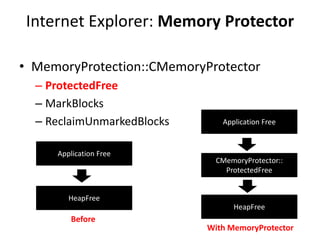
The document provides an overview of use-after-free (UAF) vulnerabilities, exploitation methods, and mitigation strategies implemented in Internet Explorer. It details how the memory protector manages object deallocation to prevent re-use of freed objects, along with various application and environment-specific mitigations. The presentation includes links to references and resources for further understanding of UAF exploit development and mitigation techniques.


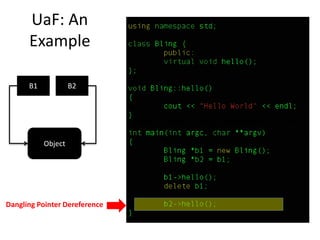
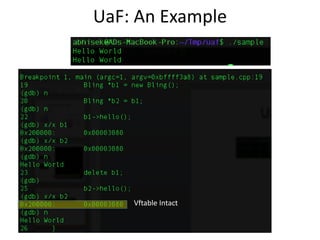
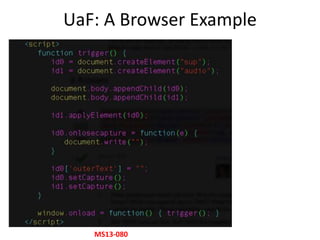
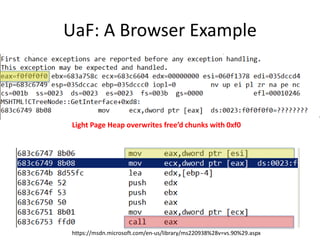

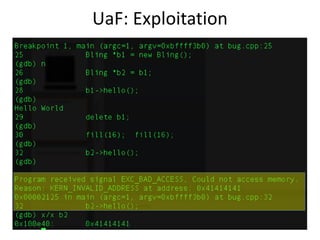
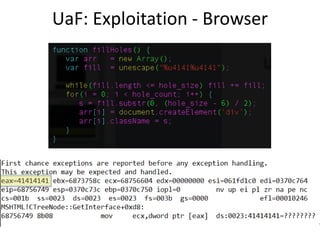
![UaF: Exploitation – Object Re-use
Object
B1
B2
Function 1
Function 2
Function …
Vftable
Objectdelete b1 [Object Freed]
0x414141fill(16) [Re-use memory block]
0x414141
B2
b2->hello()](https://image.slidesharecdn.com/iememoryprotection-150427092942-conversion-gate01/85/IE-Memory-Protector-10-320.jpg)
![Fundamental Mitigations
• Non-executable Data Pages [NX]
– PageExec [PaX/Grsecurity]
– DEP [Windows]
– W ^ X [OpenBSD]
– […]
• Address Space Layout Randomization (ASLR)](https://image.slidesharecdn.com/iememoryprotection-150427092942-conversion-gate01/85/IE-Memory-Protector-12-320.jpg)
![Environment Specific Mitigations
• Windows
– SafeSEH, SEHOP
– Stack Protection
– Vftable Guard
– Control Flow Guard
– […]
• Internet Explorer
– Enhanced Protected Mode (EPM)
– Nozzle & Bubble
– Isolated Heap
– Memory Protector
– […]](https://image.slidesharecdn.com/iememoryprotection-150427092942-conversion-gate01/85/IE-Memory-Protector-13-320.jpg)