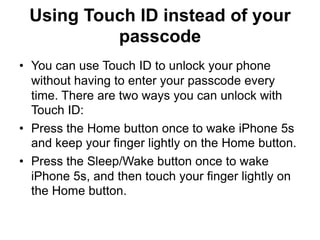
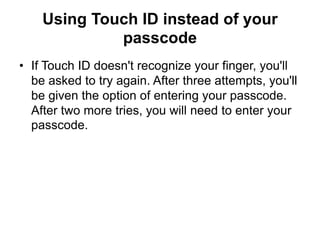
Touch ID is a fingerprint recognition feature introduced in the iPhone 5S that allows users to unlock their phone and make purchases with a fingerprint instead of a passcode. It is built into the home button using a fingerprint sensor. Fingerprint data is stored securely on the phone's processor and not on Apple servers. The document provides details on the history and acquisition of the technology by Apple, the hardware and sensor design, and how the security and privacy of fingerprints is maintained.