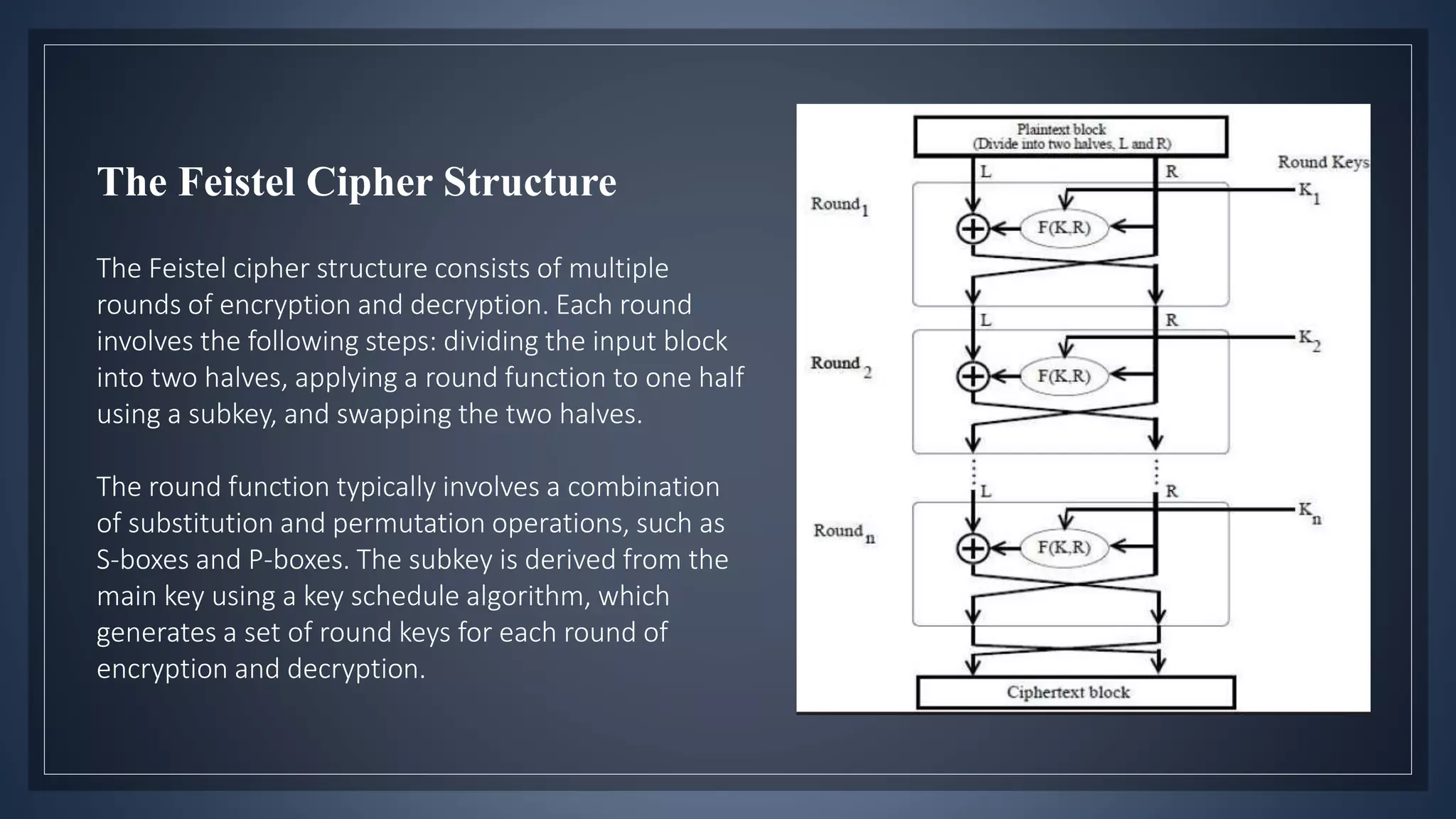
This document provides an overview of the Feistel cipher, a symmetric encryption algorithm developed by Horst Feistel in the 1970s. It describes the Feistel cipher's structure, which involves dividing plaintext into halves, applying a round function to one half using a subkey, and swapping the halves over multiple rounds of encryption. The document notes advantages like simplicity and resistance to some attacks, as well as weaknesses like vulnerability to brute force attacks. It concludes that the Feistel cipher provides strong security for many applications due to its structure and resistance to certain attacks.