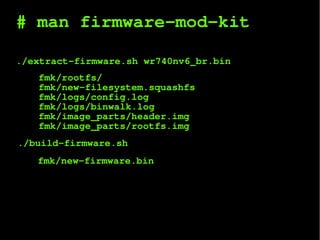
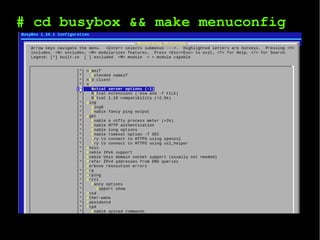
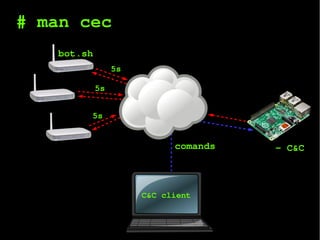
The document outlines a project focused on pentesting and creating command and control (C&C) botnets, detailing processes for extracting and analyzing firmware as well as exploiting vulnerabilities in embedded devices. It includes motivational notes, agenda items related to firmwares, bugs, and various hack logs that document reverse engineering efforts to develop exploits. Furthermore, it highlights tools and methods for firmware analysis and outlines next steps for refining the project.