The document serves as an instructional guide for a WebAuthn workshop, detailing prerequisites, coding examples, and processes for implementing WebAuthn for authentication. It includes setup instructions, JavaScript examples for managing credentials, and outlines the steps for registration and challenge-response mechanisms. It is designed for attendees to learn about secure authentication practices and how to apply WebAuthn in web applications.








![MakeCredentials requestMakeCredentials request
var publicKey = {
challenge: new Uint8Array([21,31,105, ..., 55]),
rp: {
name: "ACME Corporation"
},
user: {
id: Uint8Array.from(window.atob("MIIBkzCCATigAwIBAjCCAZMwggE4oAMCAQIwggGTMII="), c=>c.charCodeAt(0
name: "alex.p.mueller@example.com",
displayName: "Alex P. Müller"
},
pubKeyCredParams: [
{
type: "public-key", alg: -7 // "ES256" IANA COSE Algorithms registry
},
{
type: "public-key", alg: -257 // "RS256" IANA COSE Algorithms registry
}
]
}
navigator.credentials.create({ publicKey })
.then((newCredentialInfo) => {
/* Public key credential */
}).catch((error) => {
/* Error */
})
Random 32byte challenge buffer
Friendly RP name
User names and userid buffer
Signature algorithm
negotiation
9](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-9-320.jpg)
![Let's try it our selves:Let's try it our selves:
var randomChallengeBuffer = new Uint8Array(32);
window.crypto.getRandomValues(randomChallengeBuffer);
var base64id = 'MIIBkzCCATigAwIBAjCCAZMwggE4oAMCAQIwggGTMII='
var idBuffer = Uint8Array.from(window.atob(base64id), c=>c.charCodeAt(0))
var publicKey = {
challenge: randomChallengeBuffer,
rp: { name: "FIDO Example Corporation" },
user: {
id: idBuffer,
name: "alice@example.com",
displayName: "Alice von Wunderland"
},
pubKeyCredParams: [
{ type: 'public-key', alg: -7 }, // ES256
{ type: 'public-key', alg: -257 } // RS256
]
}
// Note: The following call will cause the authenticator to display UI.
navigator.credentials.create({ publicKey })
.then((newCredentialInfo) => {
console.log('SUCCESS', newCredentialInfo)
})
.catch((error) => {
console.log('FAIL', error)
})
Go to and run in the consolehttps://webauthn.bin.coffee
10](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-10-320.jpg)






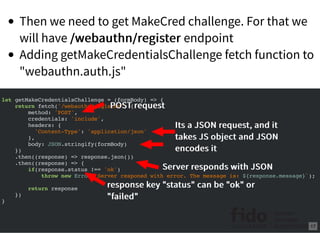


![Now lets create /webauthn/register endpoint
In routes/webauthn.js insert this code
router.post('/register', (request, response) => {
if(!request.body || !request.body.username || !request.body.name) {
response.json({
'status': 'failed',
'message': 'Request missing name or username field!'
})
return
}
let username = request.body.username;
let name = request.body.name;
if(database[username] && database[username].registered) {
response.json({
'status': 'failed',
'message': `Username ${username} already exists`
})
return
}
database[username] = {
'name': name,
'registered': false,
'id': utils.randomBase64URLBuffer(),
'authenticators': []
}
})
Check all field. The body is theCheck all field. The body is the
request.bodyrequest.body
Check that user does not exist orCheck that user does not exist or
he is not registeredhe is not registered
Creating userCreating user
Generating user random IDGenerating user random ID
This is where we storeThis is where we store
registered authenticatorsregistered authenticators
20](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-20-320.jpg)
![To generate makeCredential challenge utils have
"generateServerMakeCredRequestgenerateServerMakeCredRequest" method
let generateServerMakeCredRequest = (username, displayName, id) => {
return {
challenge: randomBase64URLBuffer(32),
rp: {
name: "FIDO Examples Corporation"
},
user: {
id: id,
name: username,
displayName: displayName
},
pubKeyCredParams: [
{
type: "public-key", alg: -7 // "ES256" IANA COSE Algorithms registry
}
]
}
}
router.post('/register', (request, response) => {
...
let challengeMakeCred = utils.generateServerMakeCredRequest(username,
name, database[username].id)
challengeMakeCred.status = 'ok'
request.session.challenge = challengeMakeCred.challenge;
request.session.username = username;
response.json(challengeMakeCred)
})
Generate makeCred challenge:Generate makeCred challenge:
passing username, name, and idpassing username, name, and id
Saving username and challengeSaving username and challenge
in session for laterin session for later
Don't forget to let browserDon't forget to let browser
know that you are ok!know that you are ok!
Send responseSend response
In routes/webauthn.js add new block of code
21](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-21-320.jpg)

![Remember this?Remember this?
var randomChallengeBuffer = new Uint8Array(32);
window.crypto.getRandomValues(randomChallengeBuffer);
var base64id = 'MIIBkzCCATigAwIBAjCCAZMwggE4oAMCAQIwggGTMII='
var idBuffer = Uint8Array.from(window.atob(base64id), c=>c.charCodeAt(0))
var publicKey = {
challenge: randomChallengeBuffer,
rp: { name: "FIDO Example Corporation" },
user: {
id: idBuffer,
name: "alice@example.com",
displayName: "Alice von Wunderland"
},
pubKeyCredParams: [
{ type: 'public-key', alg: -7 }, // ES256
{ type: 'public-key', alg: -257 } // RS256
]
}
// Note: The following call will cause the authenticator to display UI.
navigator.credentials.create({ publicKey })
.then((newCredentialInfo) => {
console.log('SUCCESS', newCredentialInfo)
})
.catch((error) => {
console.log('FAIL', error)
})
challenge is a bufferchallenge is a buffer
id is a bufferid is a buffer
23](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-23-320.jpg)
![Here is our server responseHere is our server response
{
"challenge": "IAomGjp6nnS9GvPhdRdd3ATQWdL0PXTOAHDR6pPgeXM",
"rp": {
"name": "ACME Corporation"
},
"user": {
"id": "38cuhE0p0bN5PM9hSp7WEE8oTS08OQE0igXtuBifxfo",
"name": "alice",
"displayName": "Alice"
},
"pubKeyCredParams": [{
"type": "public-key",
"alg": -7
}],
"status": "ok"
}
Oh boy, challenge is not BUFFER!Oh boy, challenge is not BUFFER!
...cause no buffers in JSON...cause no buffers in JSON
...and id as well...and id as well
Good that helpers.js have "Good that helpers.js have "preformatMakeCredReq" methodmethod
var preformatMakeCredReq = (makeCredReq) => {
makeCredReq.challenge = base64url.decode(makeCredReq.challenge);
makeCredReq.user.id = base64url.decode(makeCredReq.user.id);
return makeCredReq
}
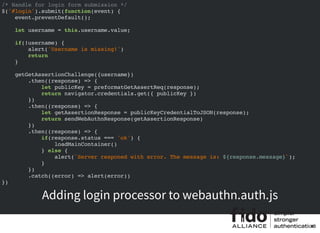
/* Handle for register form submission */
$('#register').submit(function(event) {
event.preventDefault();
let username = this.username.value;
let name = this.name.value;
if(!username || !name) {
alert('Name or username is missing!')
return
}
getMakeCredentialsChallenge({username, name})
.then((response) => {
let publicKey = preformatMakeCredReq(response);
return navigator.credentials.create({ publicKey })
})
.then((newCred) => {
console.log(newCred)
})
})
Updating #registration processor in webauthn.auth.js
24](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-24-320.jpg)





![AttestationVerificationAttestationVerification
In utils.js there is a method
"verifyAuthenticatorAttestationResponse"
let verifyAuthenticatorAttestationResponse = (webAuthnResponse) => {
let attestationBuffer = base64url.toBuffer(webAuthnResponse.response.attestationObject);
let ctapMakeCredResp = cbor.decodeAllSync(attestationBuffer)[0];
let response = {'verified': false};
if(ctapMakeCredResp.fmt === 'fido-u2f') {
let authrDataStruct = parseMakeCredAuthData(ctapMakeCredResp.authData);
if(!(authrDataStruct.flags & U2F_USER_PRESENTED))
throw new Error('User was NOT presented durring authentication!');
let clientDataHash = hash(base64url.toBuffer(webAuthnResponse.response.clientDataJSON))
let reservedByte = Buffer.from([0x00]);
let publicKey = COSEECDHAtoPKCS(authrDataStruct.COSEPublicKey)
let signatureBase = Buffer.concat([reservedByte, authrDataStruct.rpIdHash, clientDataHa
let PEMCertificate = ASN1toPEM(ctapMakeCredResp.attStmt.x5c[0]);
let signature = ctapMakeCredResp.attStmt.sig;
response.verified = verifySignature(signature, signatureBase, PEMCertificate)
if(response.verified) {
response.authrInfo = {
fmt: 'fido-u2f',
publicKey: base64url.encode(publicKey),
counter: authrDataStruct.counter,
credID: base64url.encode(authrDataStruct.credID)
}
}
}
return response
}
Decode base64url encoded assertionDecode base64url encoded assertion
buffer, and CBOR parse itbuffer, and CBOR parse it
It's a U2F statementIt's a U2F statement
Parsing raw authData bufferParsing raw authData buffer
Check that TUP flag is setCheck that TUP flag is set
Generate signature baseGenerate signature base COSE to PKCS conversionCOSE to PKCS conversion
X509 Cert buffer into PEMX509 Cert buffer into PEM
Verify signatureVerify signature
On verification, returnOn verification, return
response with new Authrresponse with new Authr
30](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-30-320.jpg)
![AuthenticatorDataAuthenticatorData
let parseMakeCredAuthData = (buffer) => {
let rpIdHash = buffer.slice(0, 32); buffer = buffer.slice(32);
let flagsBuf = buffer.slice(0, 1); buffer = buffer.slice(1);
let flags = flagsBuf[0];
let counterBuf = buffer.slice(0, 4); buffer = buffer.slice(4);
let counter = counterBuf.readUInt32BE(0);
let aaguid = buffer.slice(0, 16); buffer = buffer.slice(16);
let credIDLenBuf = buffer.slice(0, 2); buffer = buffer.slice(2);
let credIDLen = credIDLenBuf.readUInt16BE(0);
let credID = buffer.slice(0, credIDLen); buffer = buffer.slice(credIDLen);
let COSEPublicKey = buffer;
return {rpIdHash, flagsBuf, flags, counter, counterBuf, aaguid, credID, COSEPublicKey}
}
31](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-31-320.jpg)
![COSE PublicKey to PKCSCOSE PublicKey to PKCS
let COSEECDHAtoPKCS = (COSEPublicKey) => {
/*
+------+-------+-------+---------+----------------------------------+
| name | key | label | type | description |
| | type | | | |
+------+-------+-------+---------+----------------------------------+
| crv | 2 | -1 | int / | EC Curve identifier - Taken from |
| | | | tstr | the COSE Curves registry |
| | | | | |
| x | 2 | -2 | bstr | X Coordinate |
| | | | | |
| y | 2 | -3 | bstr / | Y Coordinate |
| | | | bool | |
| | | | | |
| d | 2 | -4 | bstr | Private key |
+------+-------+-------+---------+----------------------------------+
*/
let coseStruct = cbor.decodeAllSync(COSEPublicKey)[0];
let tag = Buffer.from([0x04]);
let x = coseStruct.get(-2);
let y = coseStruct.get(-3);
return Buffer.concat([tag, x, y])
}
32](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-32-320.jpg)
![Final registration responseFinal registration response
let result;
if(webauthnResp.response.attestationObject !== undefined) {
/* This is create cred */
result = utils.verifyAuthenticatorAttestationResponse(webauthnResp);
if(result.verified) {
database[request.session.username].authenticators.push(result.authrInfo);
database[request.session.username].registered = true
}
} else if(webauthnResp.response.authenticatorData !== undefined) {
/* This is get assertion */
} else {
response.json({
'status': 'failed',
'message': 'Can not determine type of response!'
})
}
if(result.verified) {
request.session.loggedIn = true;
response.json({ 'status': 'ok' })
} else {
response.json({
'status': 'failed',
'message': 'Can not authenticate signature!'
})
}
Updating /response endpoint in routes/webauthn.js 33](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-33-320.jpg)



![Take username
Check that it's exits
Generate challenge
Send it to the browser
This time we start with serverThis time we start with server
/webauthn/login endpoint/webauthn/login endpoint
router.post('/login', (request, response) => {
if(!request.body || !request.body.username) {
response.json({
'status': 'failed',
'message': 'Request missing username field!'
})
return
}
let username = request.body.username;
if(!database[username] || !database[username].registered) {
response.json({
'status': 'failed',
'message': `User ${username} does not exist!`
})
return
}
let getAssertion = utils.generateServerGetAssertion(database[username].authenticators)
getAssertion.status = 'ok'
request.session.challenge = getAssertion.challenge;
request.session.username = username;
response.json(getAssertion)
})
Save username and challengeSave username and challenge
Adding new /login endpoint in routes/webauthn.js
37](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-37-320.jpg)
![let generateServerGetAssertion = (authenticators) => {
let allowCredentials = [];
for(let authr of authenticators) {
allowCredentials.push({
type: 'public-key',
id: authr.credID,
transports: ['usb', 'nfc', 'ble']
})
}
return {
challenge: randomBase64URLBuffer(32),
allowCredentials: allowCredentials
}
}
generateServerGetAssertiongenerateServerGetAssertion
38](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-38-320.jpg)



![authenticatorData parsingauthenticatorData parsing
let parseGetAssertAuthData = (buffer) => {
let rpIdHash = buffer.slice(0, 32); buffer = buffer.slice(32);
let flagsBuf = buffer.slice(0, 1); buffer = buffer.slice(1);
let flags = flagsBuf[0];
let counterBuf = buffer.slice(0, 4); buffer = buffer.slice(4);
let counter = counterBuf.readUInt32BE(0);
return {rpIdHash, flagsBuf, flags, counter, counterBuf}
}
43](https://image.slidesharecdn.com/jan-2018-fido-seminar-webauthn-tutorial1-180126001612/85/Webauthn-Tutorial-43-320.jpg)

