Embed presentation
Downloaded 19 times




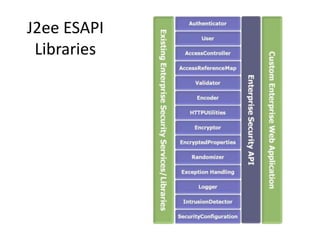
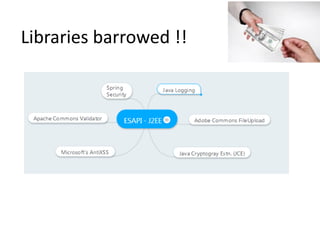
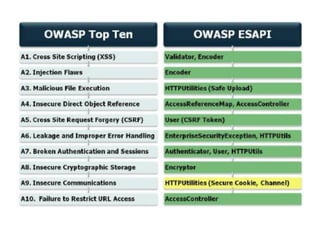
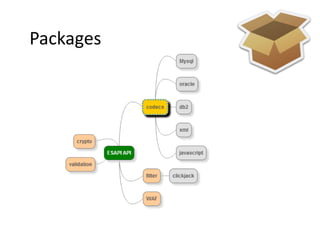


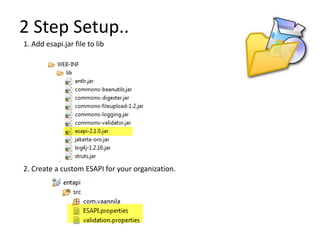
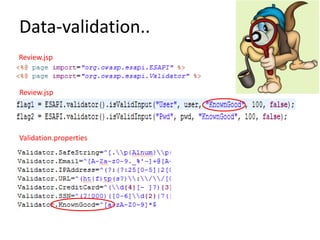
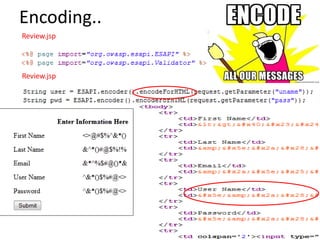



This document discusses the OWASP ESAPI project, a security API that aims to simplify application security for developers. It provides an overview of ESAPI, including that it contains over 120 security methods and interfaces and was first released in 2010. The document also notes that developers should customize ESAPI to match their own organization and that canonicalization and encoding features are mature, while data validation could be improved.















