The document discusses vulnerabilities associated with linked lists in the Windows kernel, specifically focusing on CVE-2013-3660. It outlines exploitation techniques, mitigation strategies, and the impact of changes from Windows 7 to Windows 8.1. The author emphasizes the significance of proper initialization and checks to prevent security flaws in kernel management.

![#whoami - Peter Hlavaty
[ KEEN TEAM ]
Background
@K33nTeam
Previously ~4 years in ESET
Contact
twitter : @zer0mem
weibo : weibo.com/u/5238732594
blog : http://zer0mem.sk
src : https://github.com/zer0mem](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-2-2048.jpg)

![CVE 2013-3660 [refs]
CVE :
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-3660
https://technet.microsoft.com/library/security/ms13-053
Exploitation & Info :
http://blog.cmpxchg8b.com/2013/05/introduction-to-windows-kernel-security.
html
Used technique for code execution :
http://poppopret.blogspot.sk/2011/07/windows-kernel-exploitation-basics-
part.html](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-4-2048.jpg)
![_LIST_ENTRY problem
[CVE 2013-3660]
Classical U N L I N K problem](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-5-2048.jpg)
![_LIST_ENTRY attack
[CVE 2013-3660]
Attack
surface
WritePtr
win3k pool (“tapG”) addr
Write-Where
_LIST_ENTRY.Flink
Vulnerability
detail
Write Kernel Ptr
address of PATHRECORD
Content of
PATHRECORD
controlled data](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-6-2048.jpg)
![Mittigations
[ … ]
LIST_ENTRY assertions
In Heap management commonly used SafeLink check
Win 8.1 comes with this feature for LIST_ENTRY overall
http://www.alex-ionescu.com/?p=69
Implemented across kernel, but f.e. in this case :
btw. PATHRECORD contains _LIST_ENTRY, but not implemented check even in
win8.1 at win32k!EPATHOBJ::bFlatten](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-7-2048.jpg)
![BYPASS
[safe link check]
SafeLink checks, really big deal ?
Relink original chain to
heap-sprayed chain
ENTRY pass the check
without problem!
http://www.slideshare.net/PeterHlavaty/how-safe# - syscan360, 2013; “How safe is your link ?”](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-8-2048.jpg)
![Advanced mittigations ?
[UserHeap vs _LIST_ENTRY]
HEAP
•validate also in search algorithm itself!
Kernel
•BUT assertions used only by un/linking
Idea
• Relink and conquer forever](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-9-2048.jpg)
![CVE-2013-3660
[no overflow – but lack of initialization!]
PATHRECORD I
Allocated
Inserted to win32k!EPATHOBJ list
Setup-ed almost OK
except FLINK!
Supposed to be done later](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-10-2048.jpg)
![CVE-2013-3660
[no overflow – but lack of initialization!]
.. later …
PATHRECORD II
NOT-Allocated
PATHRECORD I
FLINK setup ?
NOT-going to happen
Invalid PATHRECORD in
win32k!EPATHOBJ list!](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-11-2048.jpg)
![CVE-2013-3660
[plan & impl]
SETUP your fakelist
Correctly linked
Fullfill custom checks
while(1) loop at the end](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-12-2048.jpg)
![Relink & Conquer
[ KERNEL ]
Trigger one
ptr-write
Recover
heap-sprayed
chain
•Headers
•Flink / Blink
Set new
entry.Flink for
ptr-write
Idea of one ptr-write
Relink to
heap-sprayed
chain
use entry.Flink
as where-to-write
Idea of ‘countless’ ptr-writes](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-13-2048.jpg)
![CVE-2013-3660
[what is threads for ?]
Current thread in SYSCALL
Cpl0
Win32k!EPATHOBJ::bFlatten
Trigger vuln
catch win32k thread in loop
Detect hangout
Abuse PATHRECORD.FLINK](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-14-2048.jpg)
![CVE-2013-3660
[what is threads for ?]
Boosting vuln
! Catch win32k thread again
Recover fake list
Abuse next FLINK again
No-need watchdog anymore
No-need to trigger vuln again
FAST
Reliable](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-15-2048.jpg)
![CVE-2013-3660
Implementation of ‘countless’ ptr-writes :
Made forever loop, at the end of chain
entry_end.Flink = entry_end
Per write play with fake chain :
[boosting]
Set forever loop in the beginning; // entry_beg.Flink = entry_beg
Unset forever loop at the end; // entry_end.Flink = entry_beg
Resume (altered begin-forever-loop)
Set forever loop at the end; // entry_end.Flink = entry_end
Set FLINK; // entry.Flink = Where-To-Write
Unset forever loop at the begin; // entry_beg.Flink = entry](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-16-2048.jpg)
![CVE-2013-3660
[boosting]
Reset your fake list
handle leaks
while(1) loop at begining
Recover fake list
while(1) loop at end
Fix while(1) at beginning](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-17-2048.jpg)
![CVE-2013-3660
[final state]
Relinked
Entry.Flink
Safelinked
Trampoline - WritePtr
While(1)
WritePtr
2 threads
CPL0 win32k
CPL3 watchdog](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-18-2048.jpg)
![CVE 2013-3660
[‘demo’]
WritePtr to Kernel, ‘countless-times’](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-19-2048.jpg)
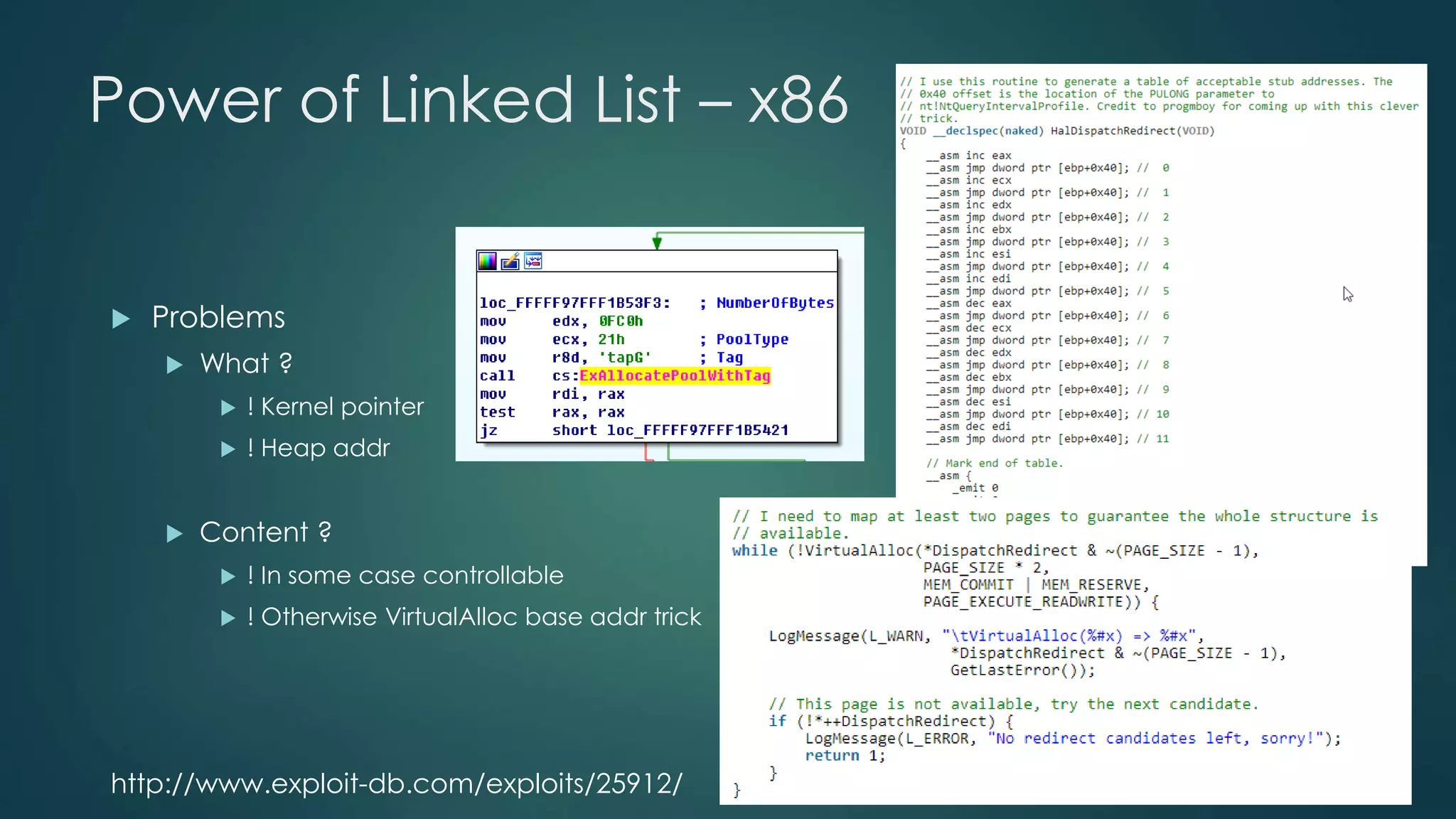


![Write-WHERE
[domino effect]
win32k!PATHALLOC::freelist
win32k!PATHALLOC::cFree](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-24-2048.jpg)
![Write-WHERE
[win32k!PATHALLOC::freelist]
1. Correct but OPTIMIZED
:)
handling
2. Just necessary checks
3. Good target
1. force
FreeList to be
free
2. Then
Rewrite NULL
w valid pointer](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-25-2048.jpg)
![Write-WHERE
[win32k!PATHALLOC::freelist]
win32k!PATHALLOC::freelist
is DISABLED
win32k!PATHALLOC::cFree is
big too huge (~0)
win32k!PATHALLOC::freelist
is empty
By EXAMPLE :
Previously was problems with content
on written PATHRECORD pointer
Solved when called PolyDraw up to
498 for cpt param
But then not trigerred vuln on
win7x64, because of usage of freelist
Problem solved now …](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-26-2048.jpg)
![Write-WHERE
[hidden pointers in kernel]
HalDispatchTable
old school
‘VTABLES’ in kernel
RW pointers in kernel images
Like win32k!..freelist, and many others more
interesting ;)
IoCompletion callbacks
OB_OPERATION_REGISTRATION
nt!_OBJECT_TYPE
OpenProcedure and friends
。。。
Some nice ideas : http://www.nosuchcon.org/talks/2013/D3_02_Nikita_Exploiting_Hardcore_Pool_Corruptions_in_Microsoft_Windows_Kernel.pdf](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-27-2048.jpg)

![Exploitation afterparty
[INFO LEAK PARTY!]
“There’s an info leak party at Ring 0” [Alex Ionescu, recon 2013]
http://recon.cx/2013/slides/Recon2013-Alex%20Ionescu-
I%20got%2099%20problems%20but%20a%20kernel%20pointer%20ain't%20one
.pdf
Modules :
RTL_PROCESS_MODULES
Objects :
SYSTEM_HANDLE_INFORMATION
Page Table :
SUPERFETCH_INFORMATION
“…real deal is querying the PFN database!”
T R U E !](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-29-2048.jpg)
![NtQuerySystemInformation
[GOLD-MINE!]](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-30-2048.jpg)
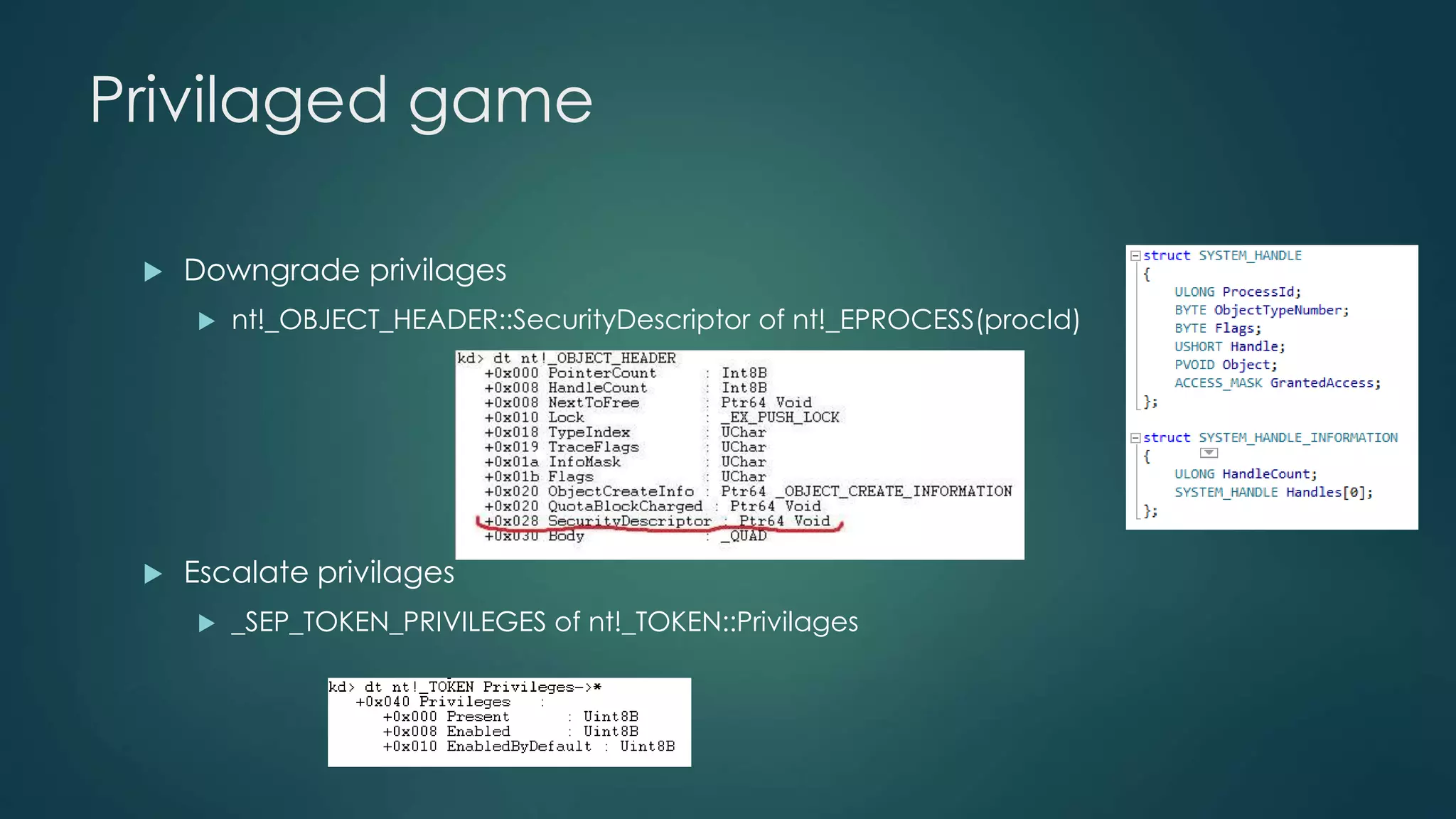
![WritePtr without Kernel exec!
[Privilages--]
With NtQuerySystemInformation
for ever and ever*
Also is possible to substitute
existing security descriptor
with new one!
InitializeSecurityDescriptor
AllocateAndInitializeSid](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-32-2048.jpg)
![WritePtr without Kernel exec!
[Privilages++]](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-33-2048.jpg)
![Kernel space
[Art of knowledge]
Unknown addresses of Kernel modules
Easy way : NtQuerySystemInformation
Hard way : InfoLeak
Unknown Symbols
Lieberal method
LoadLibrary + GetProcAddress in user mode
Do not touch anything sensitive
Resolving via offsets (Microsoft symbols)](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-34-2048.jpg)
![Kernel space [Art of knowledge]
Offset technique :
Reliable
Silent
Easy to use](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-35-2048.jpg)

![Query PFN dtb!
[LEAK LEAK LEAK!]
Setup yourself](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-37-2048.jpg)
![Query PFN dtb!
[LEAK LEAK LEAK!]
Query & find your page](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-38-2048.jpg)
![Advanced Exploitation
[Art of Exec]
SMEP & NonPagedPoolNx
Query PageTable for RWE pages in kernel
Parse page details
Find you RWE page ‘pattern’
And there exist ;)
even on win8.1 !:](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-39-2048.jpg)
![Advanced
Exploitation
[Art of Exec]
SMEP & NonPagedPoolNx
We got RWE page in kernel,
let us write something there!
demo Trampoline for common
HaliQuerySystemInformation tech](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-40-2048.jpg)
![Advanced Exploitation
[Art of Exec]
UserCode in kernel allowed!
Kernel code hidden inside binary
Fully c++ driver!
Mixing User & Kernel code
just avoid direct linking imported kernel functions!
Also avoid to mixing um & km headers together in compile time ;)
Compile standalone kernel code as .lib
link kernel code .lib to exploit .exe](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-41-2048.jpg)
![Advanced Exploitation
[Art of Exec]
1.
Copy whole PE to RWE kernel page
ExAllocatePool(NonPagedPoolExecute,SizeOfImage);
2.
3.
Fix Rellocations
4.
resolve kernel part of
Import table
Ready for exec with CPL0!
CPL Teleport](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-42-2048.jpg)
![Advanced Exploitation
[Art of Exec]](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-43-2048.jpg)

![Conclusions
[ … ]
Driver loading protection
Who cares about breaking Driver loading protection of Microsoft, when
you got a kernel exploit ?
KPP
Not made to punish attackers!](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-45-2048.jpg)
![Conclusions
[ … ]
Info leaks
In win7 everyone can call for info
Win8.1 changed policy, just admin can do it!
Info leaks – admin
Admin < SuperVisor
Admin => Supervisor spy; leak everything ;)
Info leaks, win8.1++
Era of info leaks bugs!](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-46-2048.jpg)
![Conclusions
[ … ]
Win7 => Win8.1++
Win7 is now pretty nice target, do not you think ?
How often companies upgrade their OS, to new one ?](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-47-2048.jpg)
![Conclusions
[ XP - safeguards ]
XP state
Very bad shape :
Unsupported
API for kernel Leaks
No KASLR
No SMEP neither SMAP
…
SafeGuards
Improvements
CVE fixes
Need 0day, or not covered nday!
NtQuerySystemInformation among others disabled
With KASLR good!
KASLR enabled
Info leak necessary!
Driver Verifier
Good idea, but :
Performance ?
Real world usage (no games) ?
Still fixed (predictable) pointers
nt!MiInitializeSessionPool, ..
Still hidden pointers
No SMEP, no SMAP (smap no likely anyway)](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-48-2048.jpg)
![materials
[ cve, techniques, tools ]
http://blog.cmpxchg8b.com/2013/05/introduction-to-windows-kernel-security.html
http://www.exploit-db.com/exploits/25912/
http://recon.cx/2013/slides/Recon2013-Alex%20Ionescu-I%20got%2099%20problems%20but%20a%20kernel%20pointer%20ain't%20one.pdf
http://j00ru.vexillium.org/blog/04_12_11/Windows_Kernel_Address_Protection.pdf
http://www.nosuchcon.org/talks/2013/D3_02_Nikita_Exploiting_Hardcore_Pool_Corruptions_in_Microsoft_Windows_Kernel.pdf
https://media.blackhat.com/bh-us-12/Briefings/Cerrudo/BH_US_12_Cerrudo_Windows_Kernel_WP.pdf
http://poppopret.blogspot.sk/2011/07/windows-kernel-exploitation-basics-part.html
http://www.vupen.com/blog/20130723.Advanced_Exploitation_Windows_Kernel_Win32k_EoP_MS13-053.php
http://www.alex-ionescu.com/?p=51
http://technet.microsoft.com/en-us/sysinternals/ff700229.aspx
http://sebug.net/paper/Meeting-Documents/syscanhk/KernelPool.pdf
http://www.zer0mem.sk/?p=542](https://image.slidesharecdn.com/poweroflinkedlist-141104083411-conversion-gate01/75/Power-of-linked-list-51-2048.jpg)
