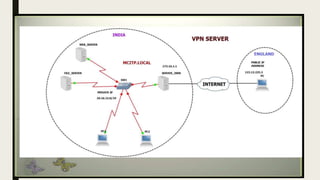
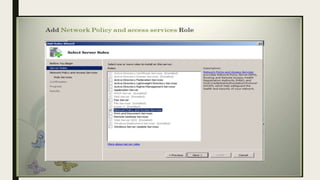
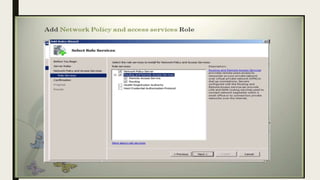
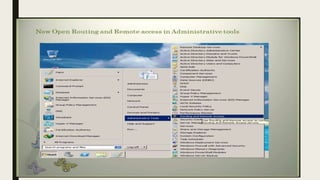
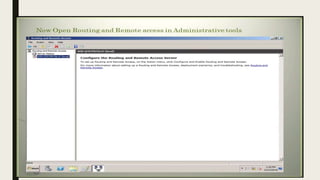
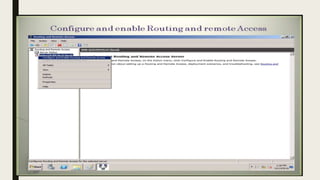
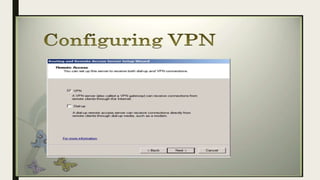
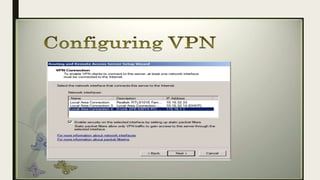
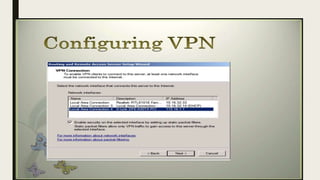
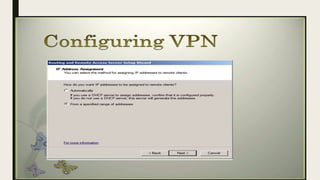
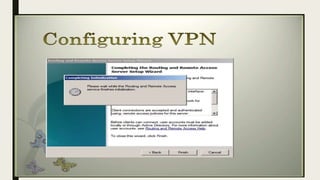
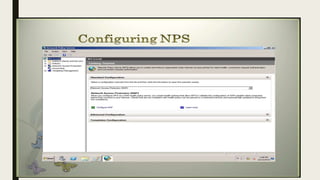
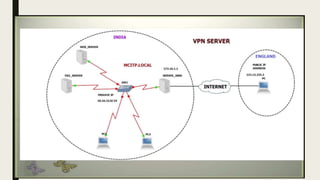
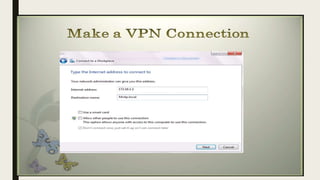
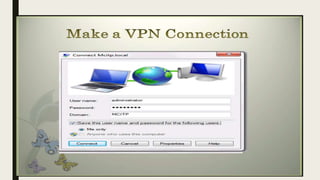
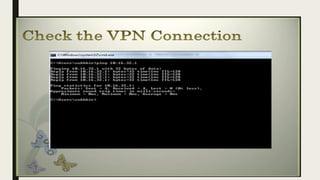
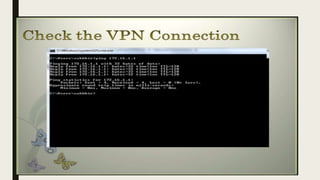
VPN allows users to securely connect to private networks over the internet. There are two main types of VPNs: remote access VPNs that allow users to access private networks remotely, and site-to-site VPNs that connect networks of different office locations. VPNs use various protocols like IPsec, L2TP, PPTP, OpenVPN, SSL/TLS, and SSH to encrypt data transmission and establish secure tunnels between devices. VPNs provide benefits such as accessing blocked websites, more secure online activity, protecting public WiFi connections, and allowing remote access to private networks.