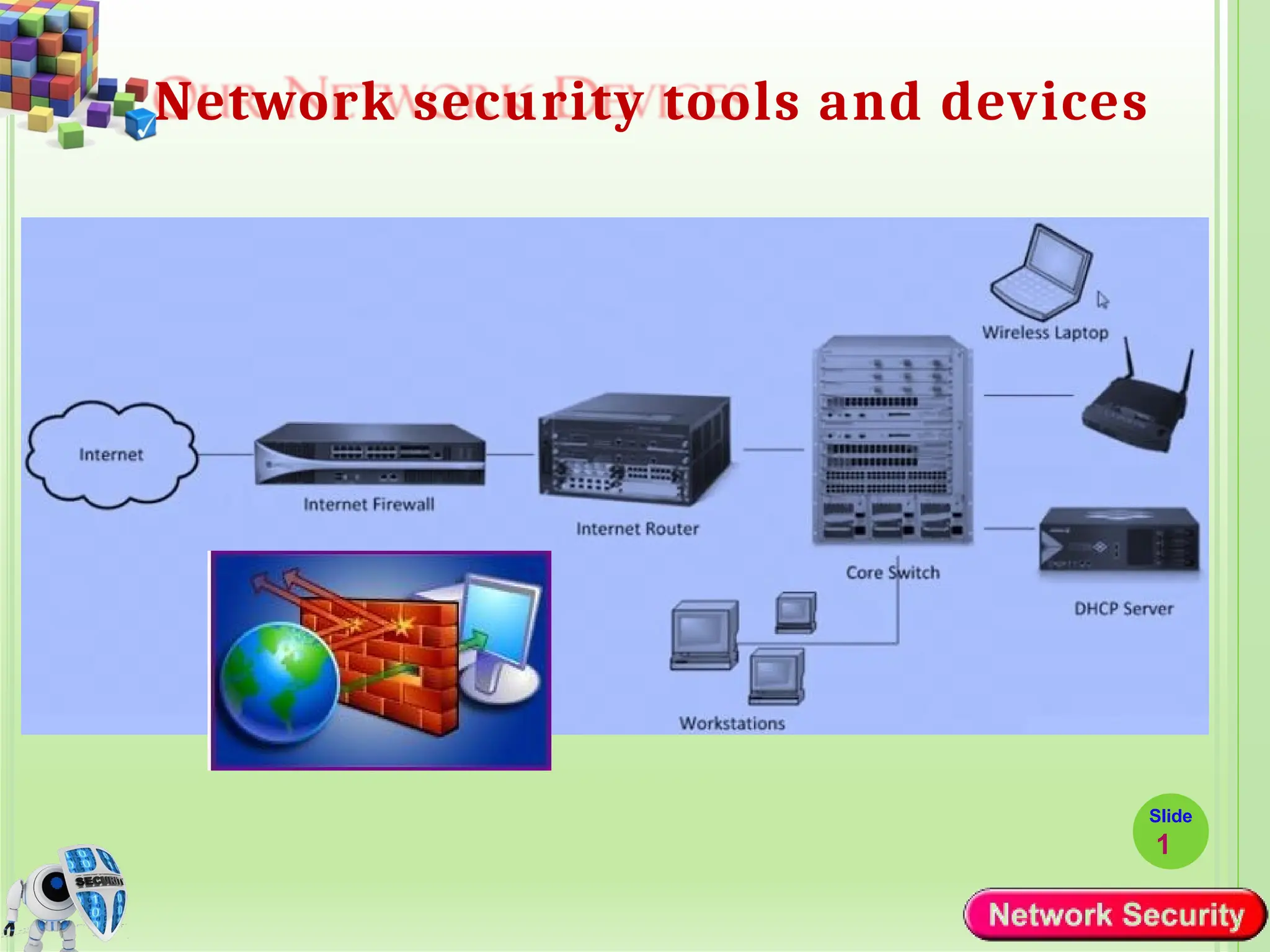
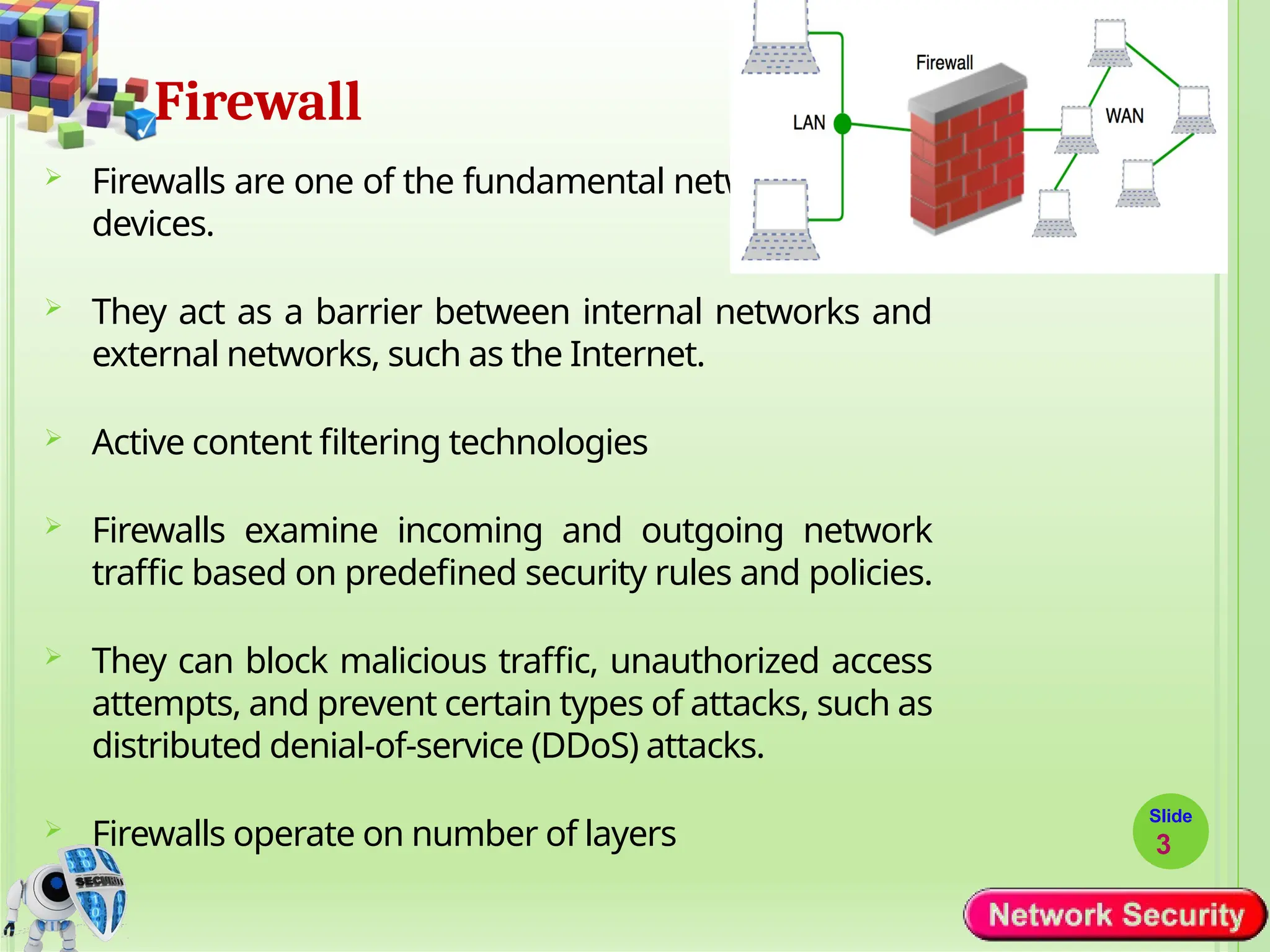
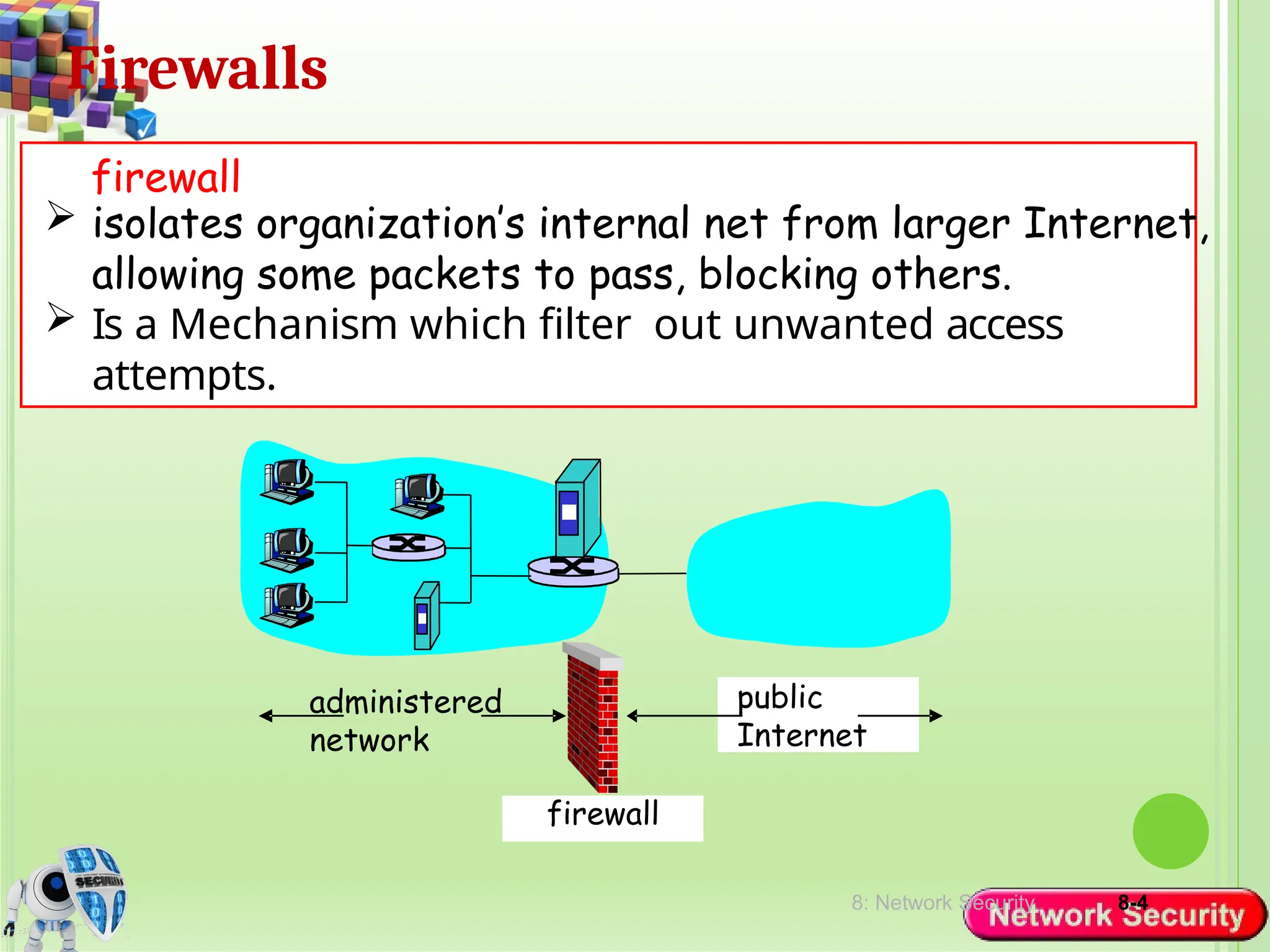
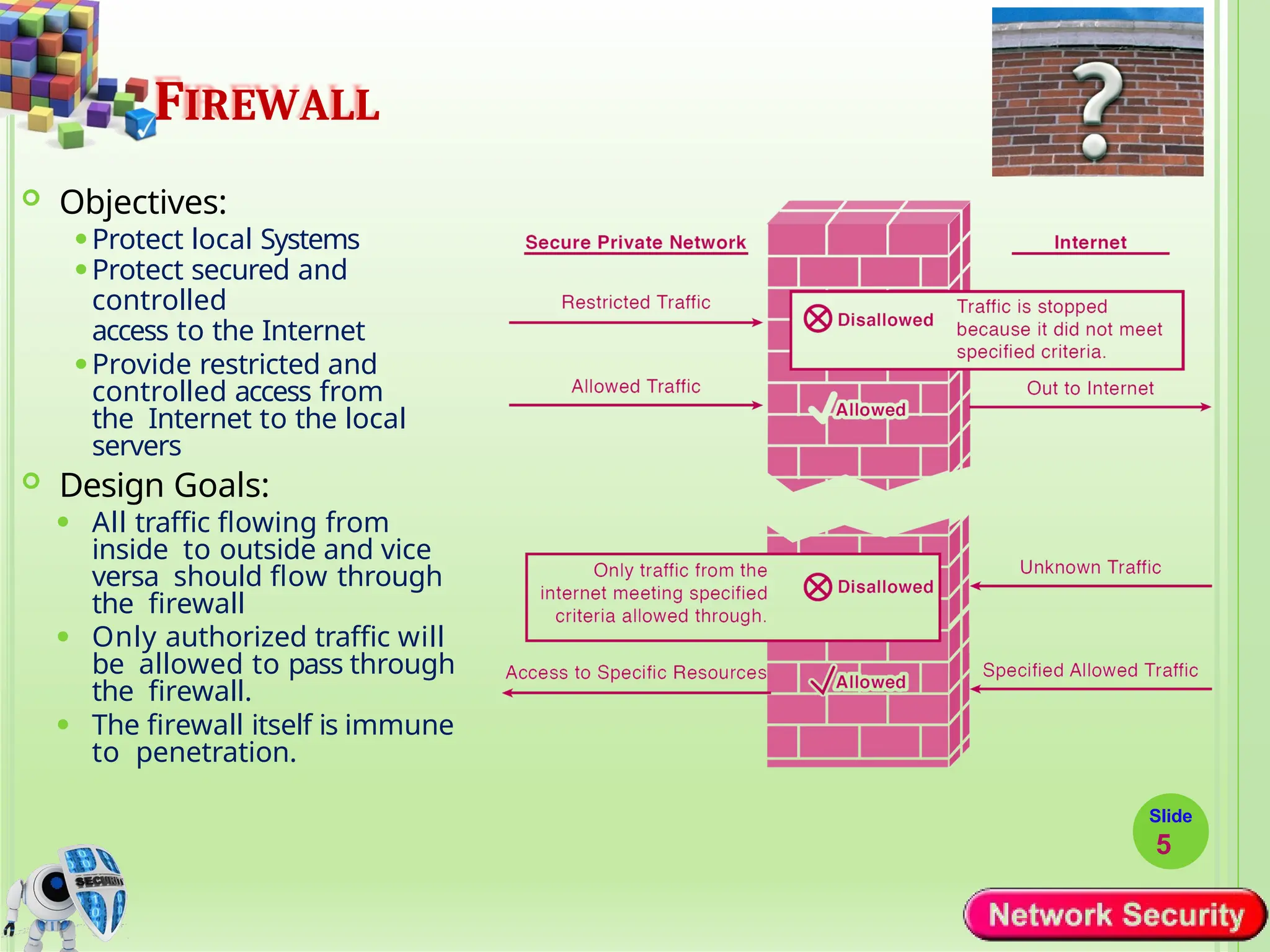
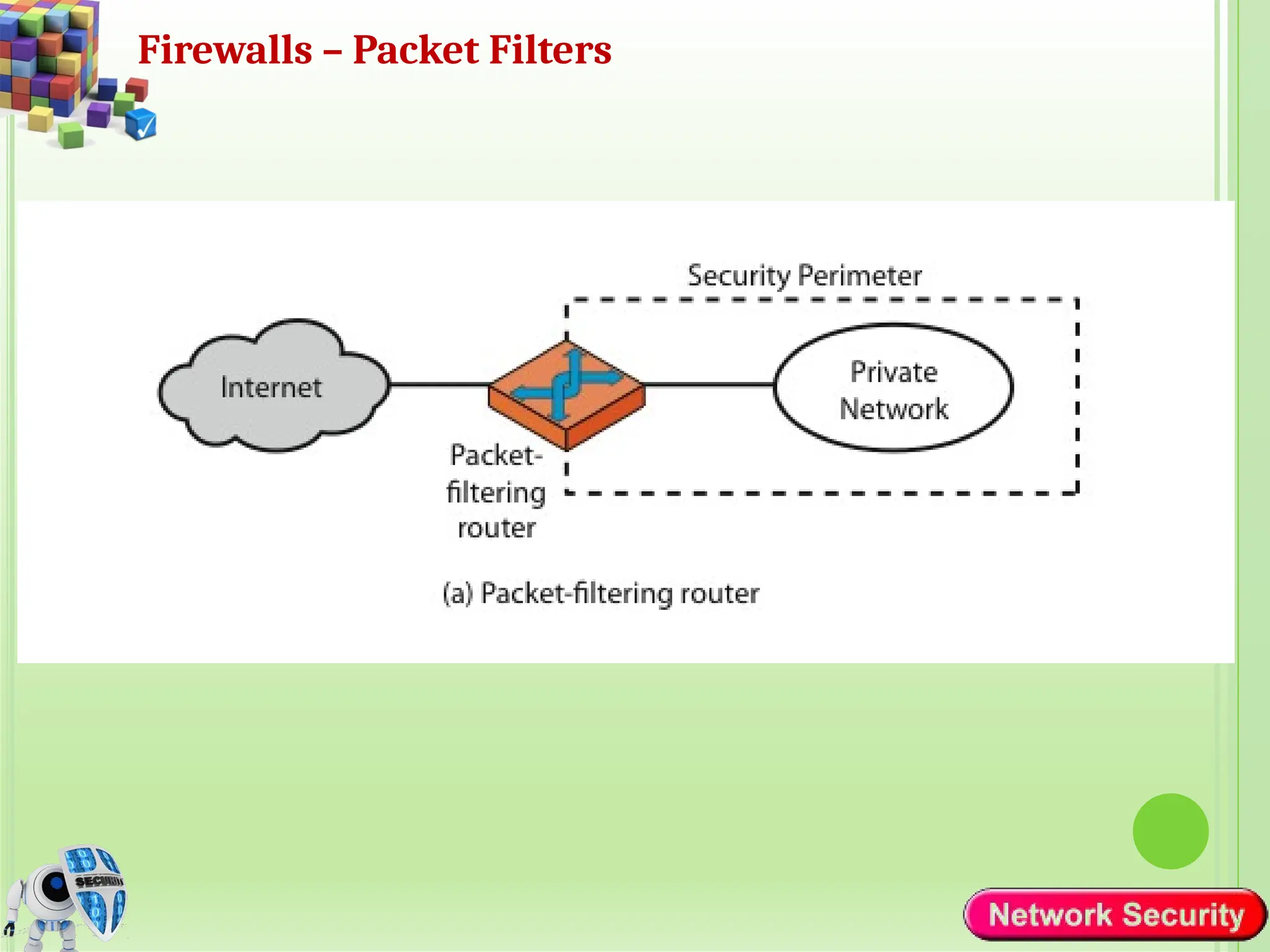
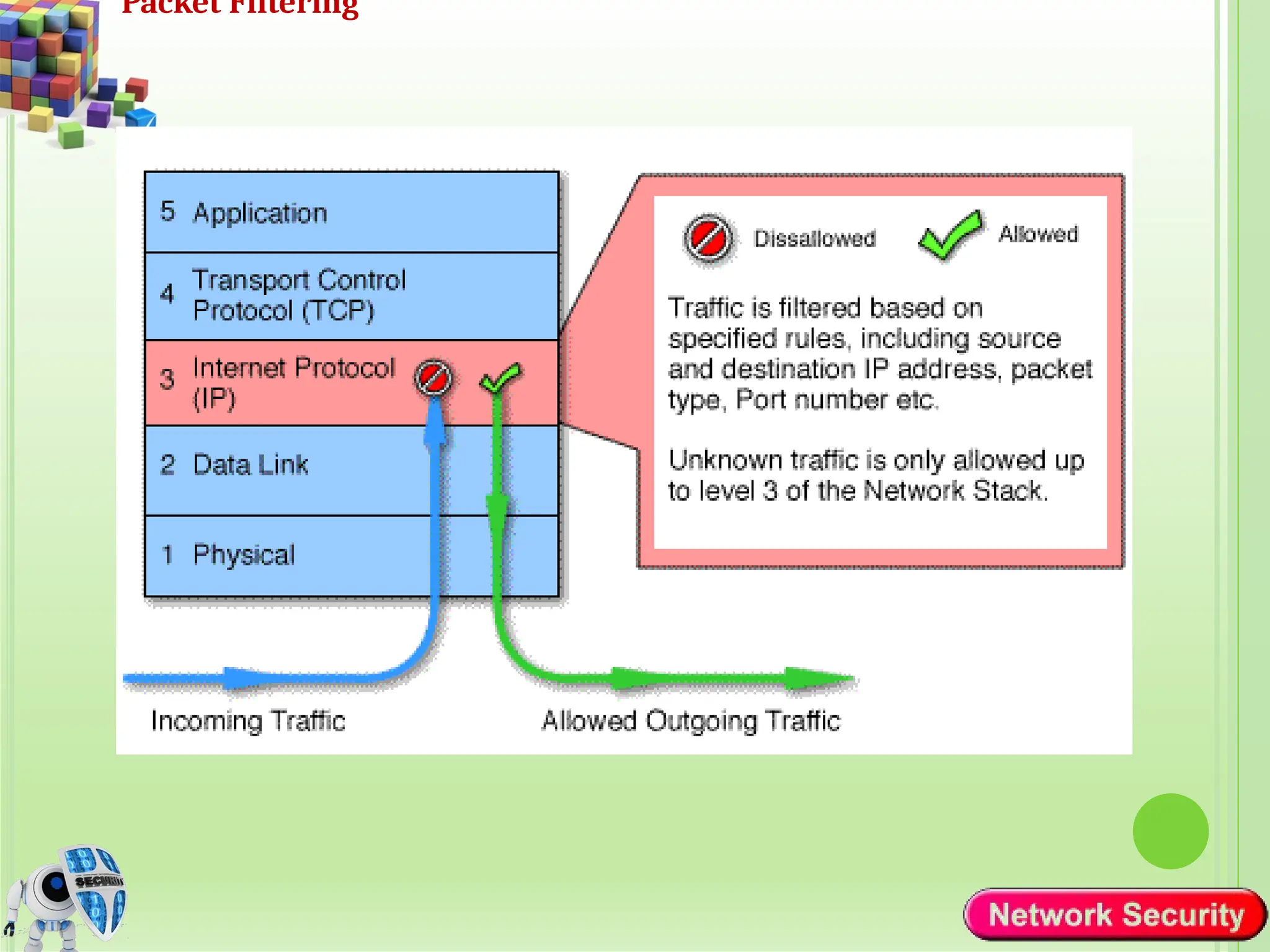
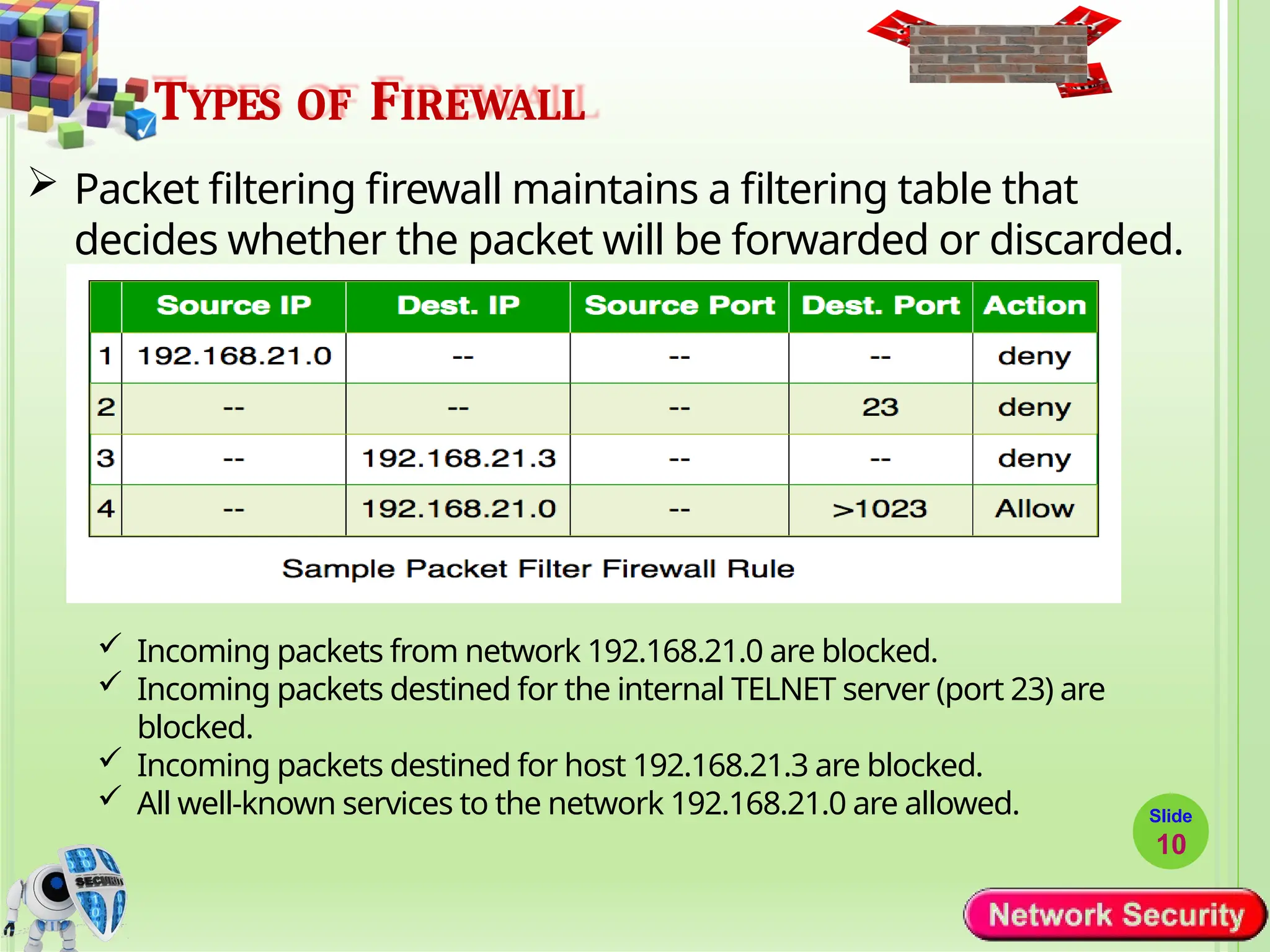
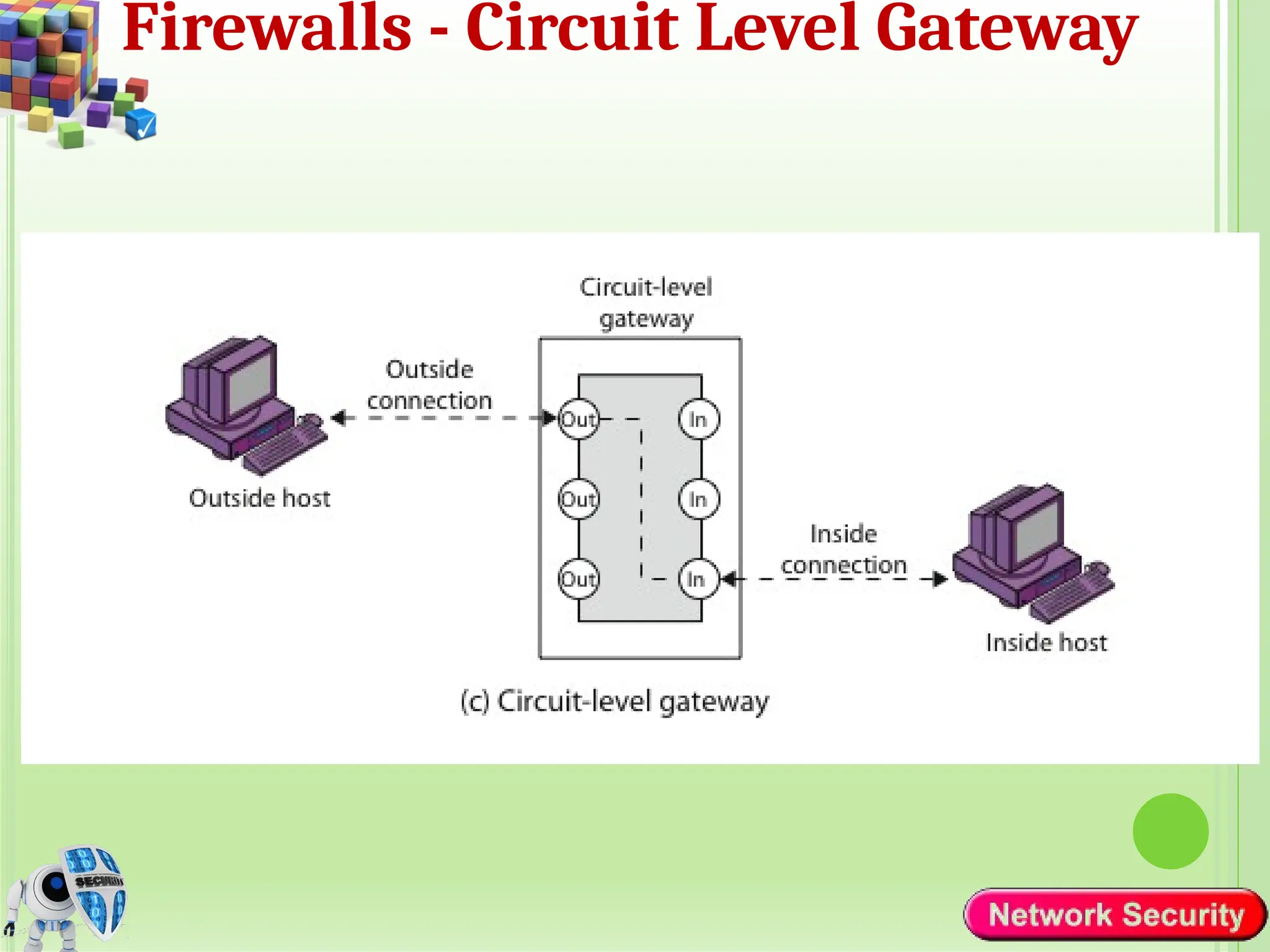
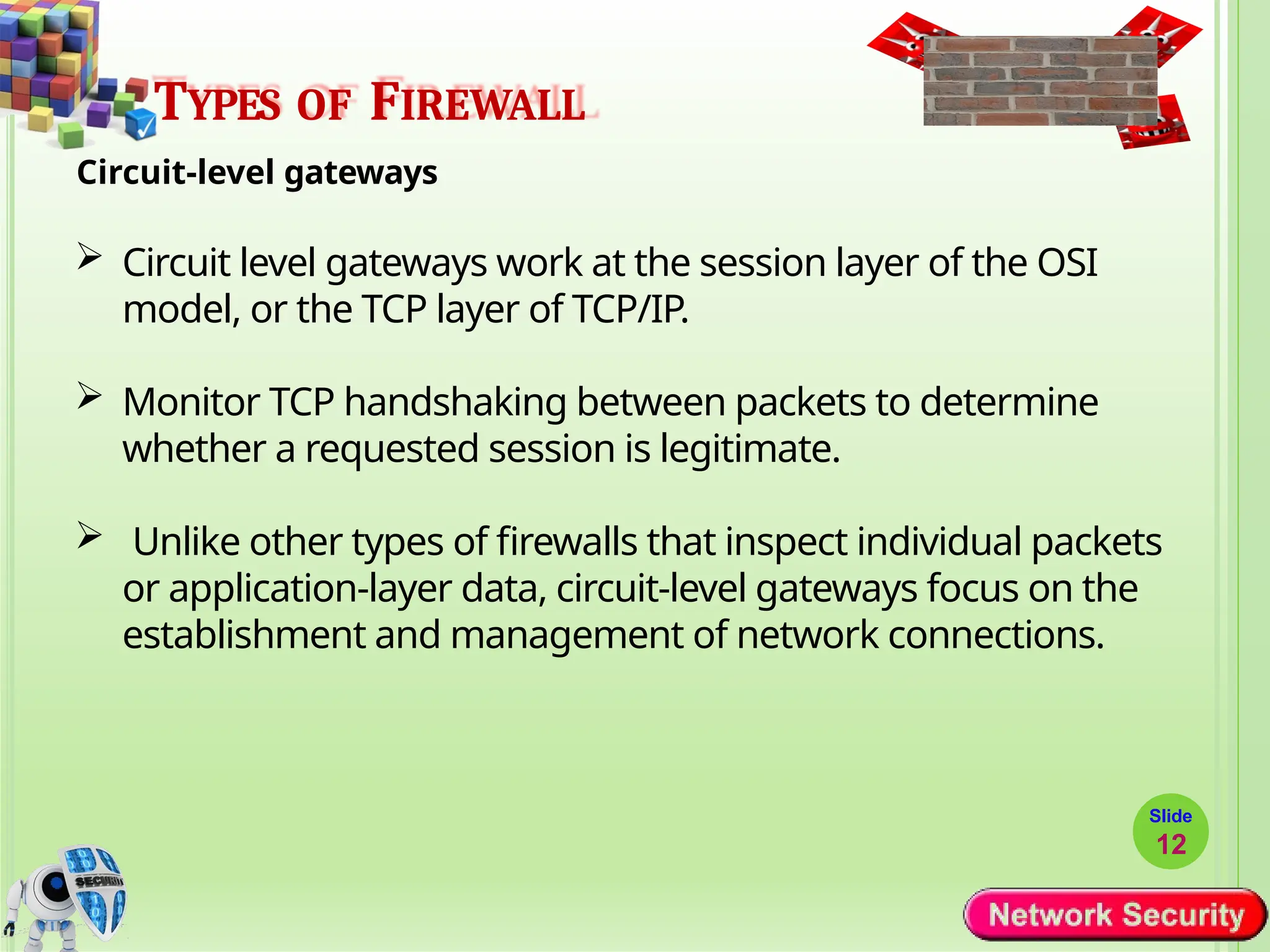
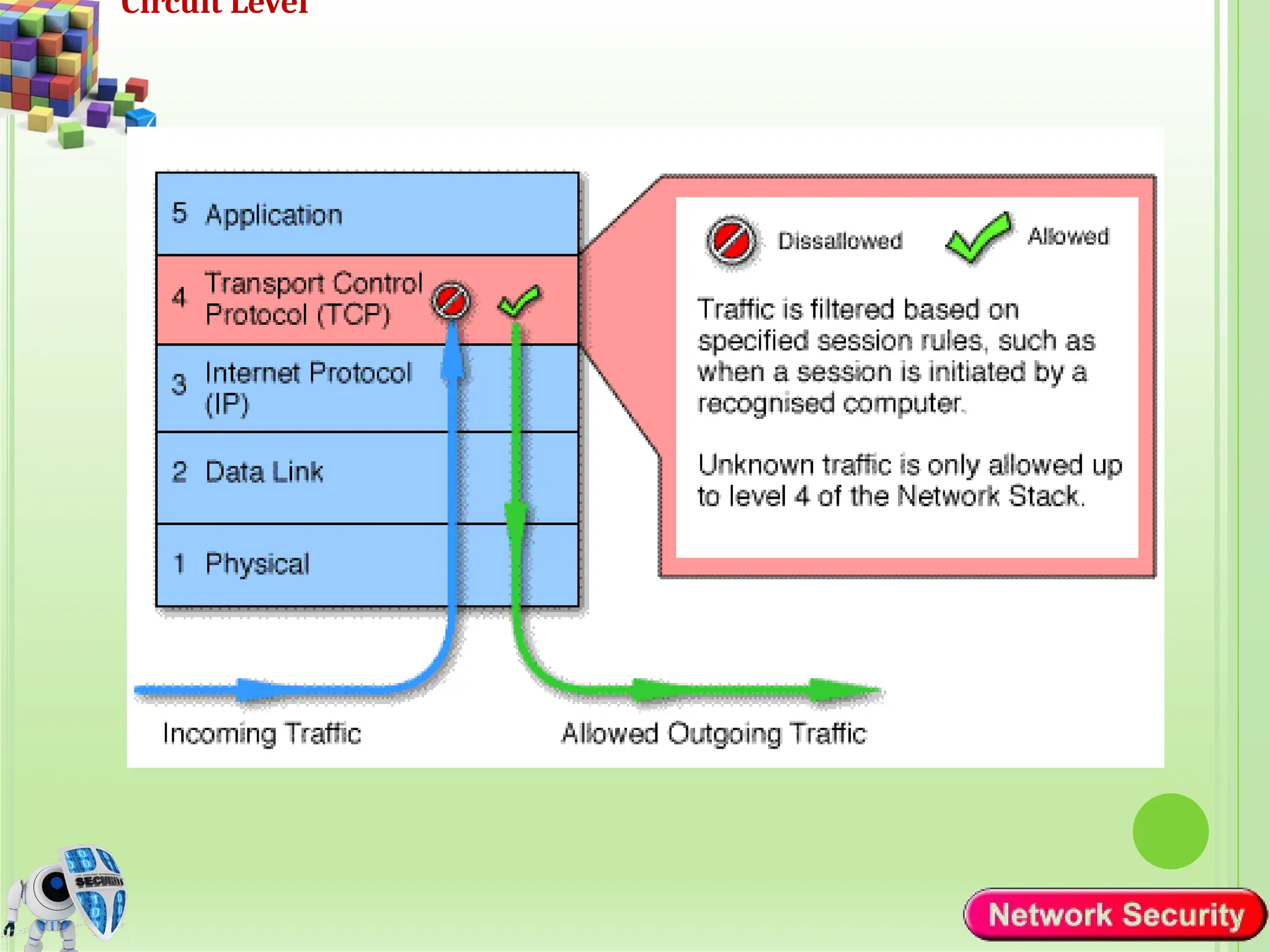
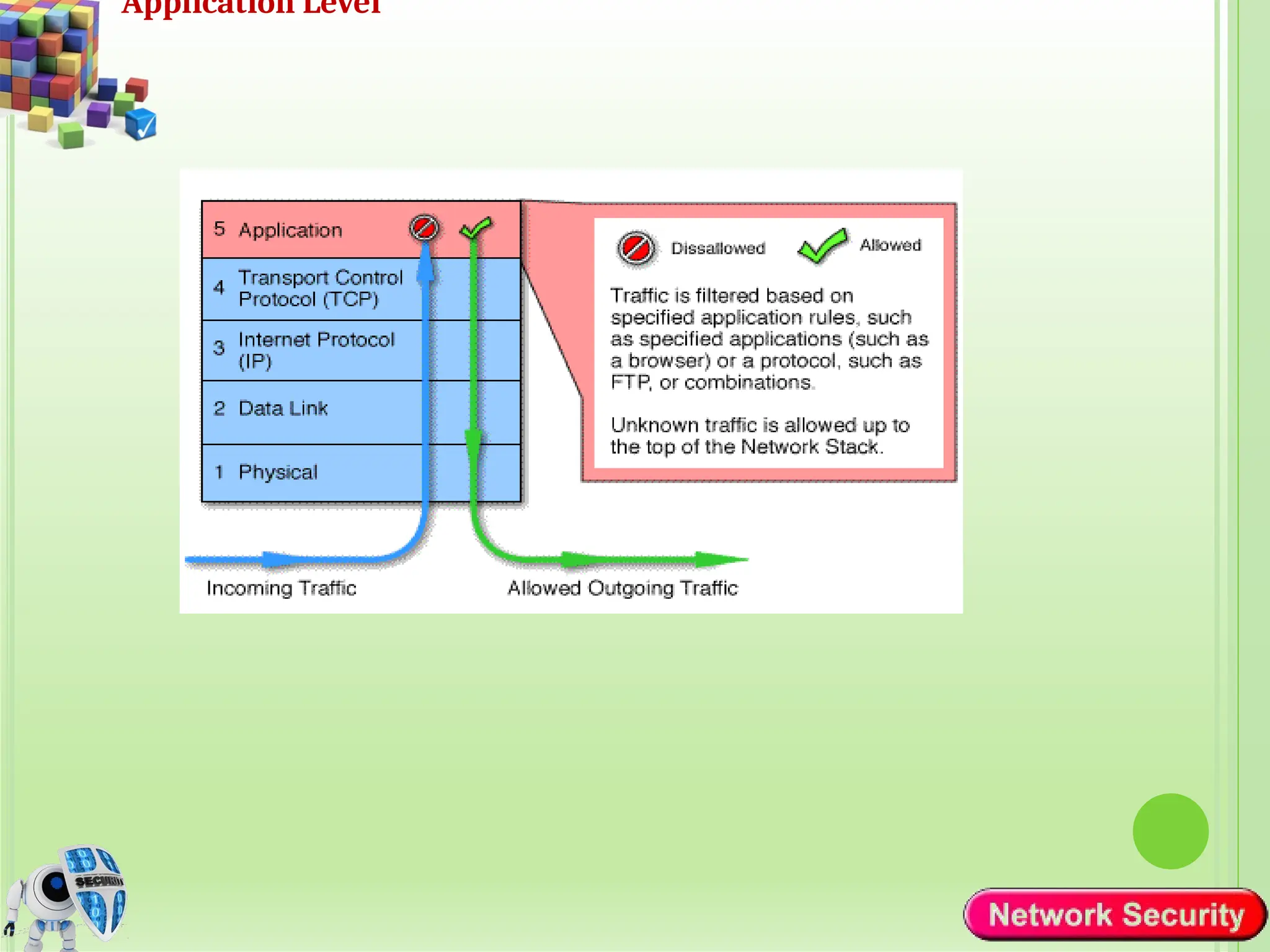
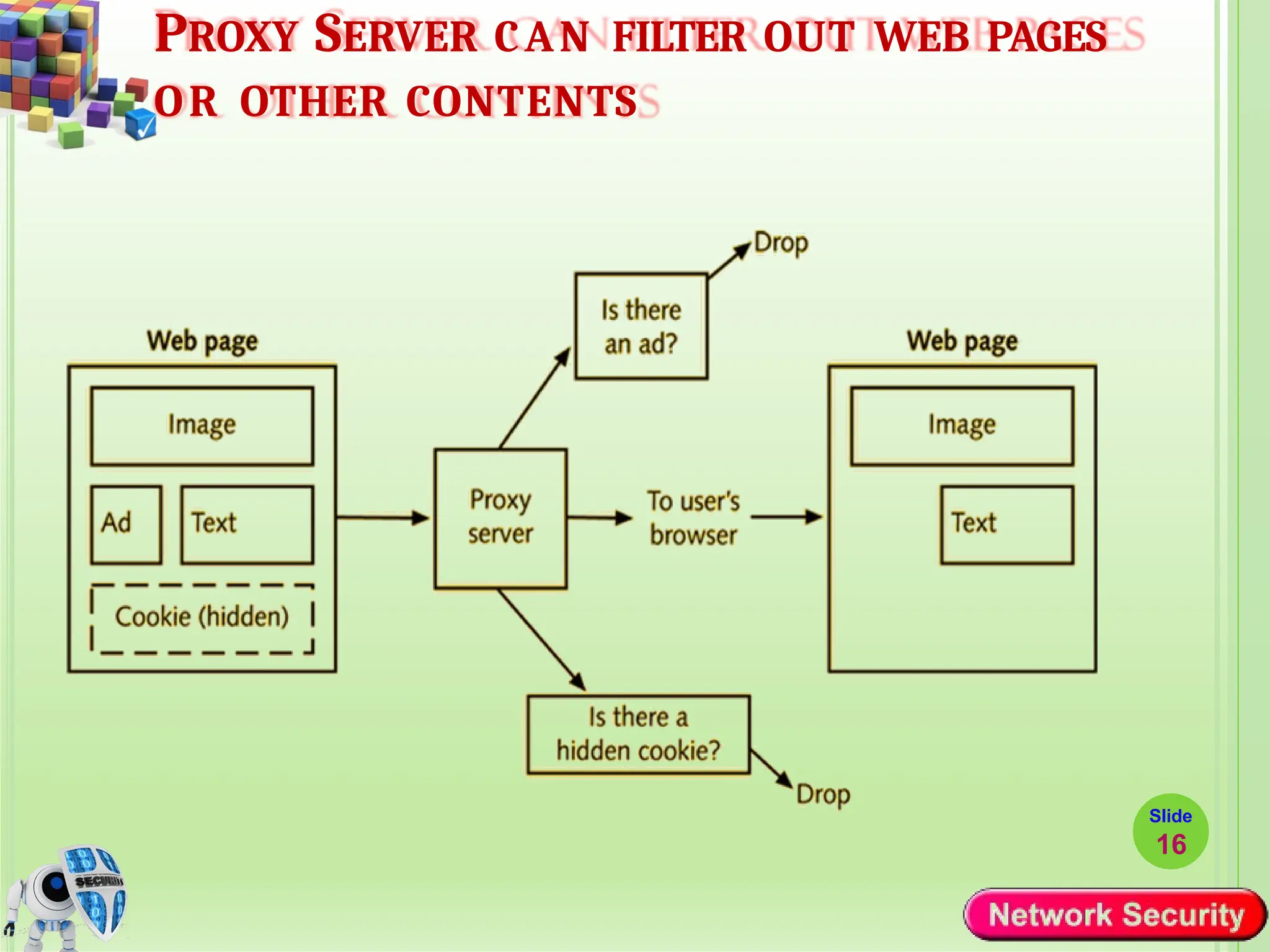
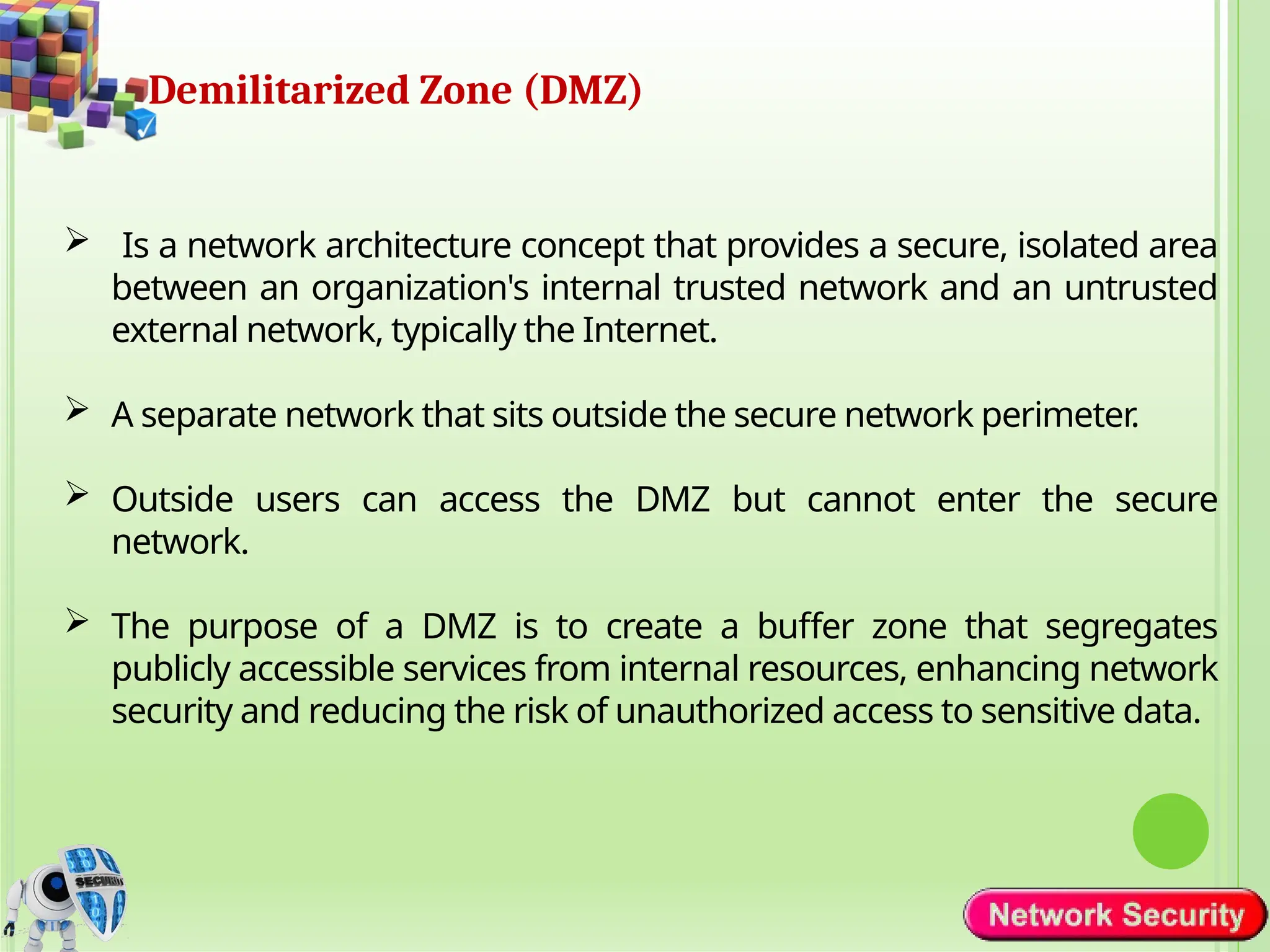
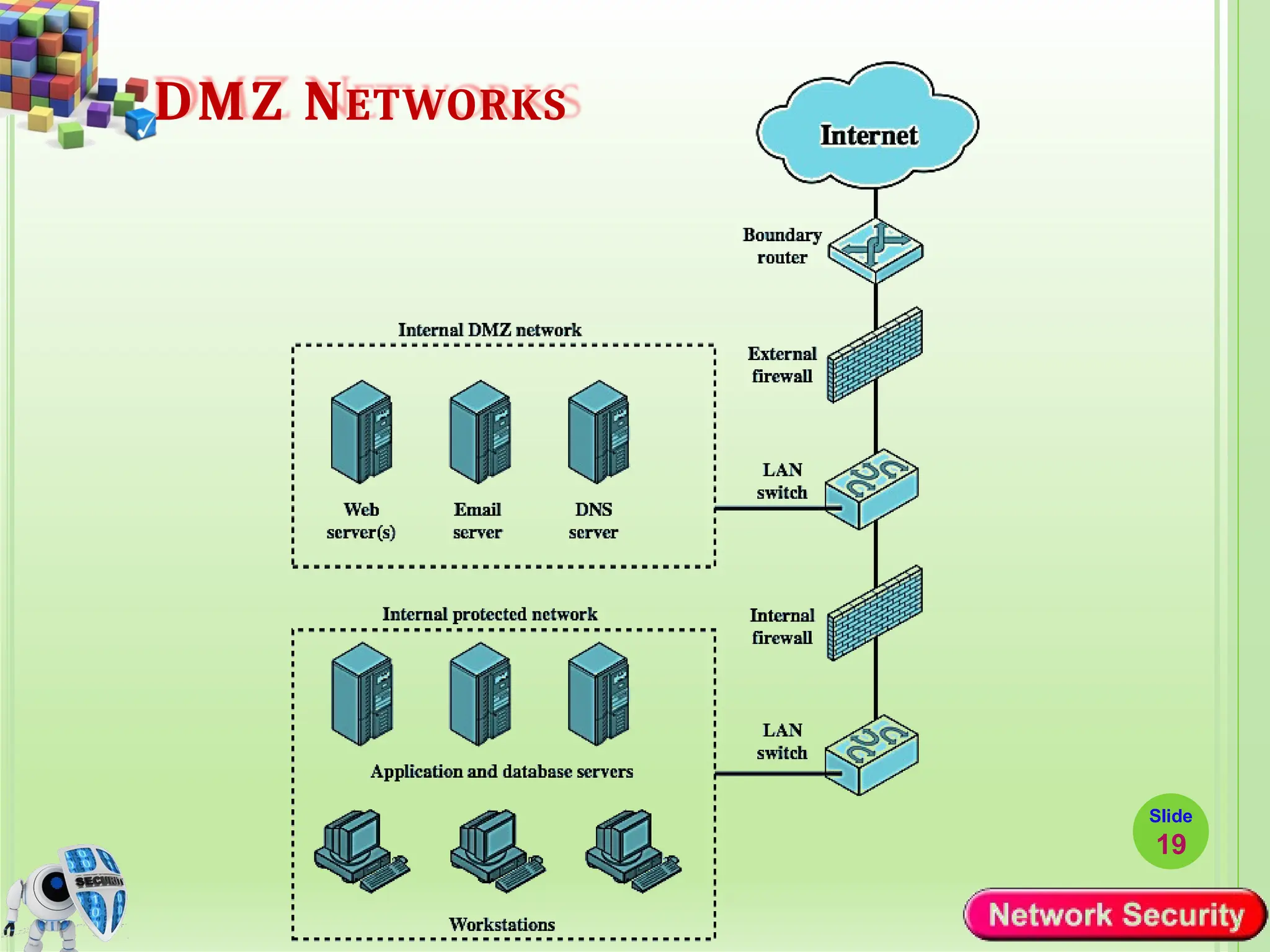
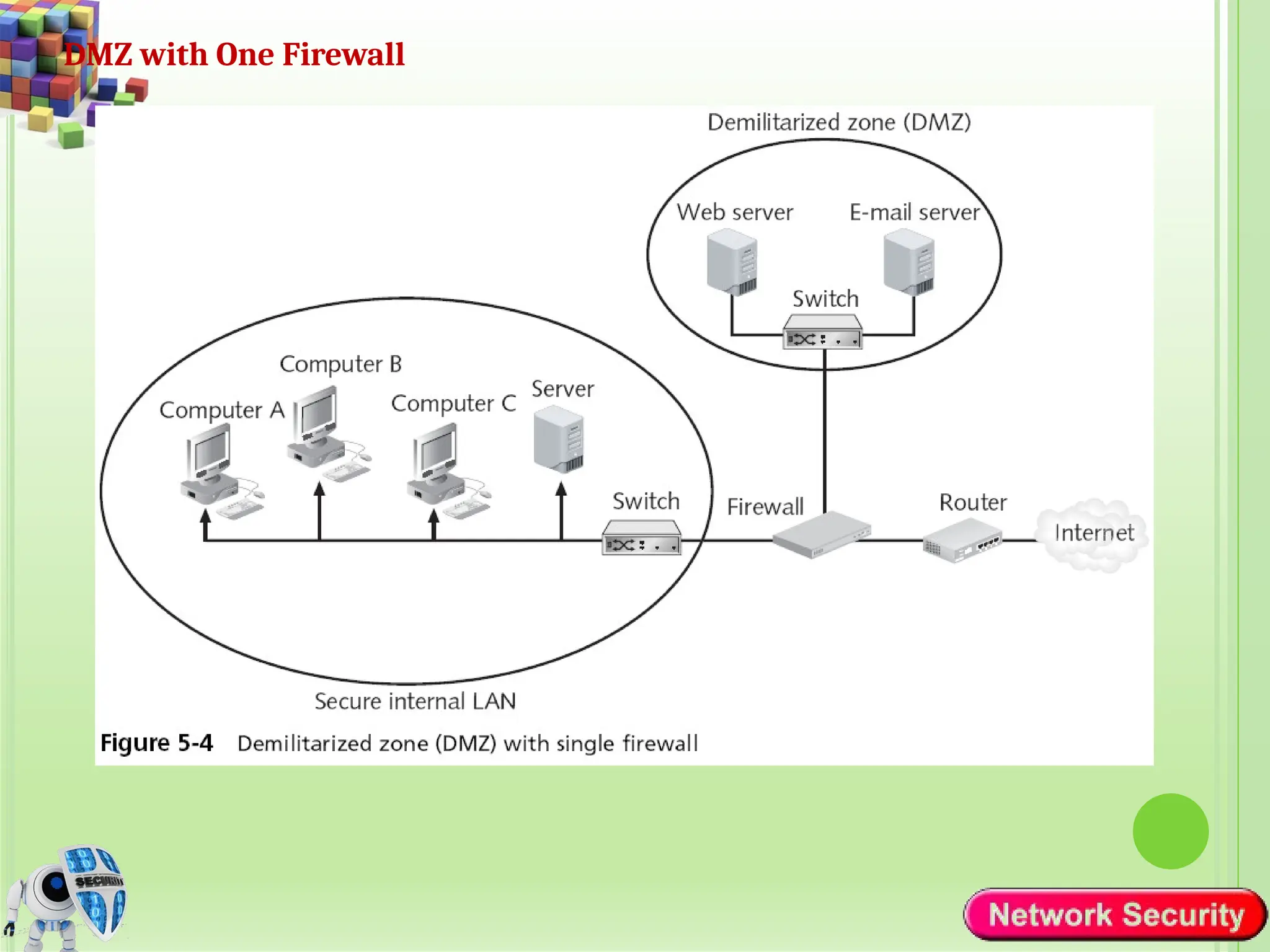
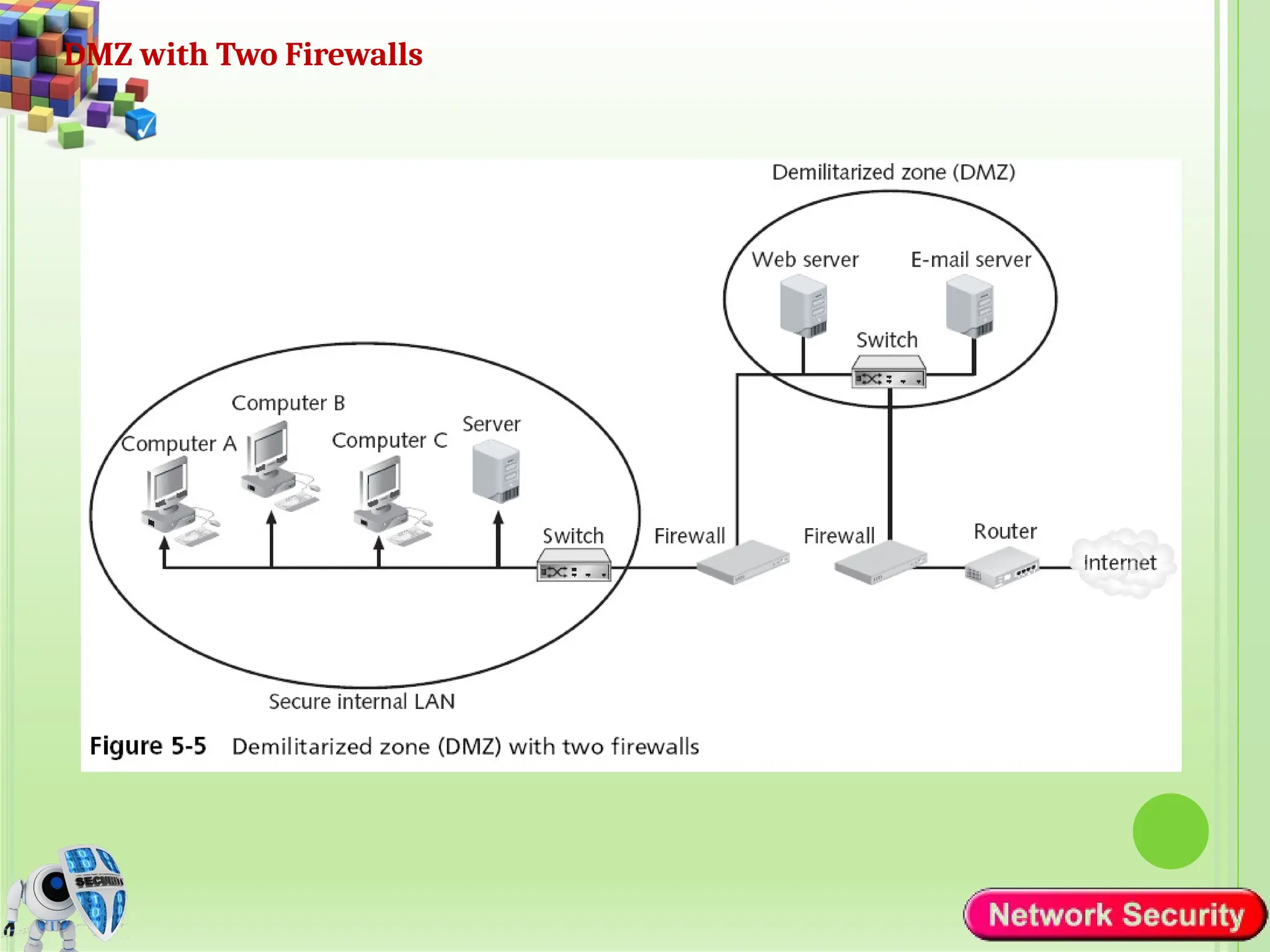
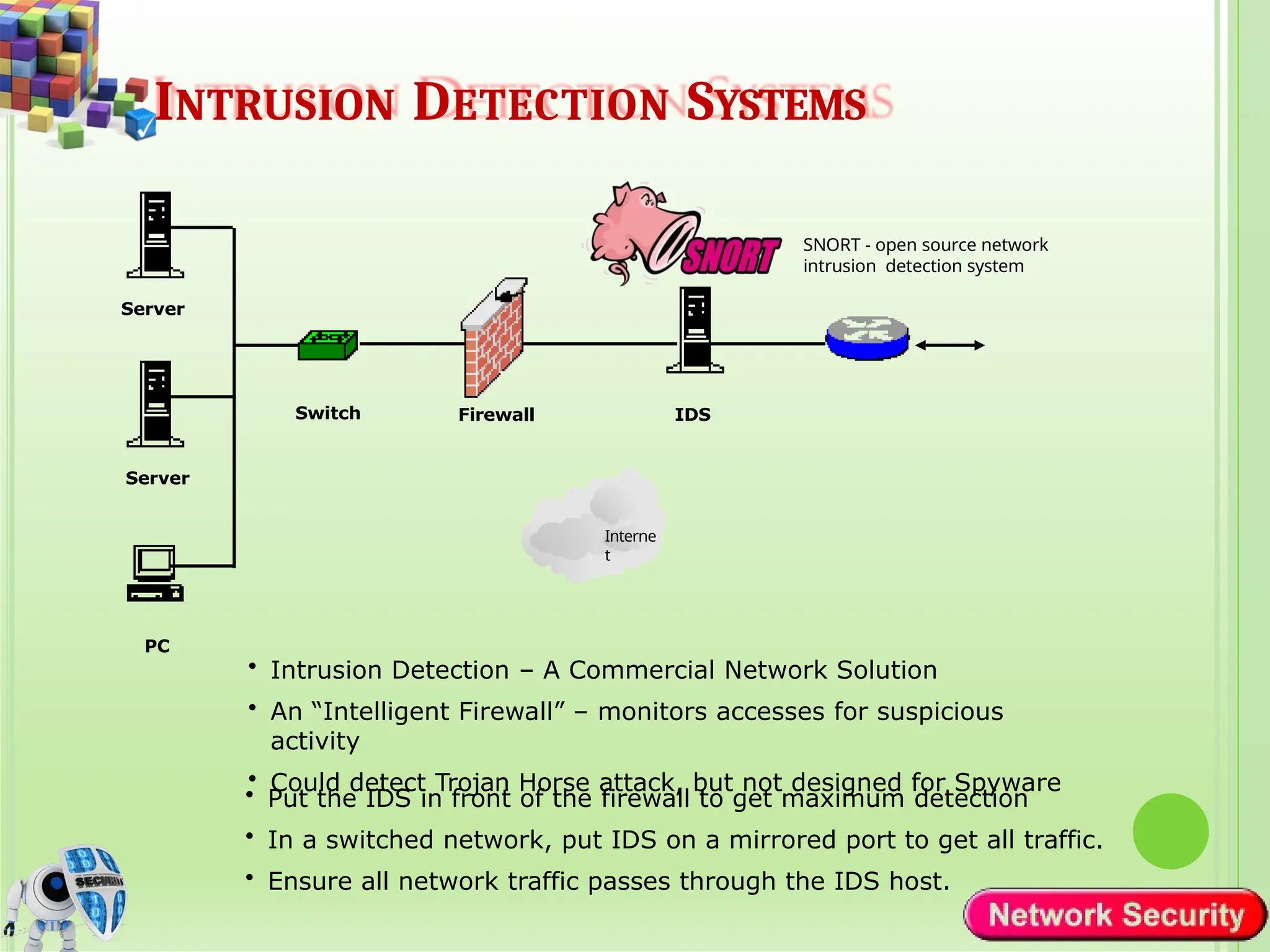
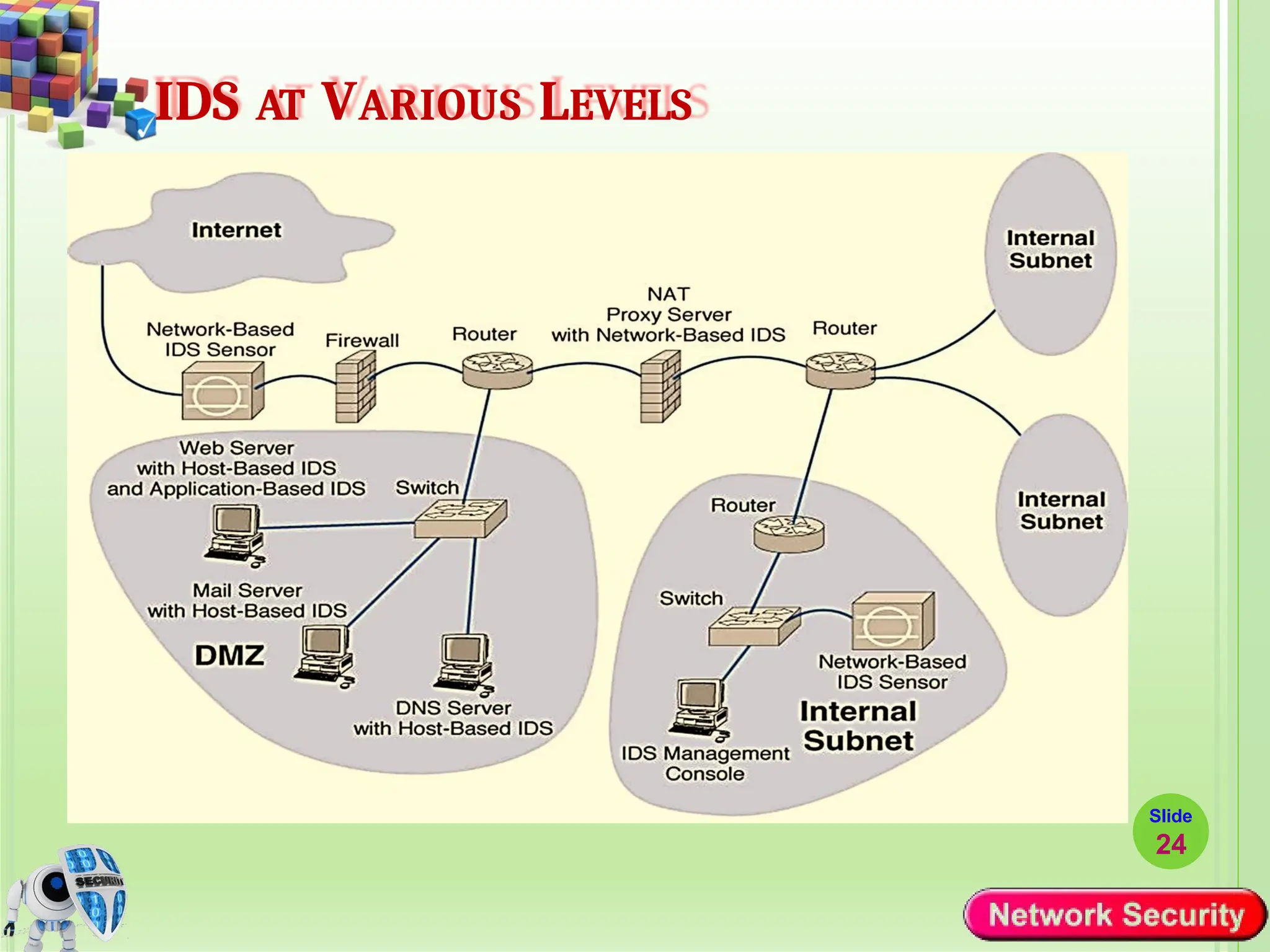
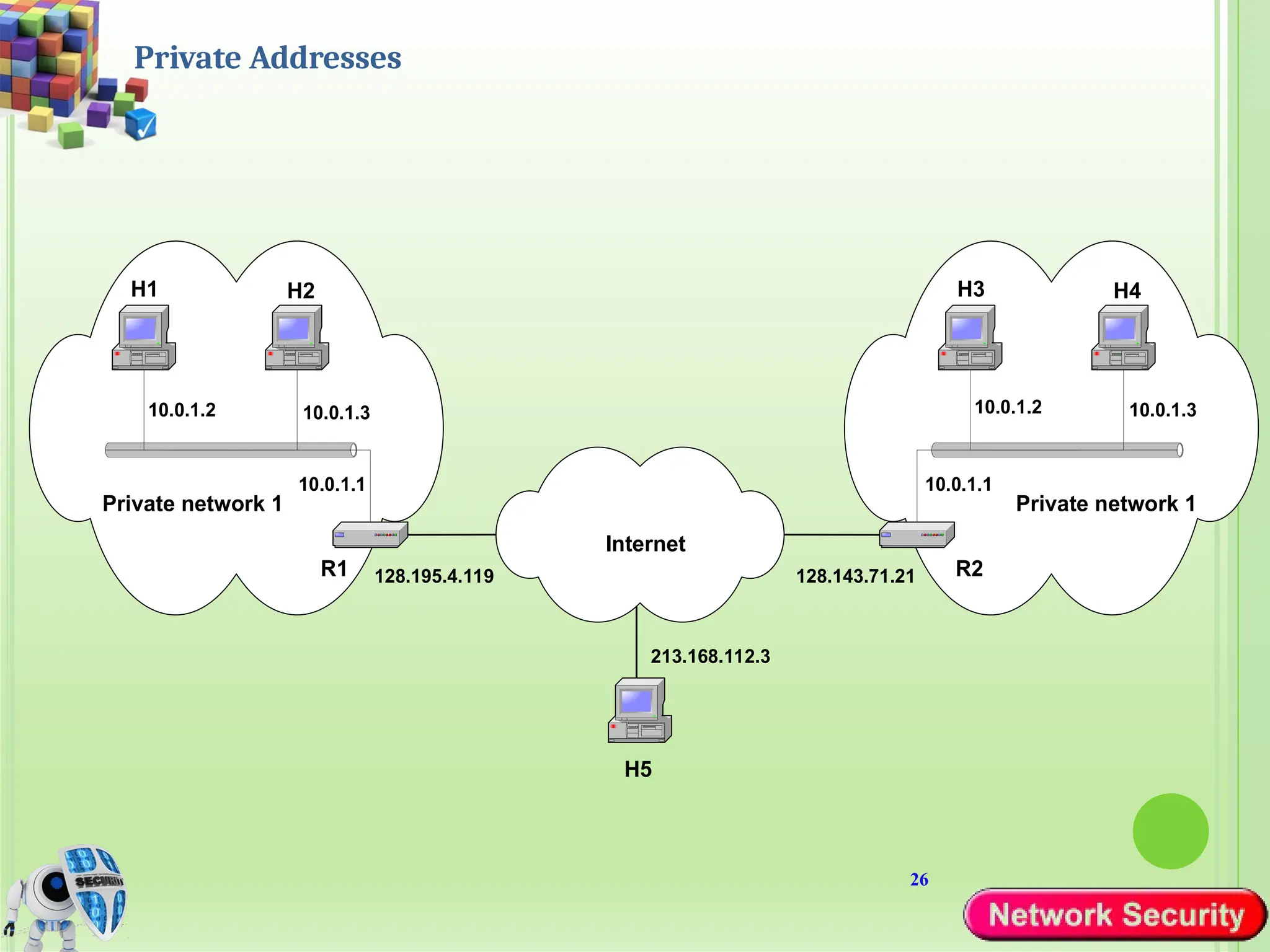
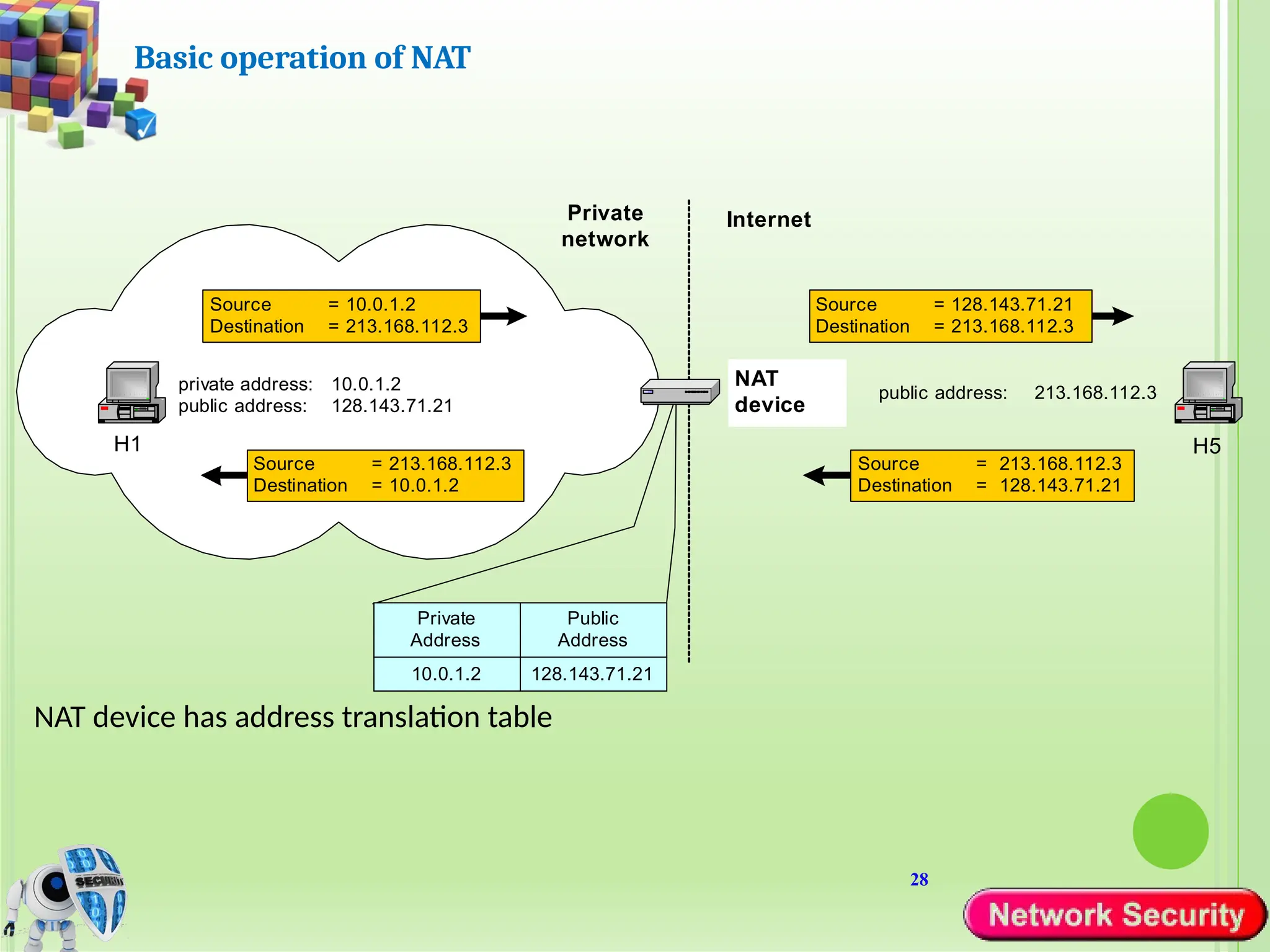
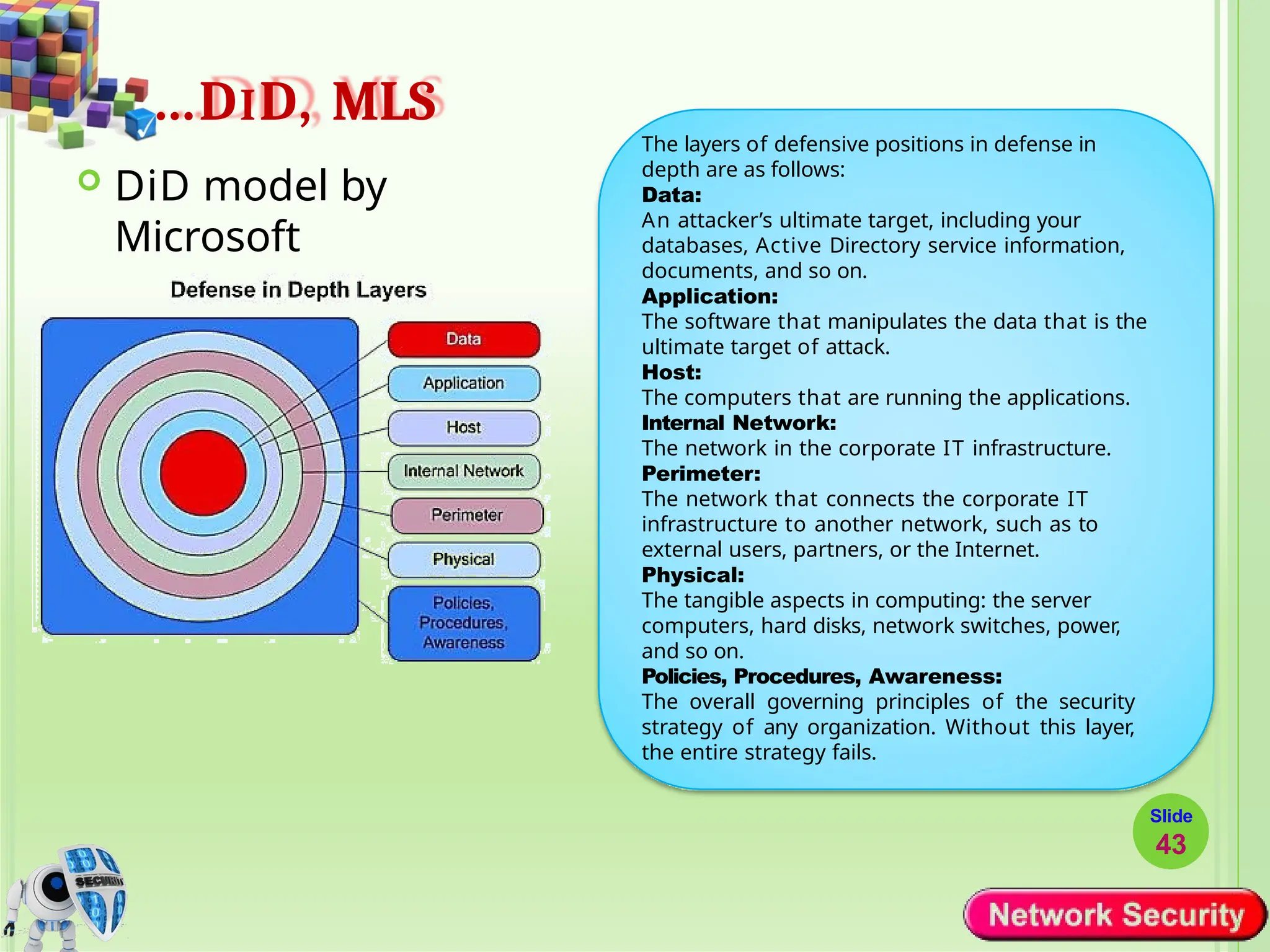
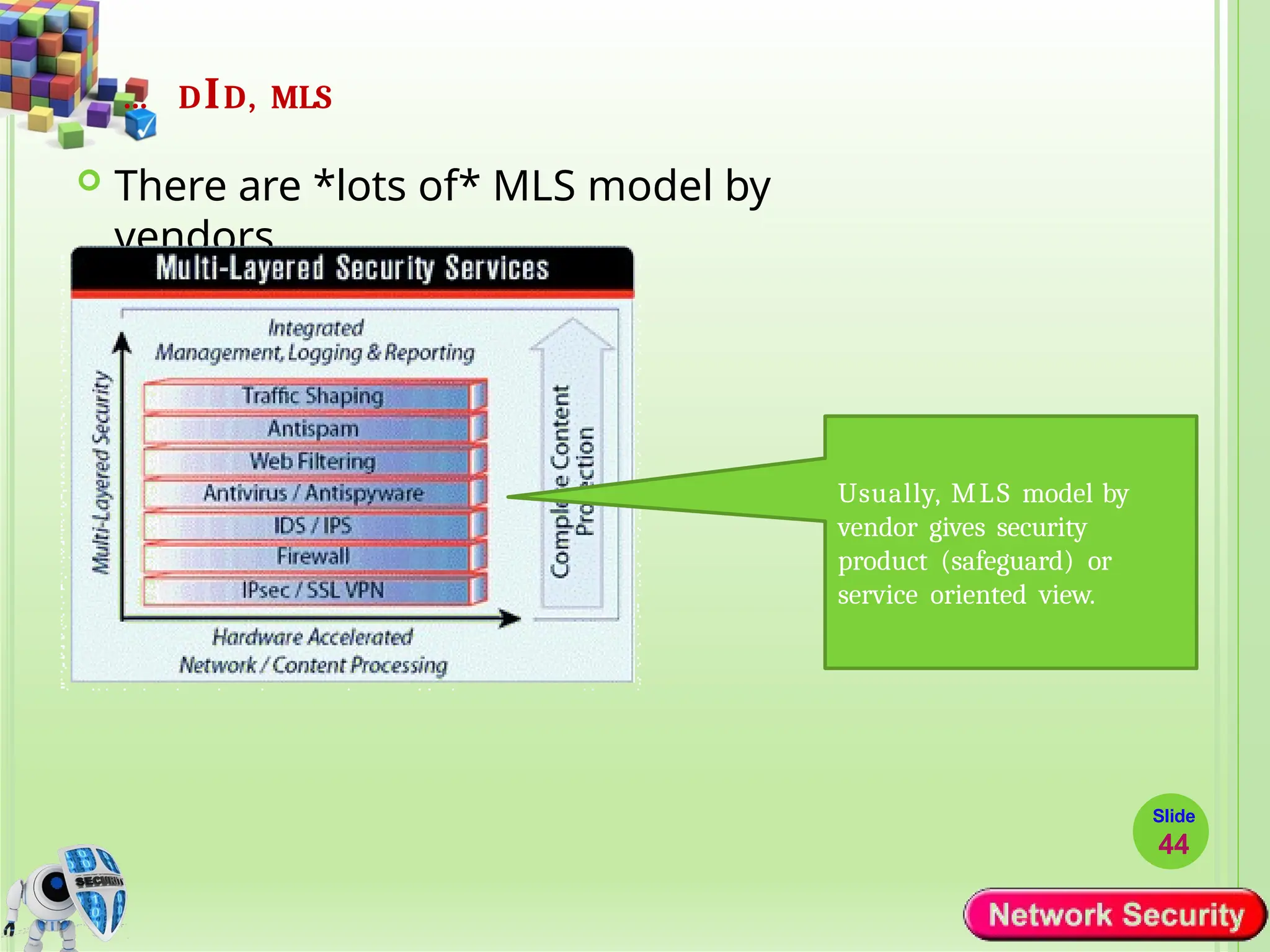
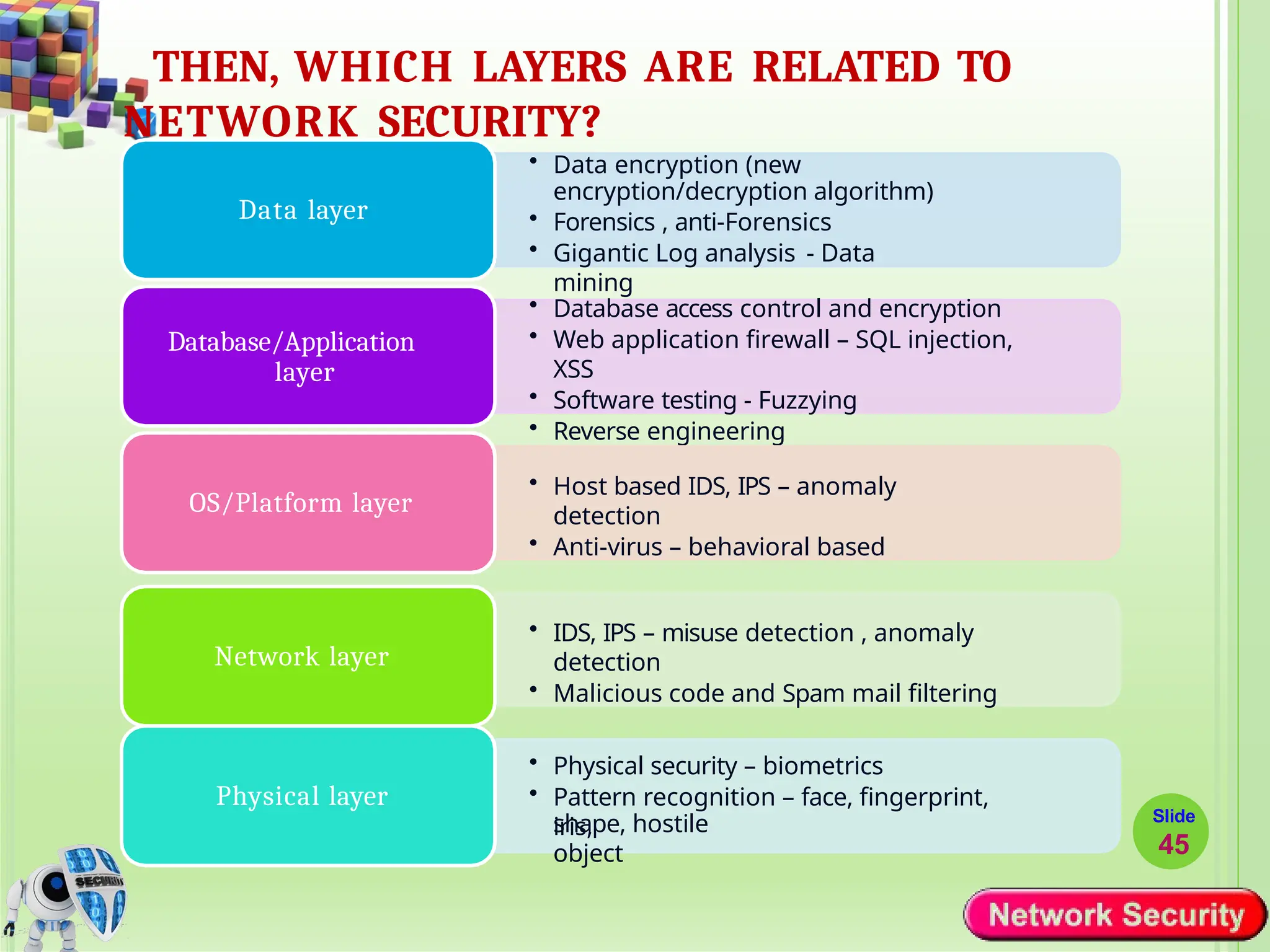
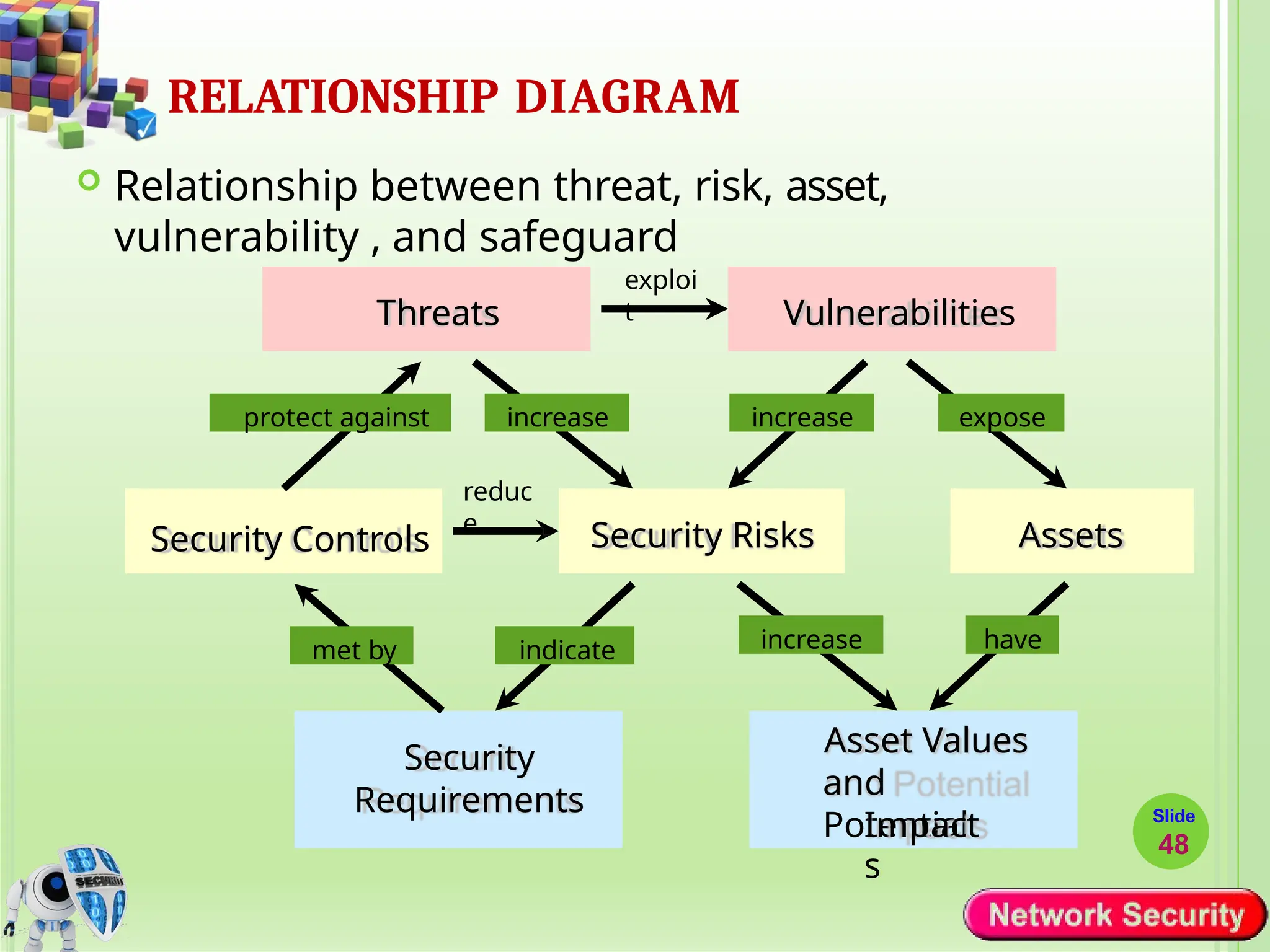
Network security refers to the practices, policies, and technologies used to protect computer networks from unauthorized access, misuse, data breaches, and attacks. It is essential for maintaining the confidentiality, integrity, and availability of data and services that networks provide. Network security is particularly crucial for organizations that handle sensitive or critical information, such as financial institutions, healthcare providers, and government agencies.