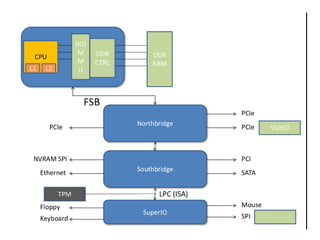
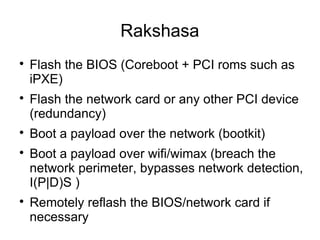
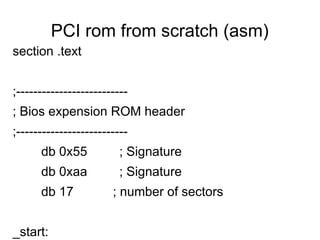
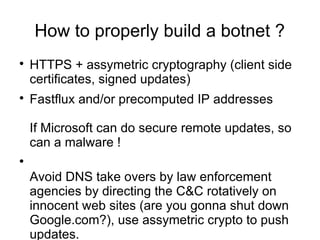
Hardware backdooring by state actors is practical according to the speaker. The speaker demonstrates a proof of concept called Rakshasa that can backdoor computer firmware like BIOS and network cards to achieve persistent remote access. Rakshasa leverages existing free and open source software like Coreboot and iPXE to make the backdoor stealthy and hard to detect. It also discusses challenges with attribution and detection of such backdoors, and argues that strong protections are not currently possible given vulnerabilities in computer hardware and supply chains.