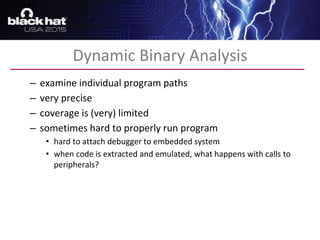
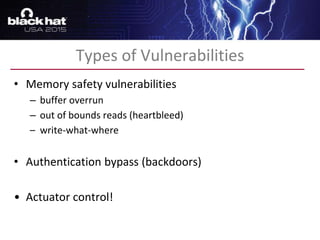
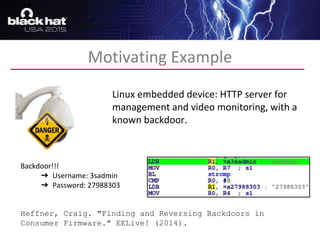
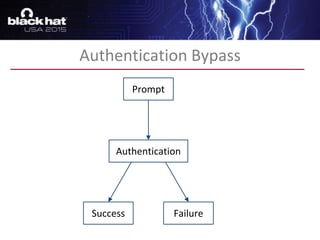
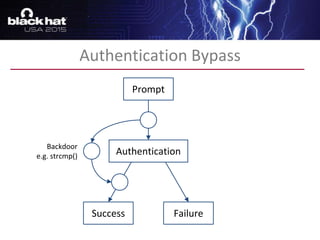
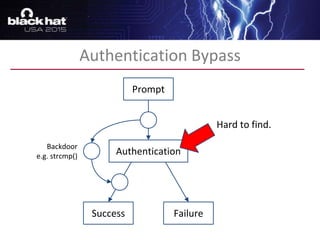
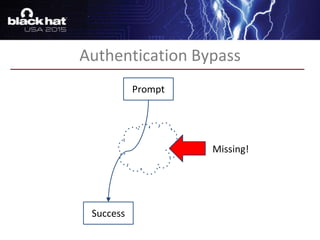
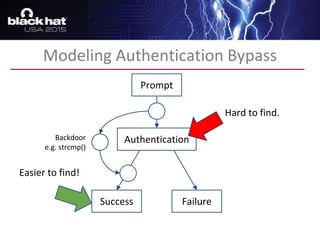
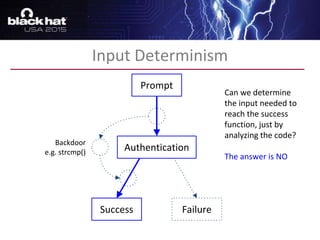
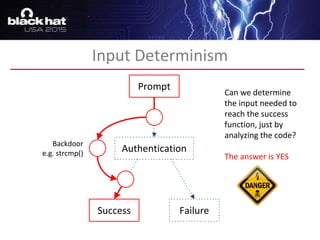
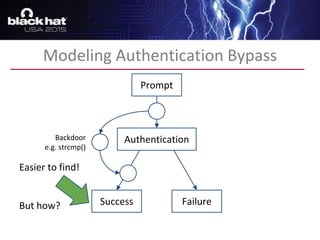
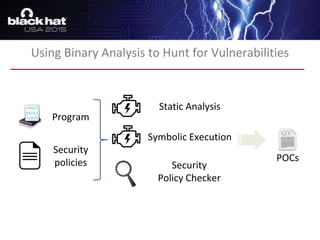
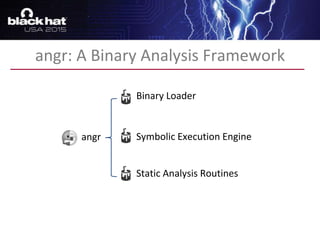
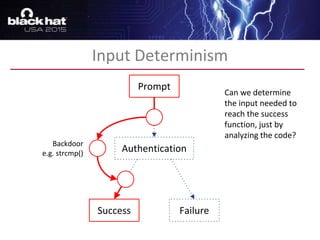
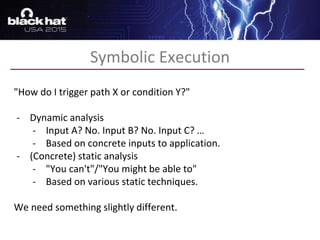
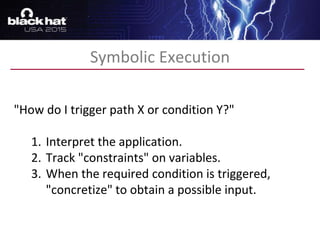
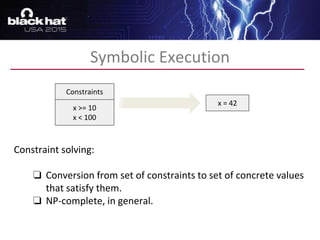
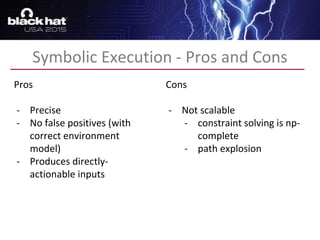
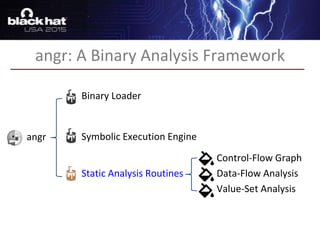
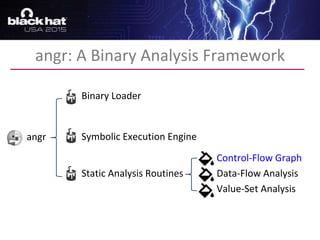
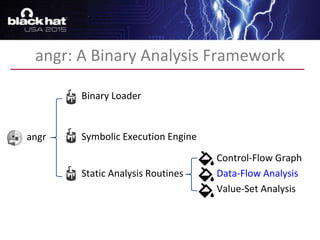
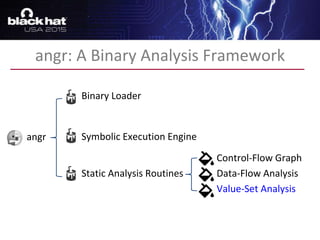
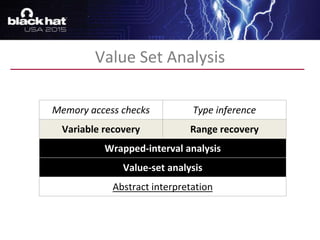
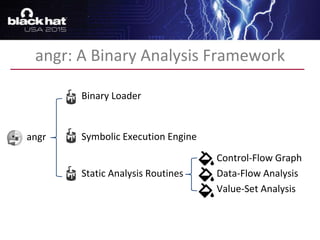
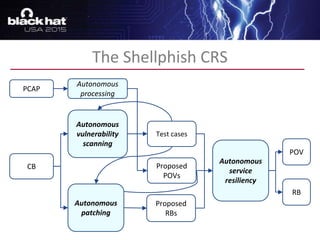
The document discusses advanced binary analysis techniques for embedded devices, highlighting the challenges of static and dynamic analysis, especially in the context of security vulnerabilities. It emphasizes the role of frameworks like angr for symbolic execution and provides insights into the complexities of analyzing binaries without full OS and library information. Additionally, it outlines types of vulnerabilities commonly found in embedded systems, including authentication bypass and memory safety issues.
















![Example
cmp rbx, 0x1024
ja _OUT
cmp [rax+rbx], 1337
je _OUT
add rbx, 4
rbx?
What is rbx in the yellow square?mov rax, 0x400000
mov rbx, 0
Symbolic execution: state explosion
Naive static analysis: "anything"
Range analysis: "< 0x1024"
Can we do better?](https://image.slidesharecdn.com/us15-kruegel-firmware-150827165421-lva1-app6891/85/Using-Static-Binary-Analysis-To-Find-Vulnerabilities-And-Backdoors-in-Firmware-46-320.jpg)
![Value Set Analysis - Strided Intervals
4[0x100, 0x120],32
Stride Low High Size
0x100 0x10c 0x118
0x104 0x110 0x11c
0x108 0x114 0x120](https://image.slidesharecdn.com/us15-kruegel-firmware-150827165421-lva1-app6891/85/Using-Static-Binary-Analysis-To-Find-Vulnerabilities-And-Backdoors-in-Firmware-48-320.jpg)
![Example
cmp rbx, 0x1024
ja _OUT
cmp [rax+rbx], 1337
je _OUT
add rbx, 4
rbx?
What is rbx in the yellow square?
1. 1[0x0, 0x0],64
2. 4[0x0, 0x4],64
3. 4[0x0, 0x8],64
4. 4[0x0, 0xc],64
5. 4[0x0, ∞],64
6. 4[0x0, 0x1024],64
mov rax, 0x400000
mov rbx, 0
Widen
Narrow
1
234 5
6](https://image.slidesharecdn.com/us15-kruegel-firmware-150827165421-lva1-app6891/85/Using-Static-Binary-Analysis-To-Find-Vulnerabilities-And-Backdoors-in-Firmware-49-320.jpg)

![Angr Mini-howto
# ipython
In [1]: import angr, networkx
In [2]: binary = angr.Project("/some/binary")
In [3]: cfg = binary.analyses.CFG()
In [4]: networkx.draw(cfg.graph)
In [5]: explorer = binary.factory.path_group()
In [6]: explorer.explore(find=0xc001b000)](https://image.slidesharecdn.com/us15-kruegel-firmware-150827165421-lva1-app6891/85/Using-Static-Binary-Analysis-To-Find-Vulnerabilities-And-Backdoors-in-Firmware-55-320.jpg)

![Value Set Analysis - Strided Intervals
4[0x100, 0x110],32 + 1 = 4[0x101, 0x111],32
4[0x100, 0x110],32 >> 1 = 2[0x80, 0x88],31
2[0x80, 0x88],31 << 1 = 1[0x100, 0x110],32
4[0x100, 0x110],32 ⋃ 4[0x102, 0x112],32 = 2[0x100, 0x112],32
4[0x100, 0x110],32 ⋂ 3[0x100, 0x110],32 = 12[0x100, 0x112],32
WIDEN (4[0x100, 0x110],32 ⋃ 4[0x100, 0x112],32) = 4[0x100, ∞],32](https://image.slidesharecdn.com/us15-kruegel-firmware-150827165421-lva1-app6891/85/Using-Static-Binary-Analysis-To-Find-Vulnerabilities-And-Backdoors-in-Firmware-58-320.jpg)