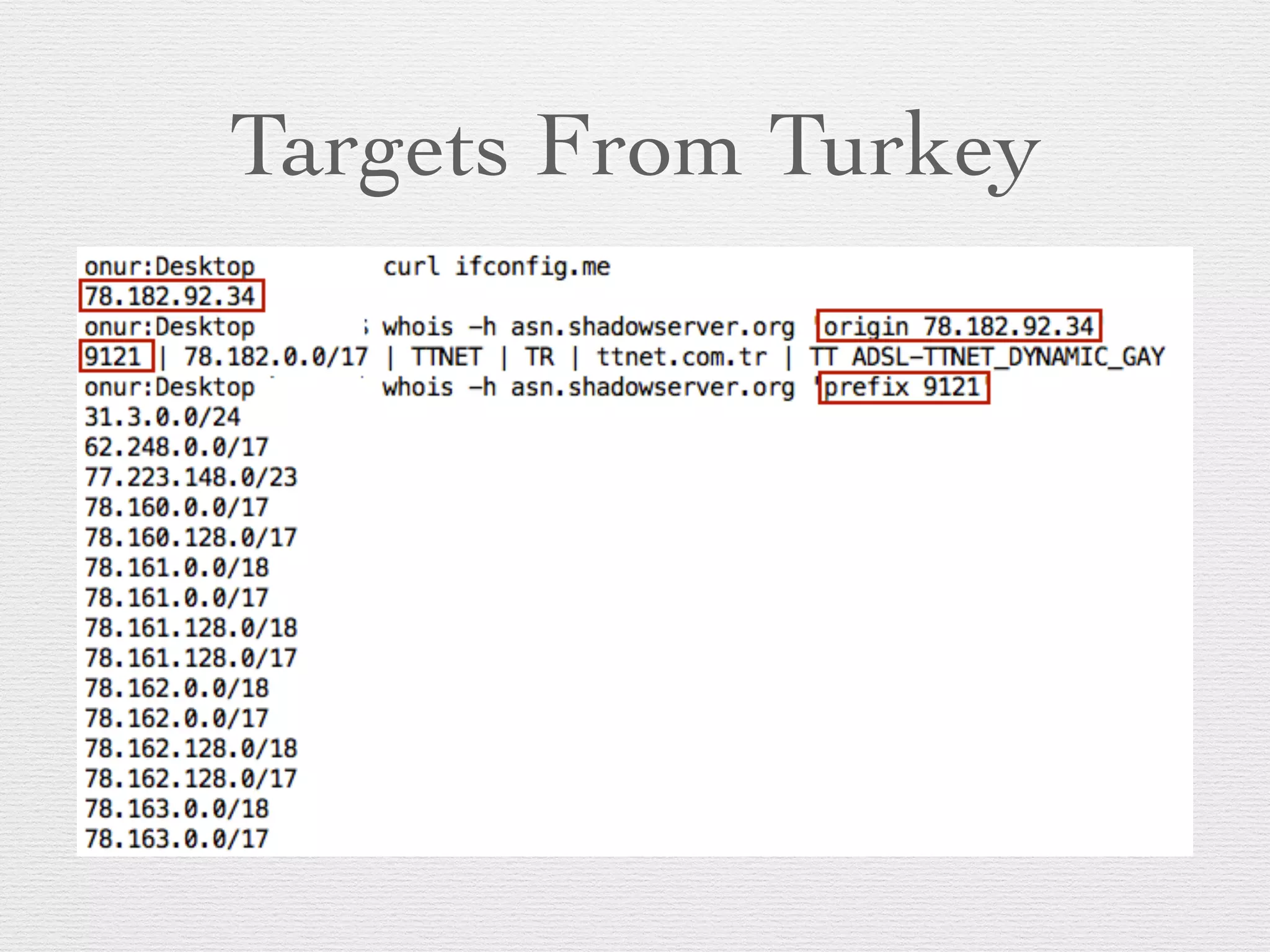
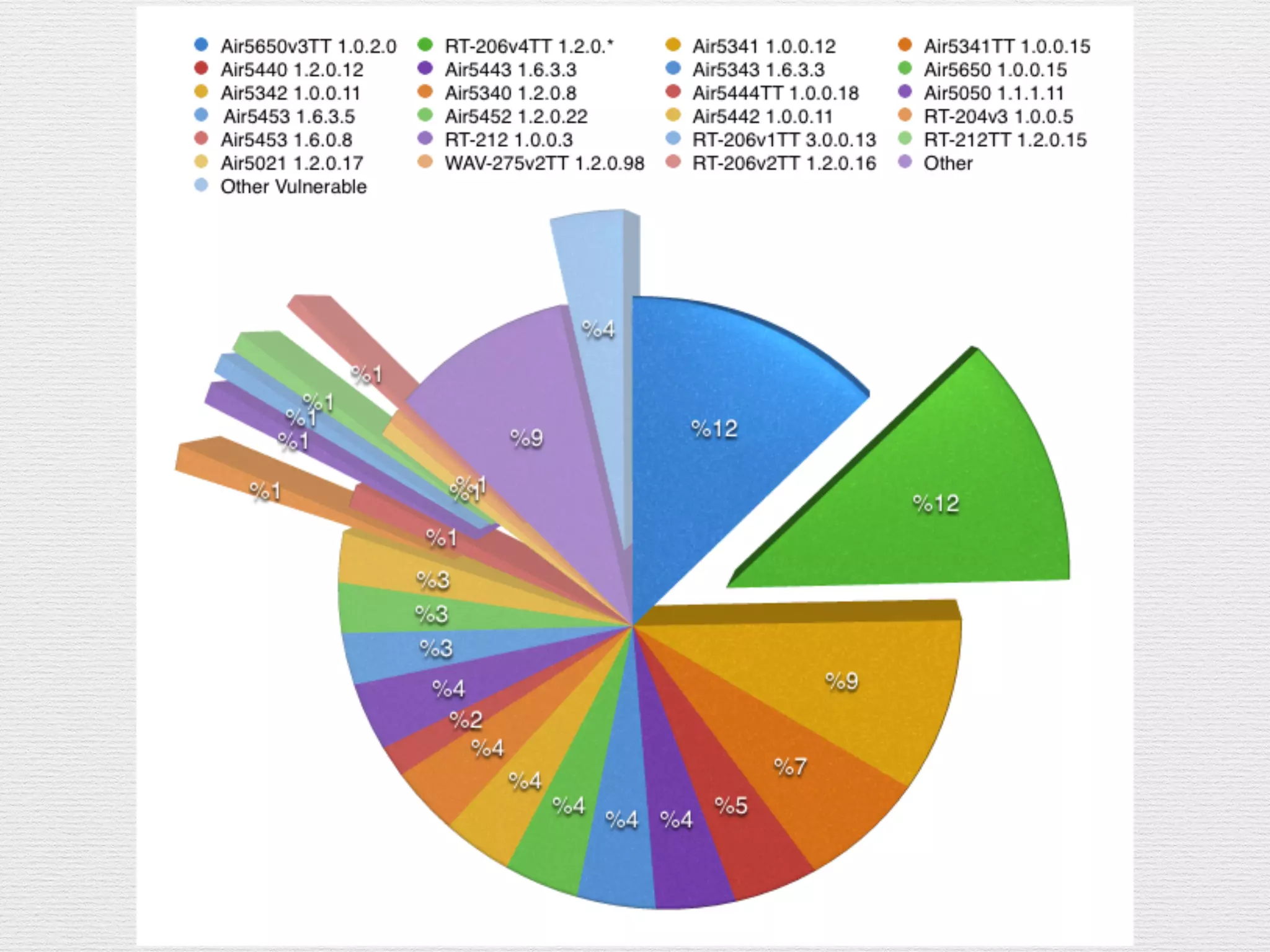
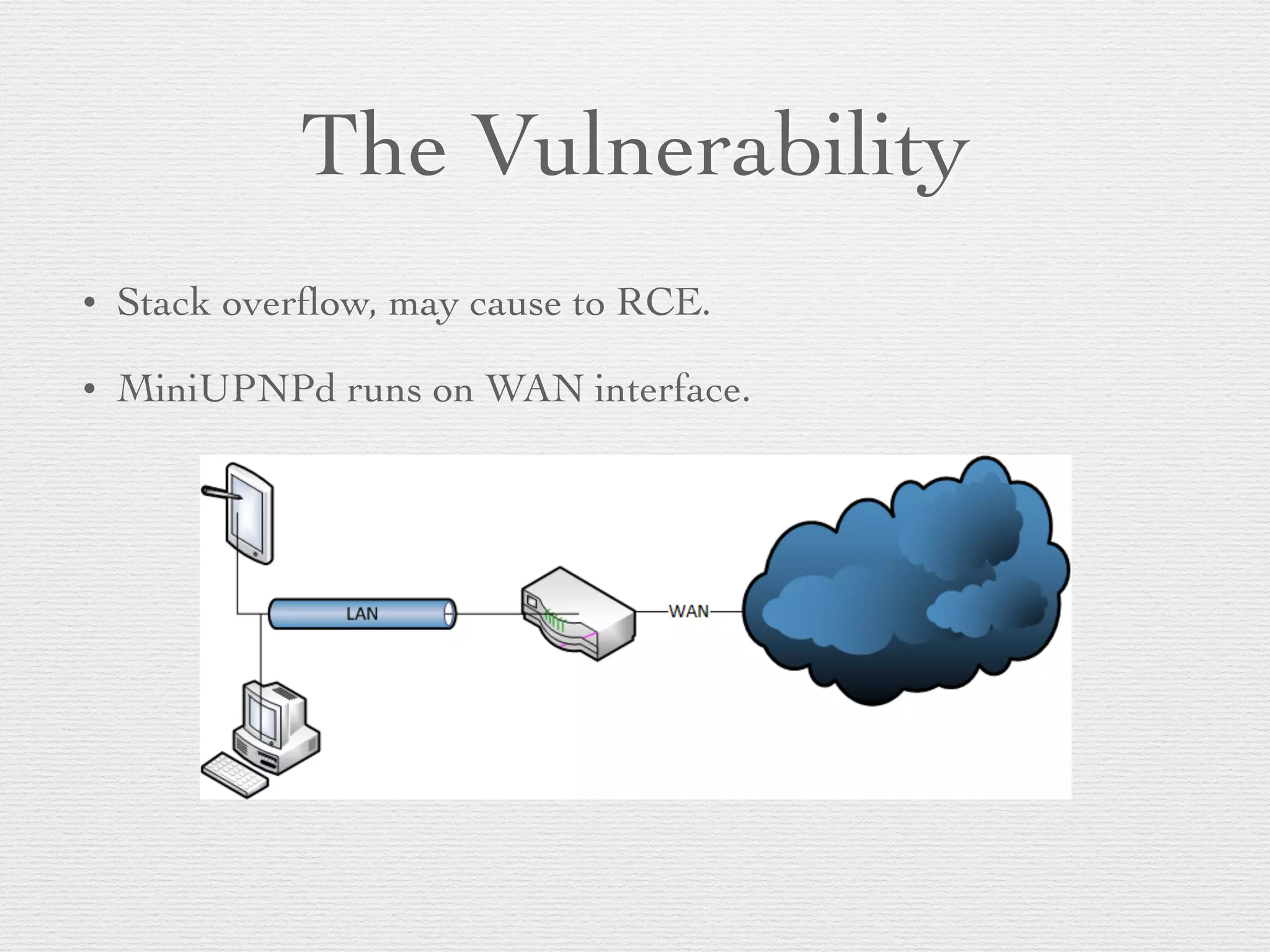
This document outlines a plan to hack routers by exploiting vulnerabilities. The plan involves deciding targets, finding vulnerabilities in routers like the AirTies RT series, writing exploits in MIPS assembly to achieve remote code execution, writing scripts for mass exploitation, running attacks on targets in Turkey, and analyzing results. Routers are attractive targets because they are directly internet accessible, can control all traffic once compromised, have limited logging capabilities, and rarely receive security updates.