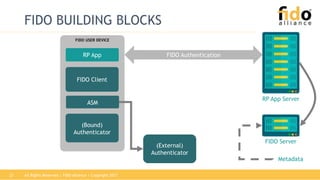
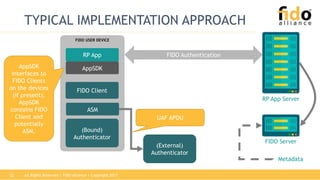
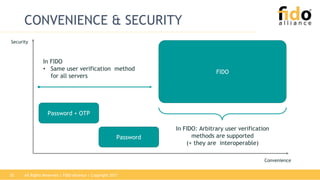
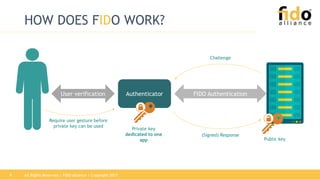
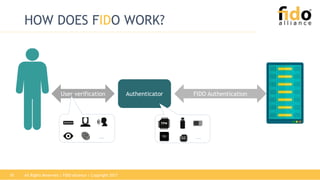
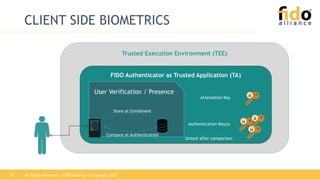
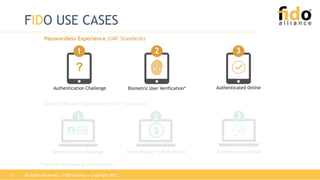
The document outlines the functionalities and security features of the FIDO (Fast Identity Online) authentication framework, emphasizing its ability to provide secure and convenient user verification methods. It addresses various authentication risks, the workings of FIDO, and the architecture for user verification and authentication using biometric and other means. Ultimately, FIDO aims to enhance security while simplifying the user experience across different applications.













![Relying Party
username, challenge, policy
appID, username, hash(fcp), [exts]
verify user
generate:
key kpub
key kpriv
keyID
fcp,ac,kpub,fcpHash,keyID,keyAlg,cntr,AAID[,exts],
signature(tbs)
fcp,ac,tbs, s
store:
key kpub
keyID
s
PlatformAuthenticator
select Authenticator according to policy;
determine facetID, check appID, get tlsData;
fcp := {challenge, facetID, appID, tlsData}
FIDO UAF REGISTRATION
tbs
ac: attestation certificate chain](https://image.slidesharecdn.com/uaftutorial-biometricsfornativeapps-180125234830/85/UAF-Tutorial-Passwordless-Biometric-Authentication-for-Native-Apps-18-320.jpg)
![Authenticator Platform Relying Party
appID, [keyID], hash(fcp)
select Authenticator according to policy;
determine facetID, check appID, get tlsData;
fcp := {challenge, facetID, appID, tlsData}
AAID,keyID,fcp,cntr,exts,
signature(AAID,keyID,fcpHash,cntr,exts)
AAID, keyID, fcp, cntr,exts, s
lookup kpub
from DB
check:
exts +
signature
using
key kpub
s
challenge, policy
FIDO UAF AUTHENTICATION
verify user
find
key kpriv
cntr++;
process exts](https://image.slidesharecdn.com/uaftutorial-biometricsfornativeapps-180125234830/85/UAF-Tutorial-Passwordless-Biometric-Authentication-for-Native-Apps-19-320.jpg)