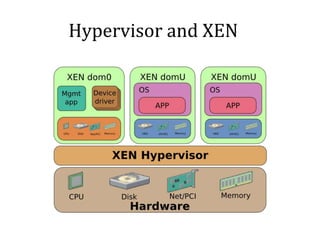
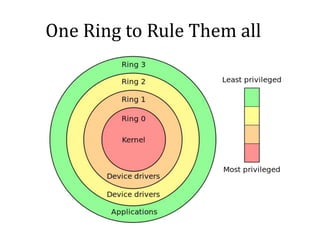
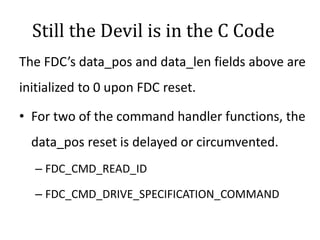
This vulnerability, called VENOM, allows an attacker to escape from a virtual machine guest into the host system. It affects virtualization platforms that use Xen, Qemu, KVM, or VirtualBox as their hypervisor. The vulnerability is in the virtual floppy disk controller code, which contains a buffer overflow issue. This allows an attacker to potentially gain code execution on the host machine. It is a serious issue because many cloud providers use these vulnerable virtualization platforms.