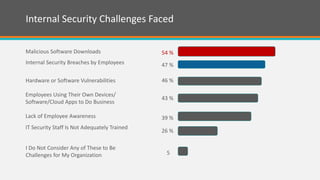
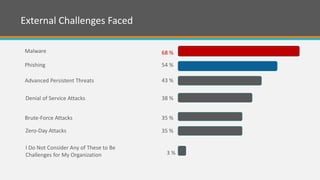
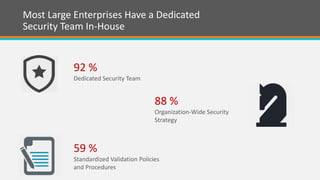
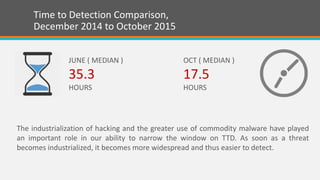
The document discusses the significant security risks faced by enterprises, with 65% of respondents perceiving their organizations as threatened, particularly in mobility, IT security, and cloud services. It highlights the importance of integrating trust and security throughout product lifecycles, as well as the internal and external security challenges organizations face. With dedicated security teams and an organization-wide strategy being essential, the document emphasizes the need for vendors to demonstrate trustworthiness to build lasting relationships with enterprises.