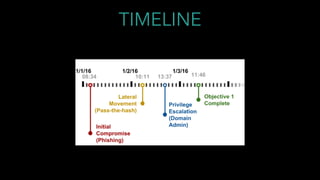
This document discusses moving beyond just prevention of cyber attacks and instead assuming that networks will be breached. It argues that protective technologies will inevitably fail and the focus should shift to detection of breaches. Red team assessments are suggested to shift from just finding vulnerabilities to acting as training partners for blue teams by providing indicators of compromise, attack signatures, and use cases to help improve detection capabilities. A pyramid of pain model is presented to show moving up from just tools to full tactics, techniques and procedures used by attackers.