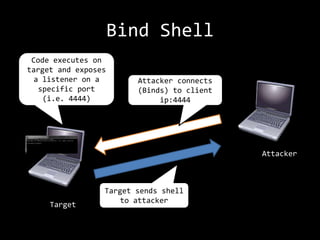
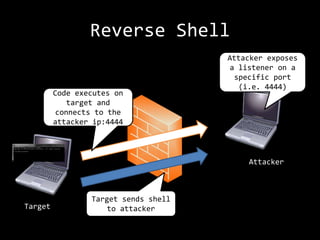
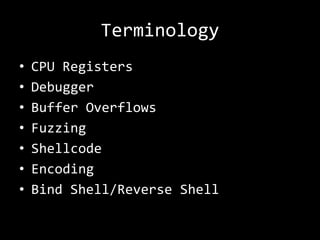
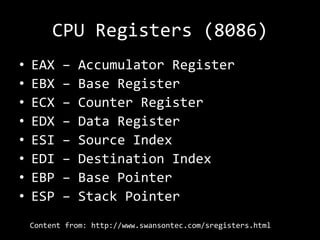
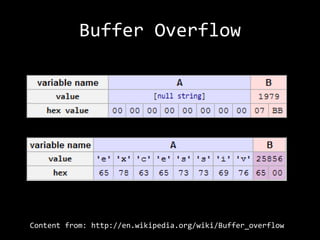
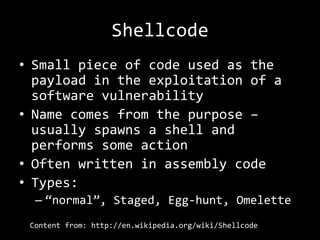
The document describes an anatomy of a buffer overflow attack. It begins with disclaimers about the legal and ethical responsibilities when discussing exploits. It then provides an overview of the scenario which involves exploiting a vulnerability in a Windows FTP server to obtain a reverse shell. It defines relevant terminology like buffers, fuzzing, shellcode and bind/reverse shells. It also provides examples of assembly shellcode and encoded shellcode. Finally, it outlines the process of identifying the vulnerability, designing an exploit through fuzzing and overwriting registers, and obtaining a shell through the exploit.

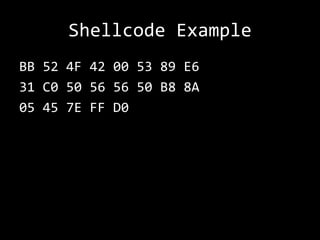
![Shellcode Example
[BITS 32]
mov ebx, 0x00424F52
push ebx
mov esi, esp
xor eax, eax
push eax
push esi
push esi
push eax
mov eax, 0x7E45058A
call eax](https://image.slidesharecdn.com/etcss-bufferoverflow-131023205249-phpapp01/85/ETCSS-Into-the-Mind-of-a-Hacker-14-320.jpg)
![[BITS 32]
mov ebx, 0x00424F52 ; Loads a null-terminated string “ROB” to
ebx
push ebx
; pushes ebx to the stack
mov esi, esp
; saves null-terminated string “ROB” in esi
xor eax, eax
; Zero our eax (eax=0)
push eax
; Push the fourth parameter (uType) to the
stack (value 0)
push esi
; Push the third parameter (lpCaption) to
the stack (value ROB00)
push esi
; Push the second parameter (lpText) to the
stack (value ROB00)
push eax
; Push the first parameter (hWnd) to the
stack (value 0)
mov eax, 0x7E45058A ; Move the MessageBoxA address in to eax
call eax
; Call the MessageBoxA function with all
parameters supplied.](https://image.slidesharecdn.com/etcss-bufferoverflow-131023205249-phpapp01/85/ETCSS-Into-the-Mind-of-a-Hacker-15-320.jpg)