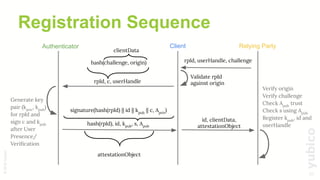
The document outlines a workshop for implementing passwordless authentication in web applications using Yubico's WebAuthn server and related technologies. It covers security principles, architecture, best practices, and provides a series of coding modules to guide participants through the setup and implementation process. Key topics include strong multi-factor authentication, credential management, and the necessary prerequisites for successful completion of the workshop.