Embed presentation
Downloaded 476 times

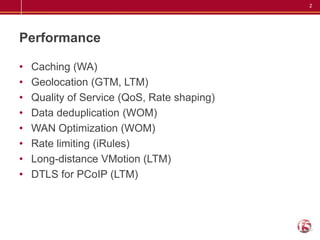



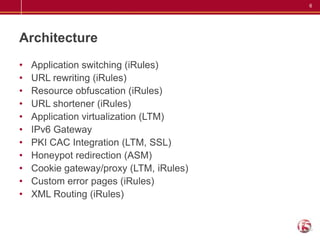




The document lists 50 different ways that the BIG-IP product can be used across several categories including performance, security, visibility, optimization, architecture, availability, and more. Some examples given are caching, geolocation, quality of service, protocol security, port lockdown, DNSSEC, application access control, IP blacklisting, load balancing, failover, global server load balancing, auto-scaling, compression, TCP offload, and centralized certificate management.








