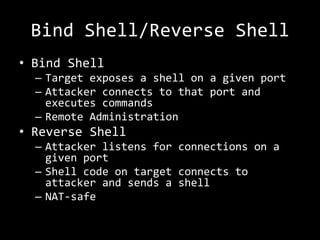
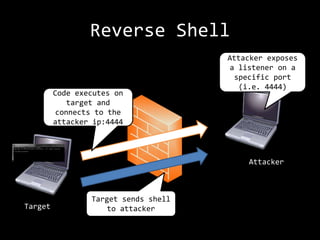
The presentation by Rob Gillen details the anatomy of a buffer overflow attack, focusing on its technical aspects and the responsibilities associated with knowledge in cybersecurity. It covers scenarios involving vulnerabilities, fuzzing, shellcode, and the exploitation process, emphasizing the importance of bounds checking and responsible testing. The session aims to educate attendees about real attack methods on systems they have explicit permission to test.














![Shellcode Example
[BITS 32]
mov ebx, 0x00424F52
push ebx
mov esi, esp
xor eax, eax
push eax
push esi
push esi
push eax
mov eax, 0x7E45058A
call eax](https://image.slidesharecdn.com/codestock-bufferoverflow-120616141715-phpapp01/85/Anatomy-of-a-Buffer-Overflow-Attack-16-320.jpg)
![[BITS 32]
mov ebx, 0x00424F52 ; Loads a null-terminated string “ROB” to
ebx
push ebx ; pushes ebx to the stack
mov esi, esp ; saves null-terminated string “ROB” in esi
xor eax, eax ; Zero our eax (eax=0)
push eax ; Push the fourth parameter (uType) to the
stack (value 0)
push esi ; Push the third parameter (lpCaption) to
the stack (value ROB00)
push esi ; Push the second parameter (lpText) to the
stack (value ROB00)
push eax ; Push the first parameter (hWnd) to the
stack (value 0)
mov eax, 0x7E45058A ; Move the MessageBoxA address in to eax
call eax ; Call the MessageBoxA function with all
parameters supplied.](https://image.slidesharecdn.com/codestock-bufferoverflow-120616141715-phpapp01/85/Anatomy-of-a-Buffer-Overflow-Attack-17-320.jpg)