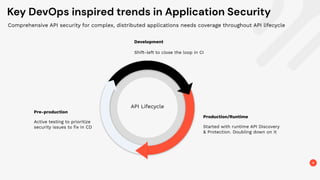
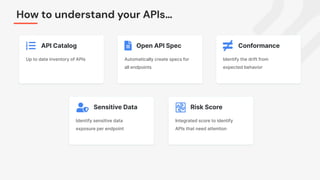
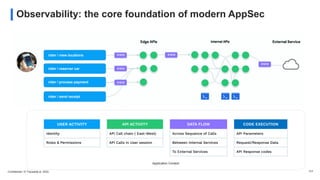
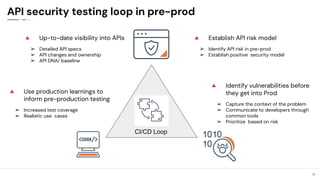
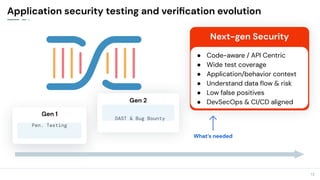
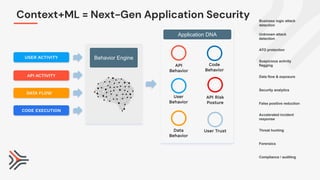
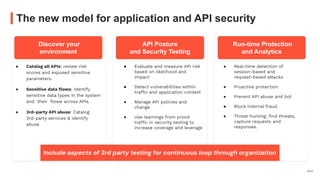
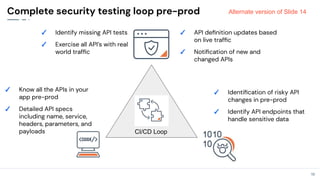
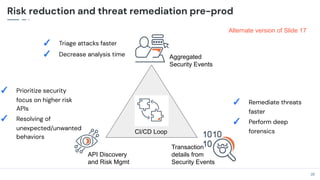
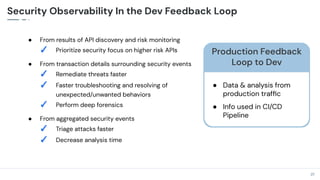
The document discusses the critical need for enhanced API security amid an increasing frequency of API security incidents, emphasizing the inadequacies of traditional security strategies in modern application environments. It advocates for a shift-left approach in security practices, including comprehensive API discovery, context awareness, and continuous testing throughout the API lifecycle. Key practices outlined include establishing risk models, implementing real-time monitoring, and leveraging production learnings to inform pre-production environments.