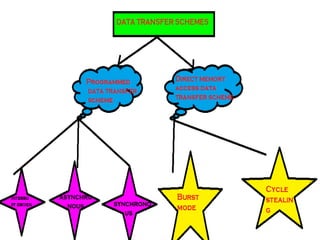
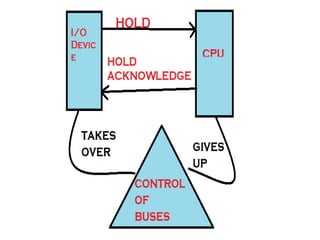
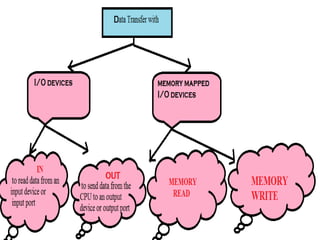
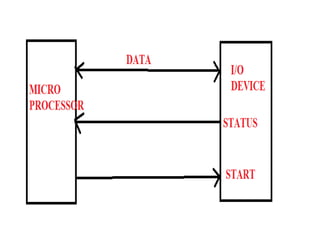
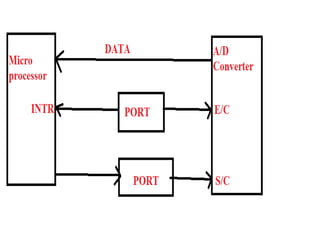
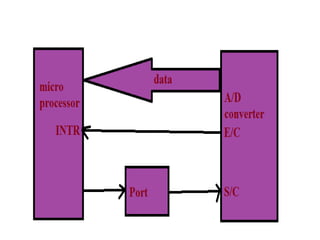
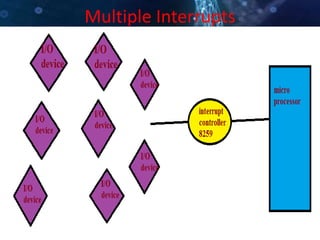
This document discusses various data transfer schemes between I/O devices and memory in a computer system. It describes DMA which allows direct transfer of data from I/O to memory without CPU involvement. It also covers programmed I/O which uses the CPU to control data transfers for small amounts of data. Asynchronous and synchronous transfer methods are explained along with handshaking techniques for asynchronous transfers between devices running at different speeds. Interrupt-driven I/O is also summarized which uses interrupt requests from I/O devices to signal the CPU to service a transfer.