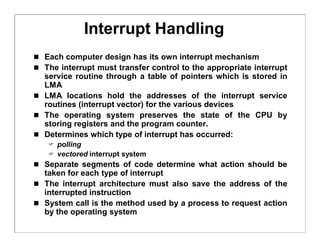
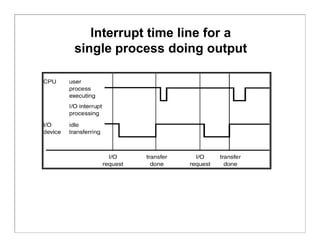
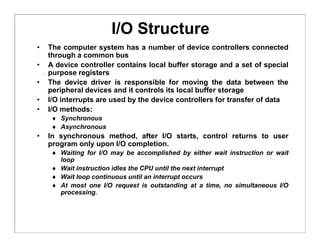
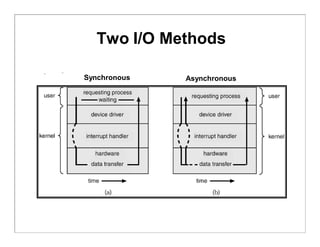
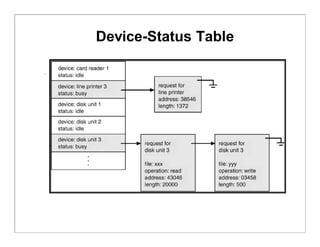
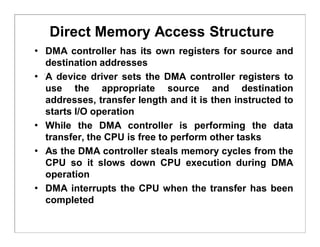
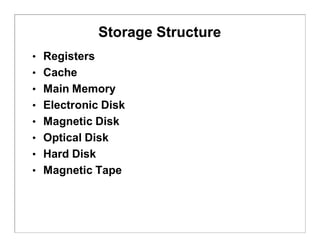
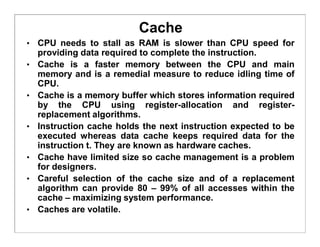
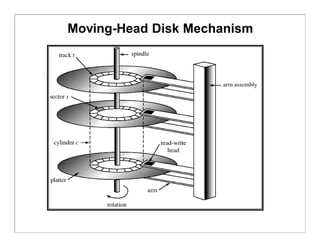
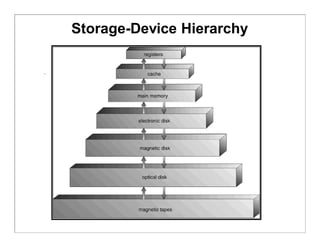
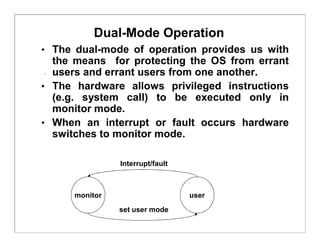
The document discusses various aspects of computer system structures. It describes that a modern computer system consists of a CPU, memory, and device controllers connected through a system bus. I/O devices and the CPU can operate concurrently, with each device controller managing a specific device type. Interrupts are used to signal when I/O operations are complete. Memory is organized in a hierarchy from fastest and smallest registers to slower but larger magnetic disks. Various techniques like caching, paging and virtual memory help bridge differences in speed between CPU and I/O devices. The document also discusses hardware protection mechanisms like dual mode operation, memory protection using base and limit registers, and CPU protection using timers.