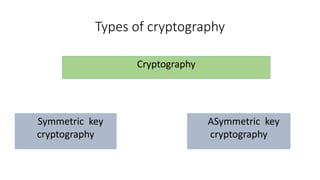
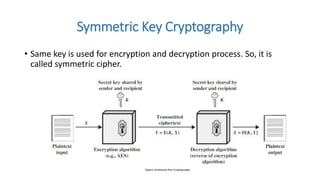
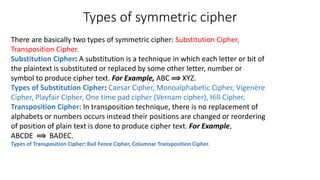
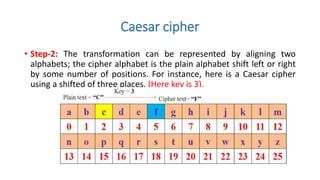
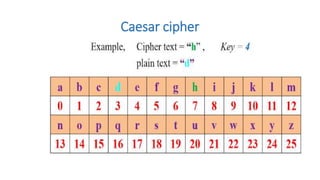
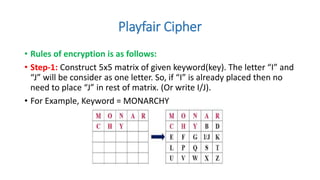
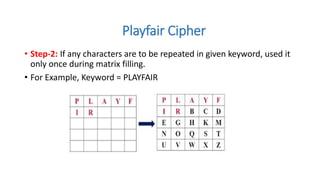
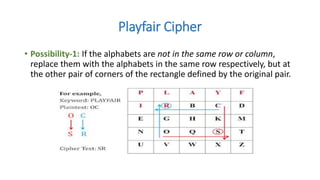
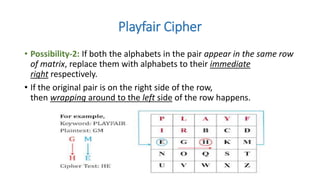
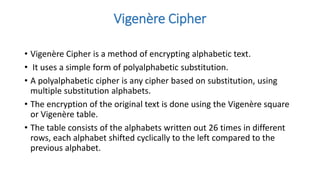
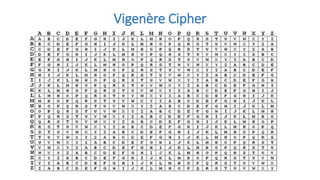
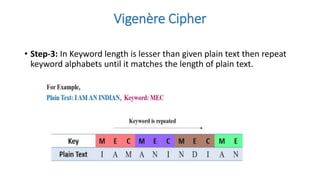
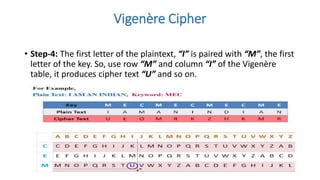
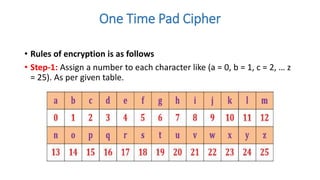
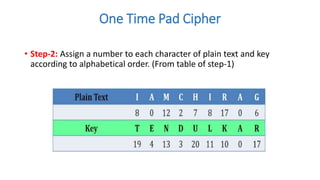
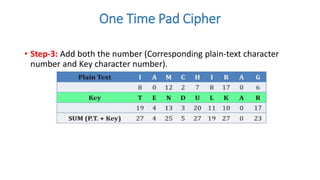
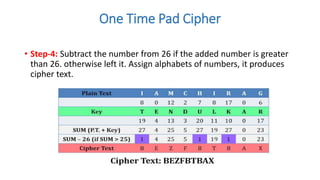
Symmetric key cryptography uses the same key for encryption and decryption. The key types include substitution ciphers that replace plaintext letters and transposition ciphers that reorder plaintext letters. Common symmetric algorithms are AES and DES. Caesar cipher is a simple substitution cipher that shifts each letter by the key amount (such as 3 places). Playfair cipher encrypts plaintext letter pairs using a 5x5 grid keyed from a word. Vigenère cipher uses a table to encrypt plaintext letters based on a repeated keyword. The one-time pad perfectly encrypts by combining a random key with the plaintext.