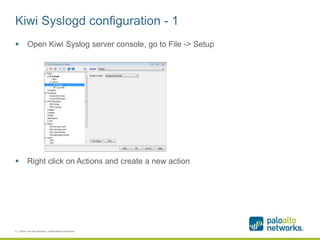
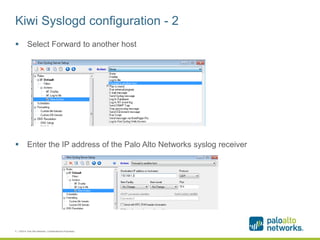
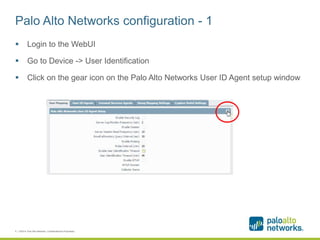
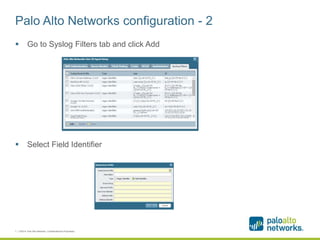
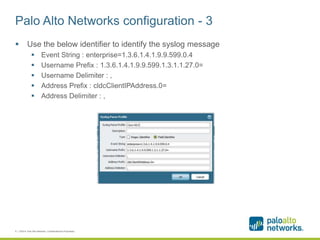
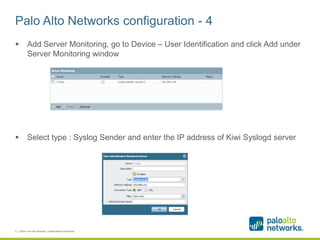
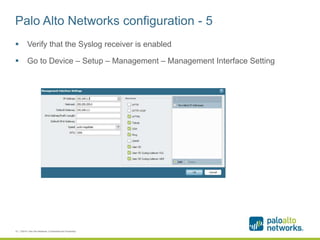
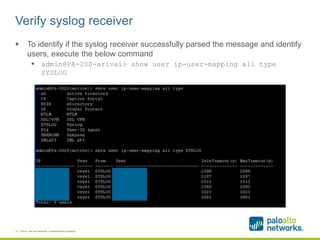
The document provides a configuration guide for integrating Cisco WLC 5500, Kiwi Syslogd, and Palo Alto Networks PAN-OS 6.1 to collect user authentication syslog messages from the Cisco WLC and map users to IP addresses in PAN-OS for use in security policies. It outlines configuring the Cisco WLC to send SNMP traps containing authentication information to Kiwi Syslogd, and Kiwi Syslogd to convert and forward the traps to the PAN-OS syslog receiver. It then details the necessary configuration steps in PAN-OS to define a syslog filter to parse and extract the user and IP address from the incoming syslog messages.