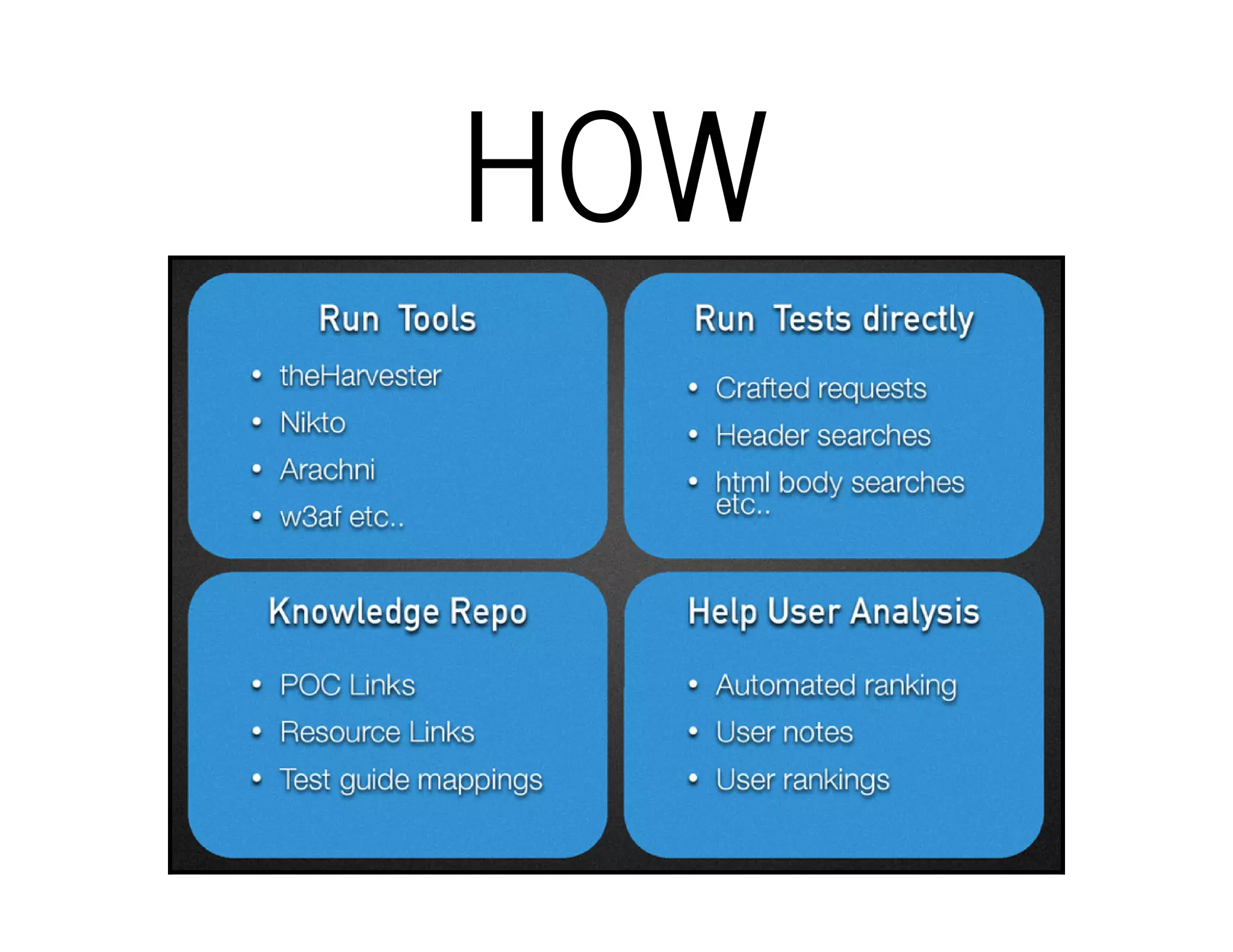
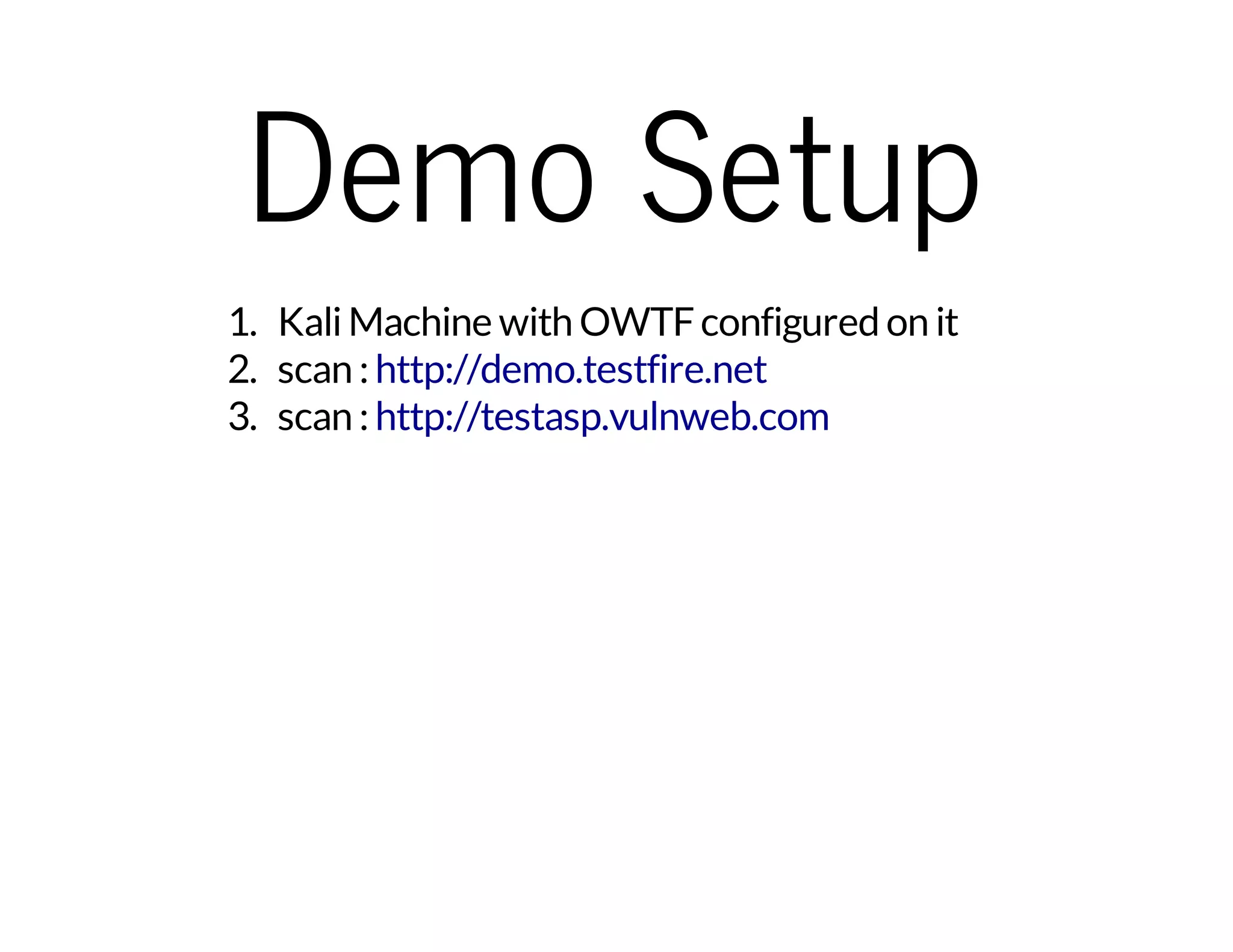
The document outlines the OWTF (Offensive Web Testing Framework), an automated penetration testing tool designed to organize findings according to various security standards. Developed in Python, it supports Kali Linux and integrates multiple tools for task execution and result aggregation. It provides resources for setup, contributions, and demo access, as well as links for further exploration.