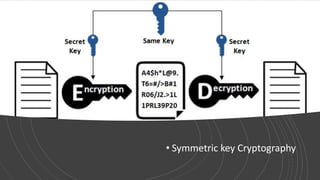
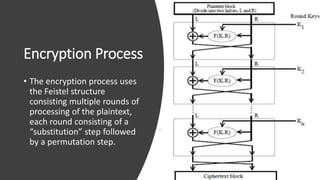
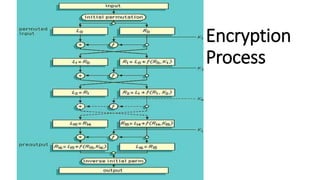
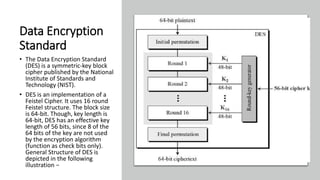
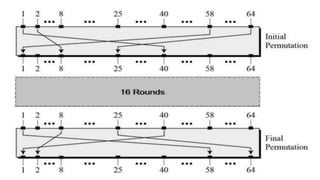
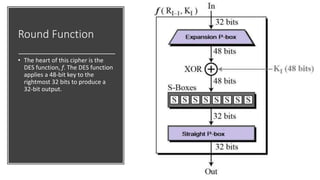
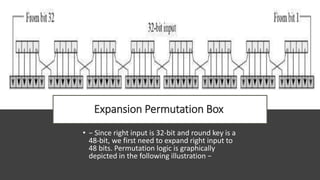
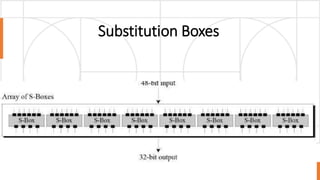
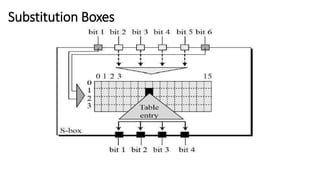
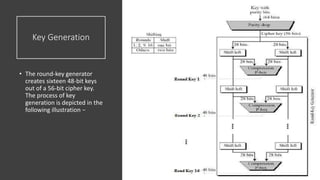
The document discusses symmetric key cryptography, focusing on the Feistel cipher, which is a design model for block ciphers like the Data Encryption Standard (DES). It details the encryption and decryption processes involving multiple rounds of substitution and permutation, the role of round keys, and the importance of the round function. The DES algorithm specifically uses a 16-round Feistel structure with a 64-bit block size and an effective key length of 56 bits, while also addressing its strengths and weaknesses.