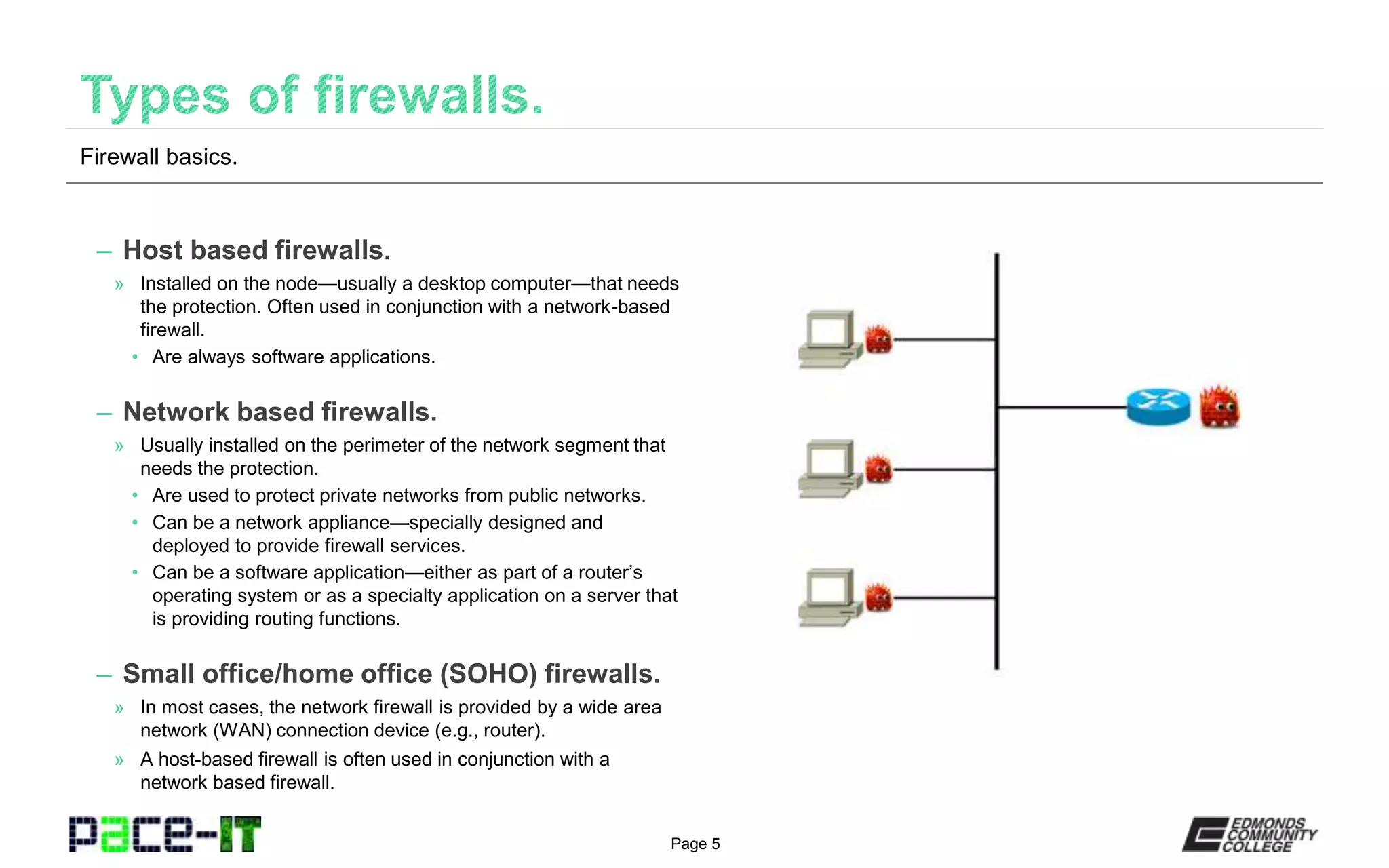
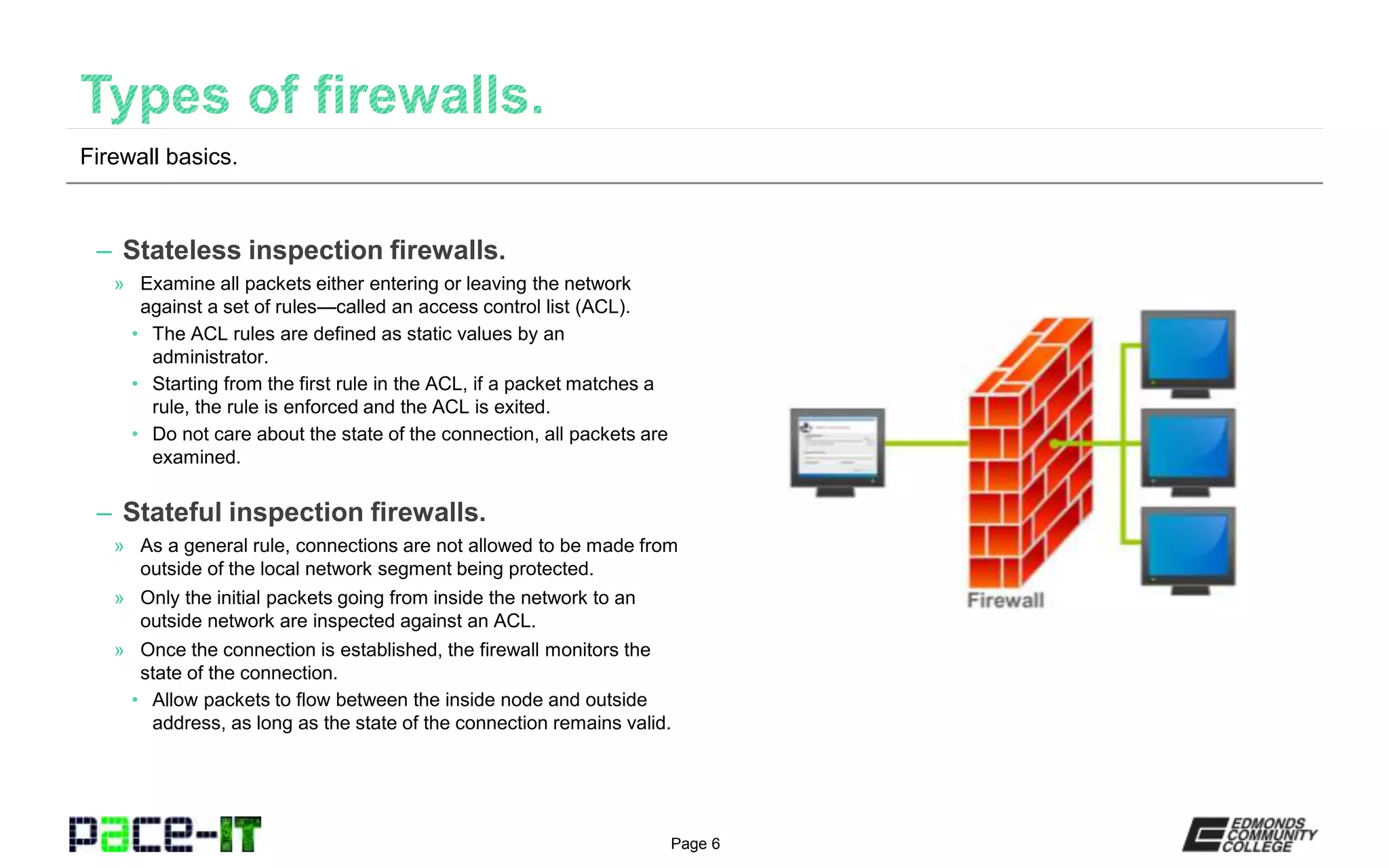
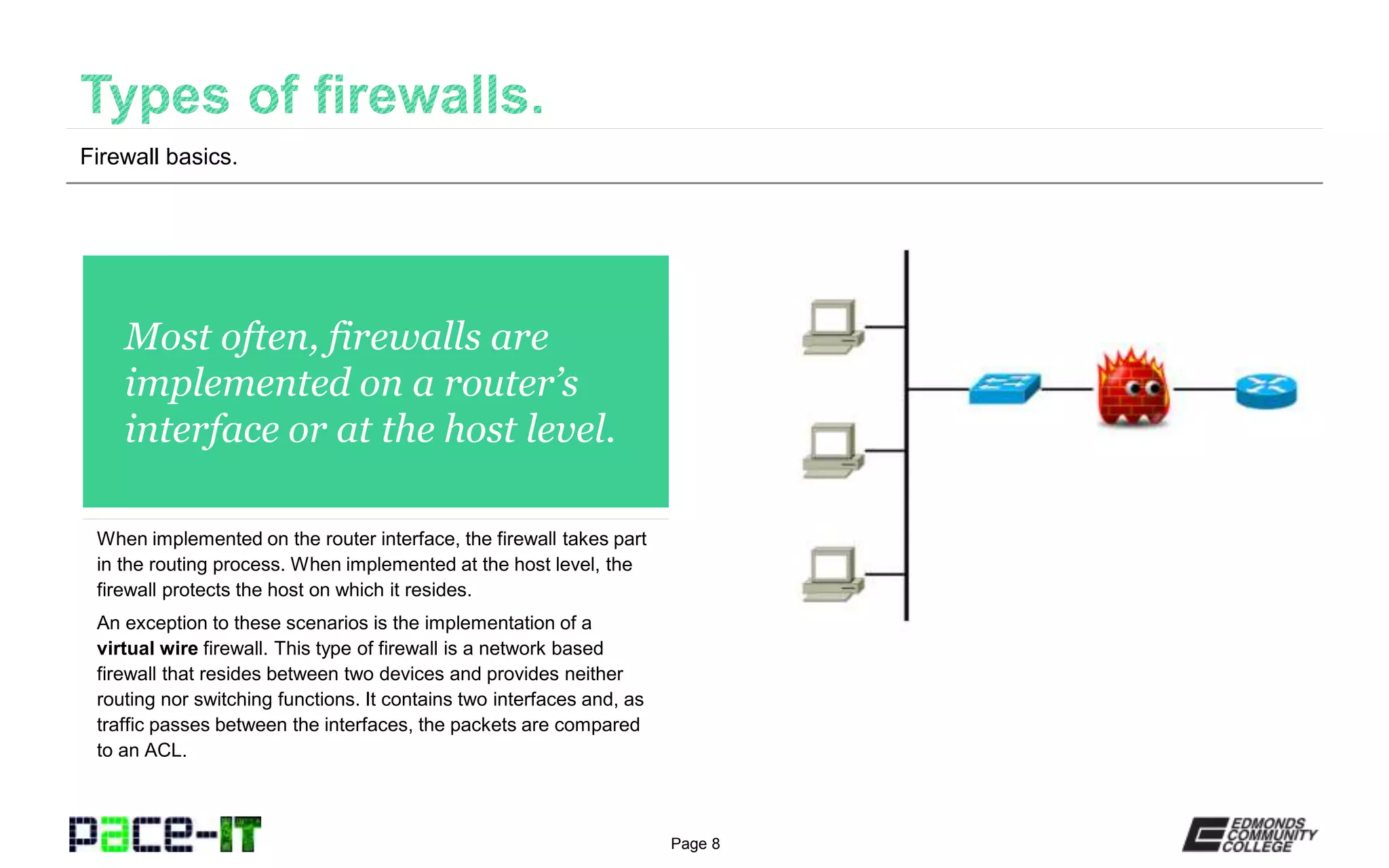
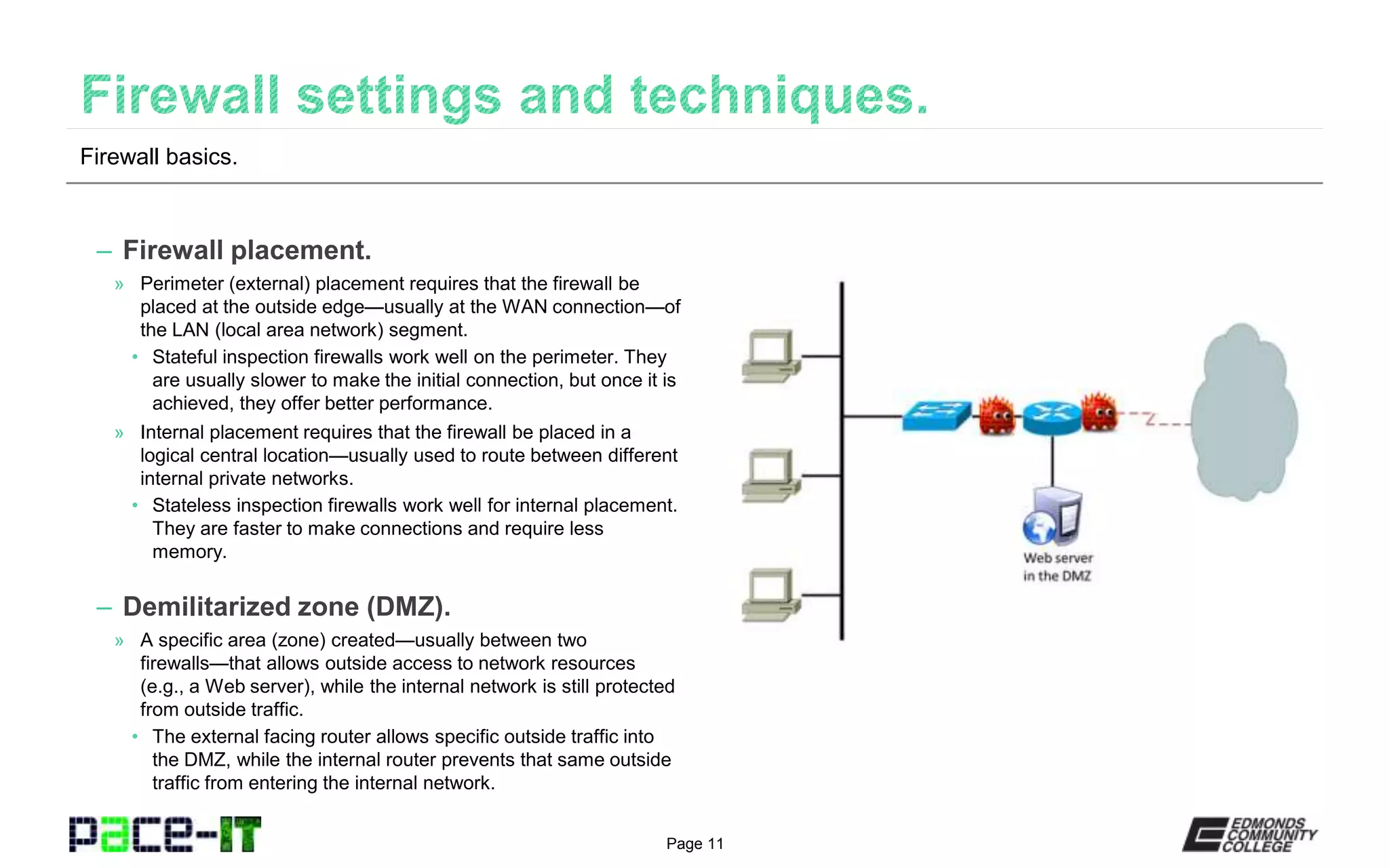
The document discusses various types of firewalls. It explains that host-based firewalls protect individual devices, while network-based firewalls protect entire network segments. Stateless firewalls inspect all packets against static rules, while stateful firewalls track the state of connections. Application-aware and context-aware firewalls examine application protocols and user/device contexts. UTM devices offer additional services like IDS/IPS but introduce single points of failure. Access control lists contain rules for inbound and outbound traffic based on attributes like source/destination IP, protocol, and time. Firewall placement depends on the inspection type - stateful firewalls work well externally, while stateless firewalls are suited internally. Demilitarized zones allow