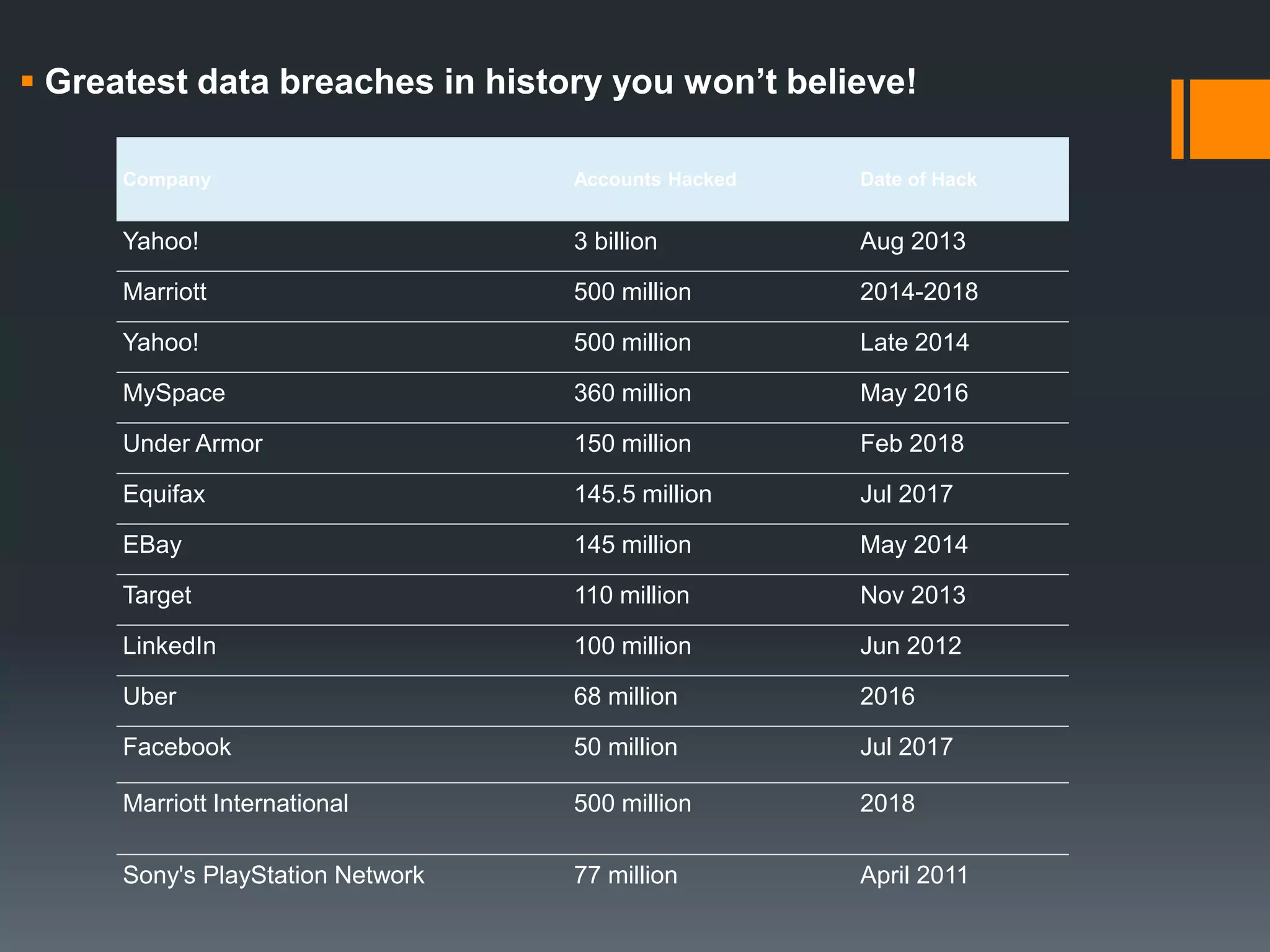
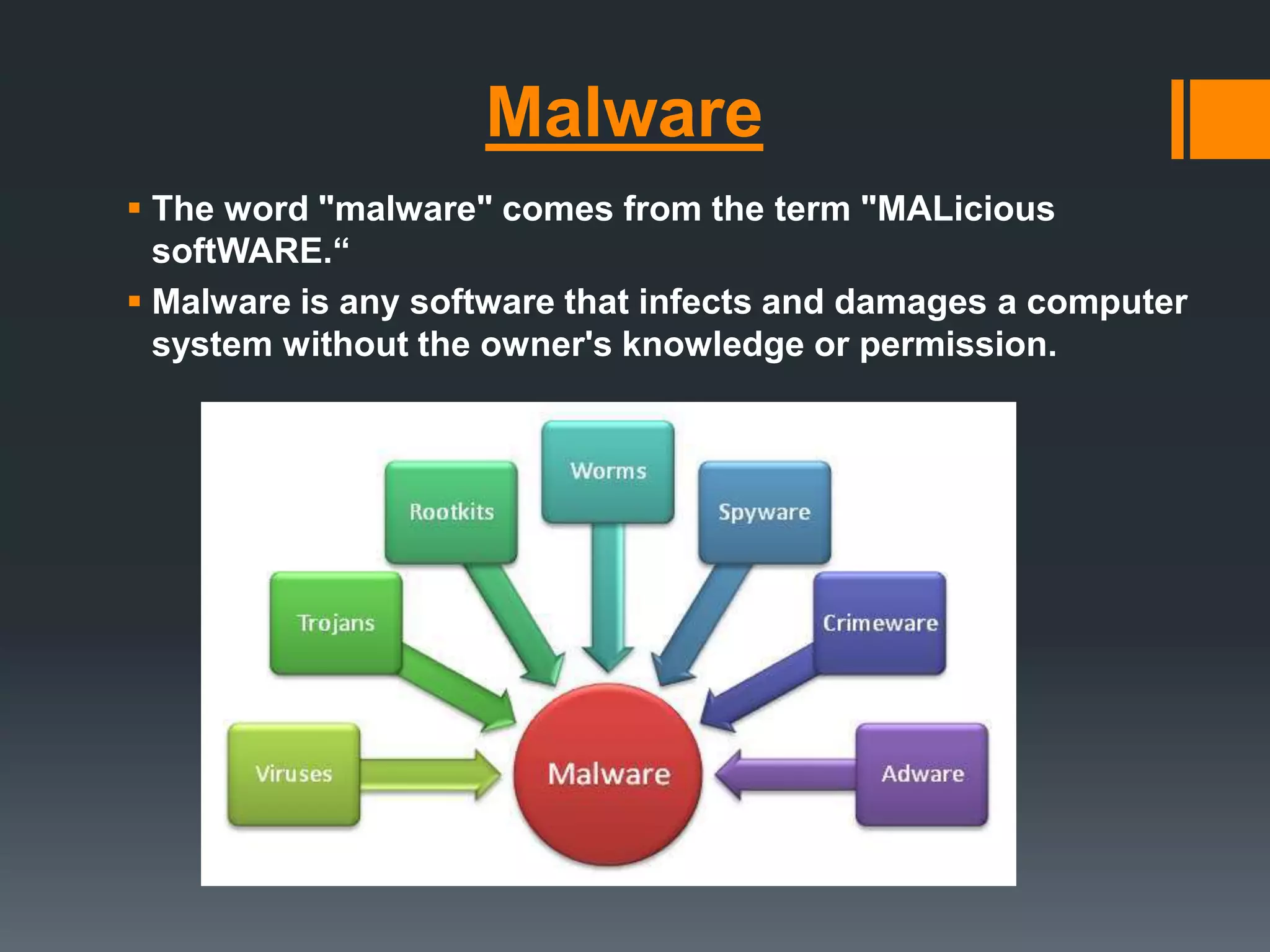
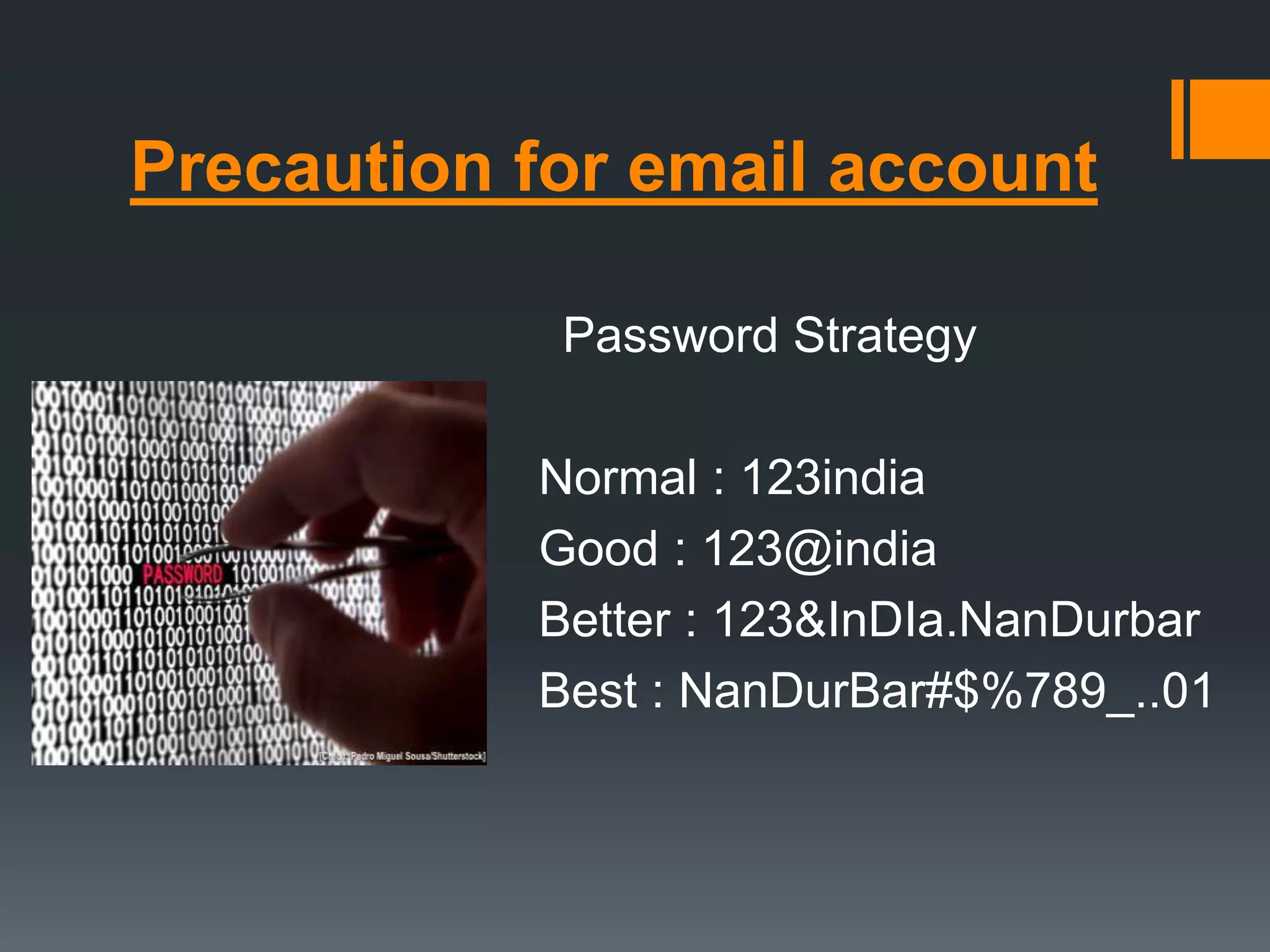
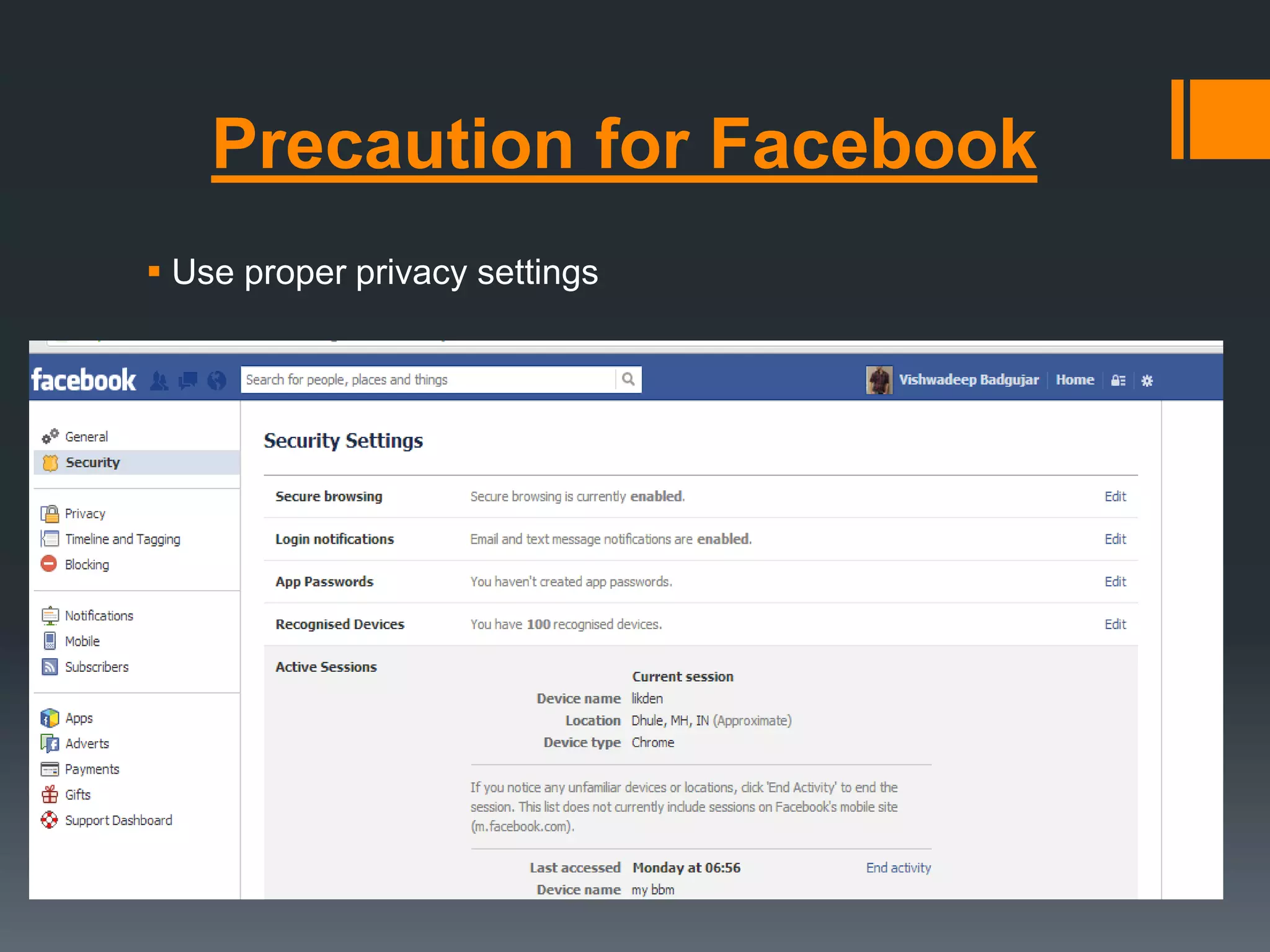
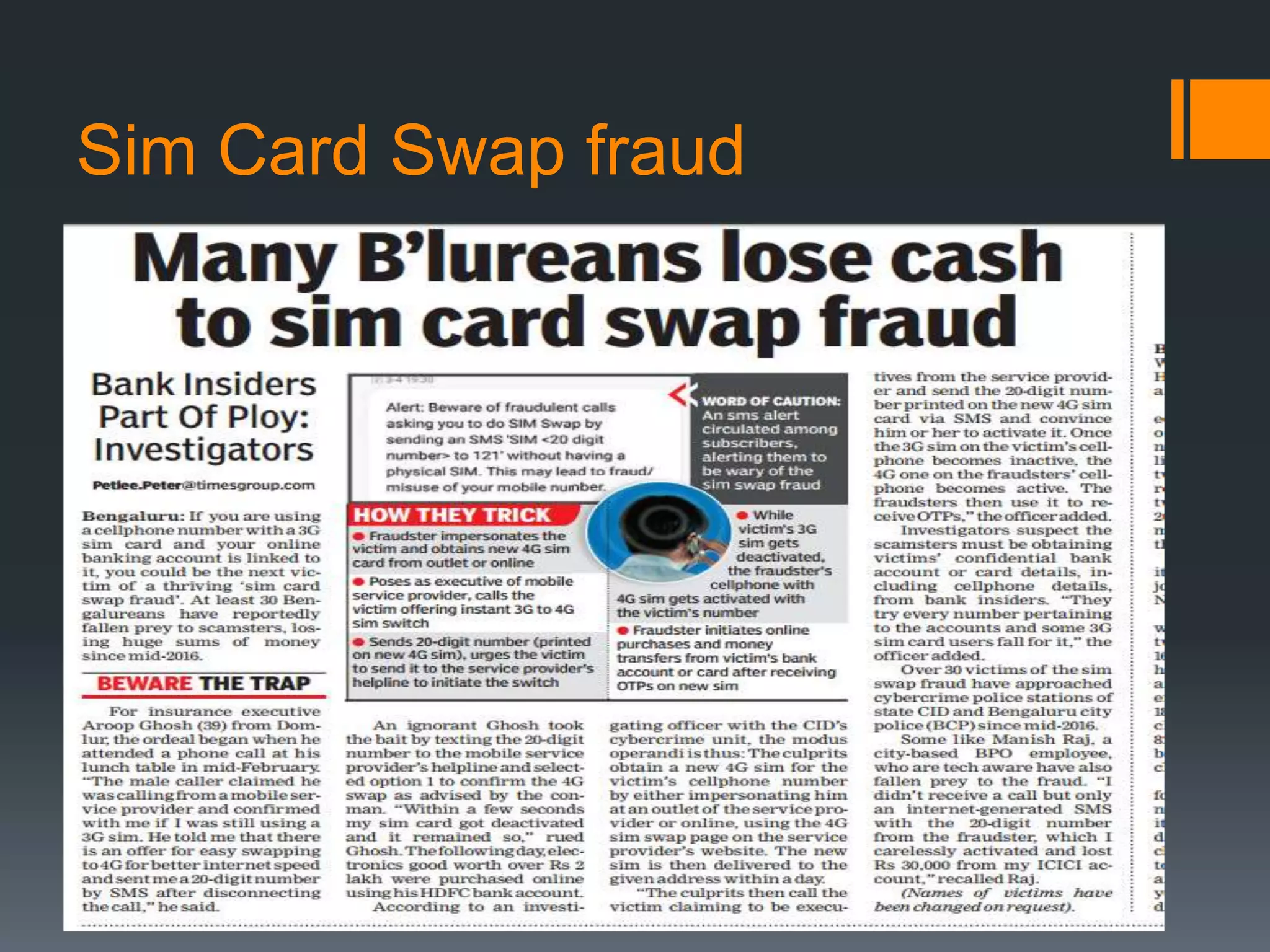
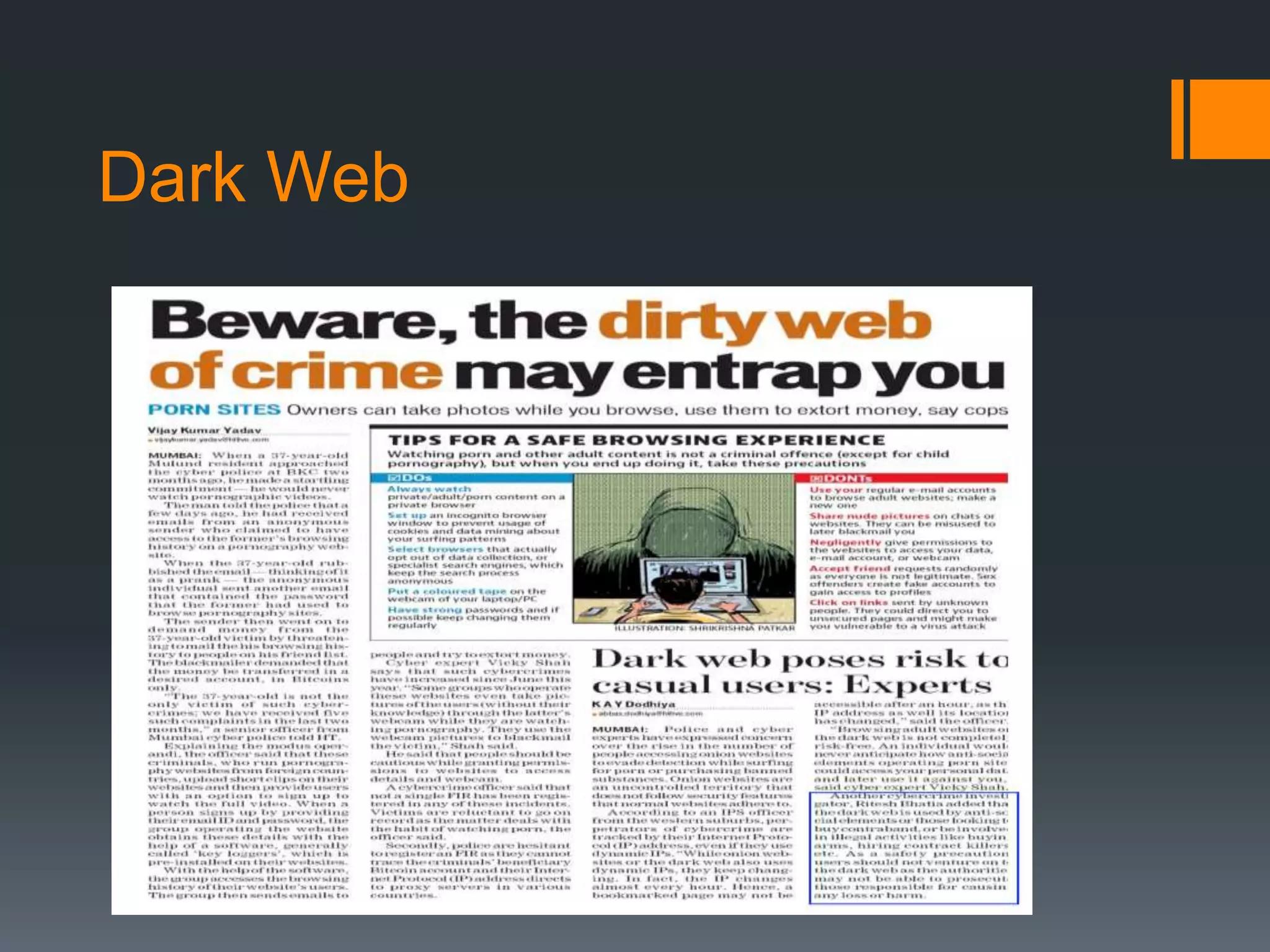
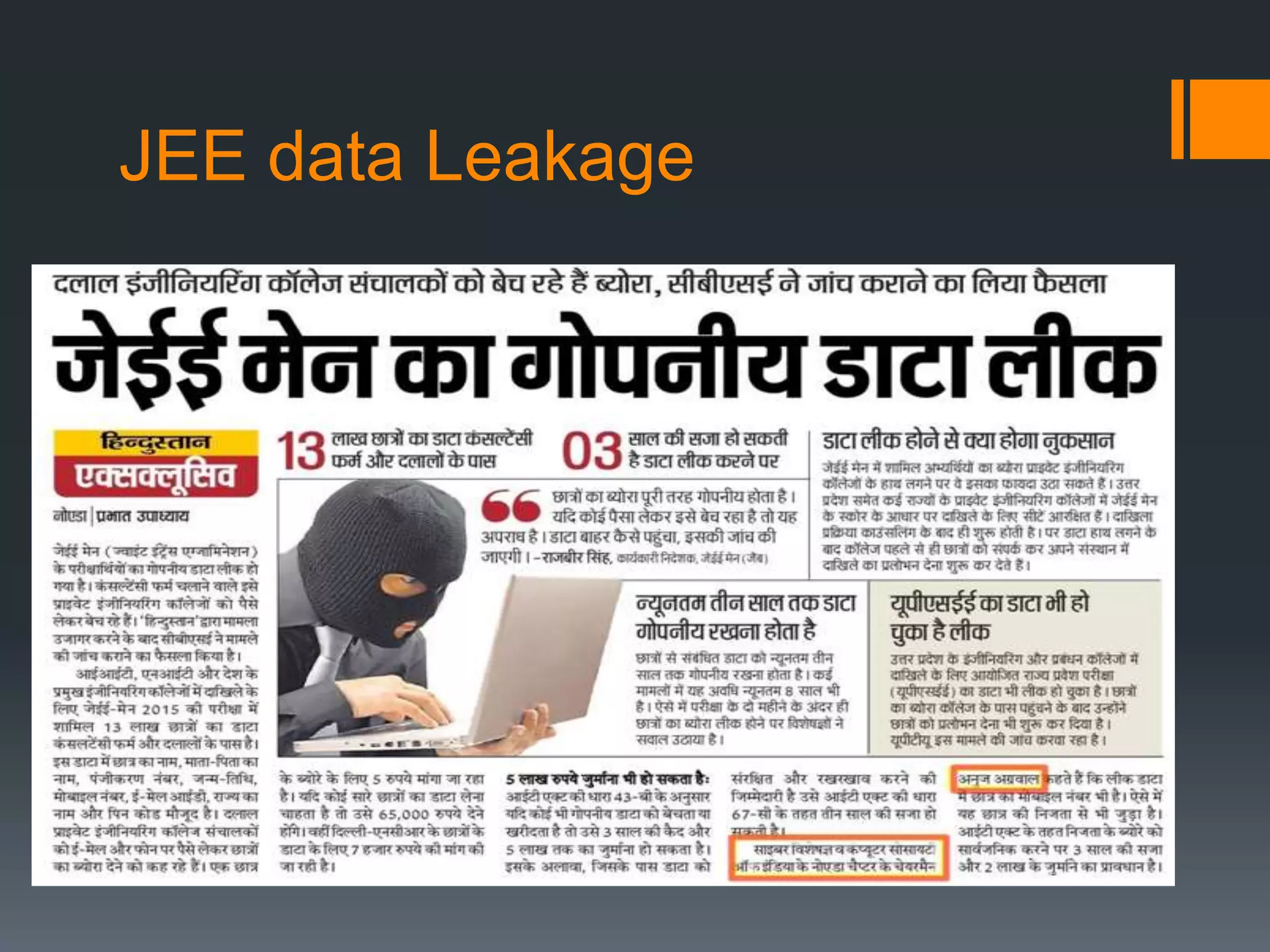
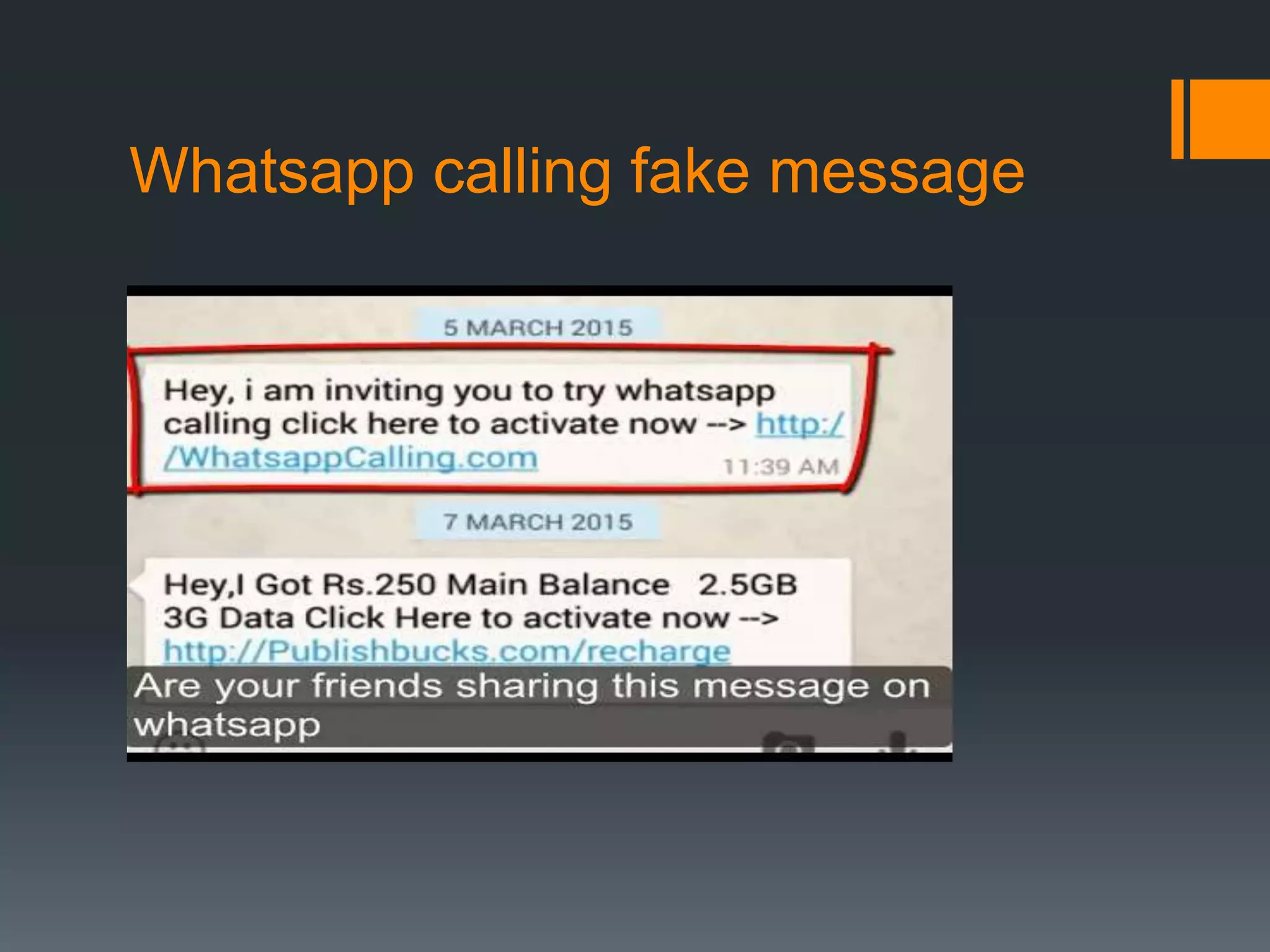
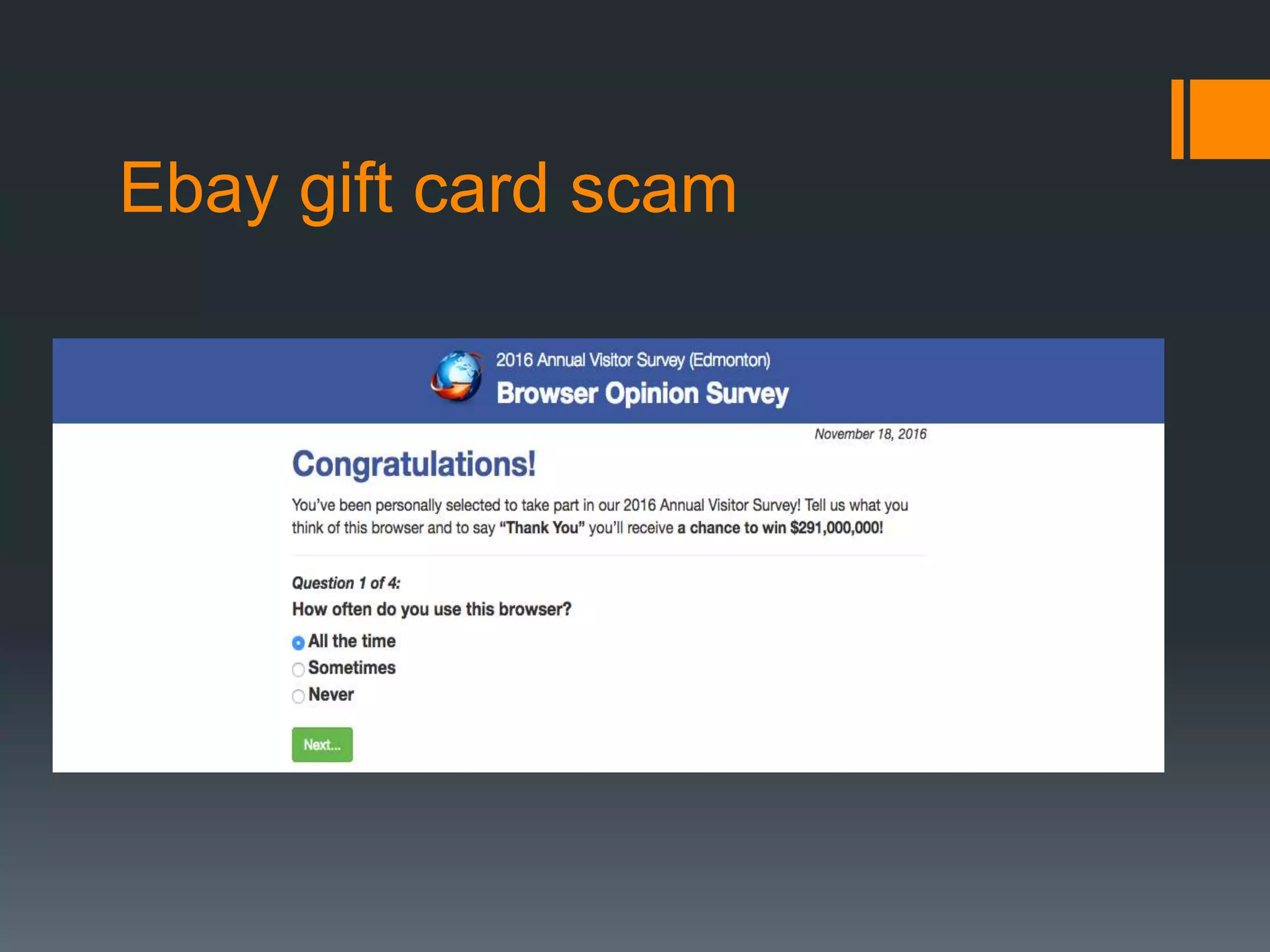
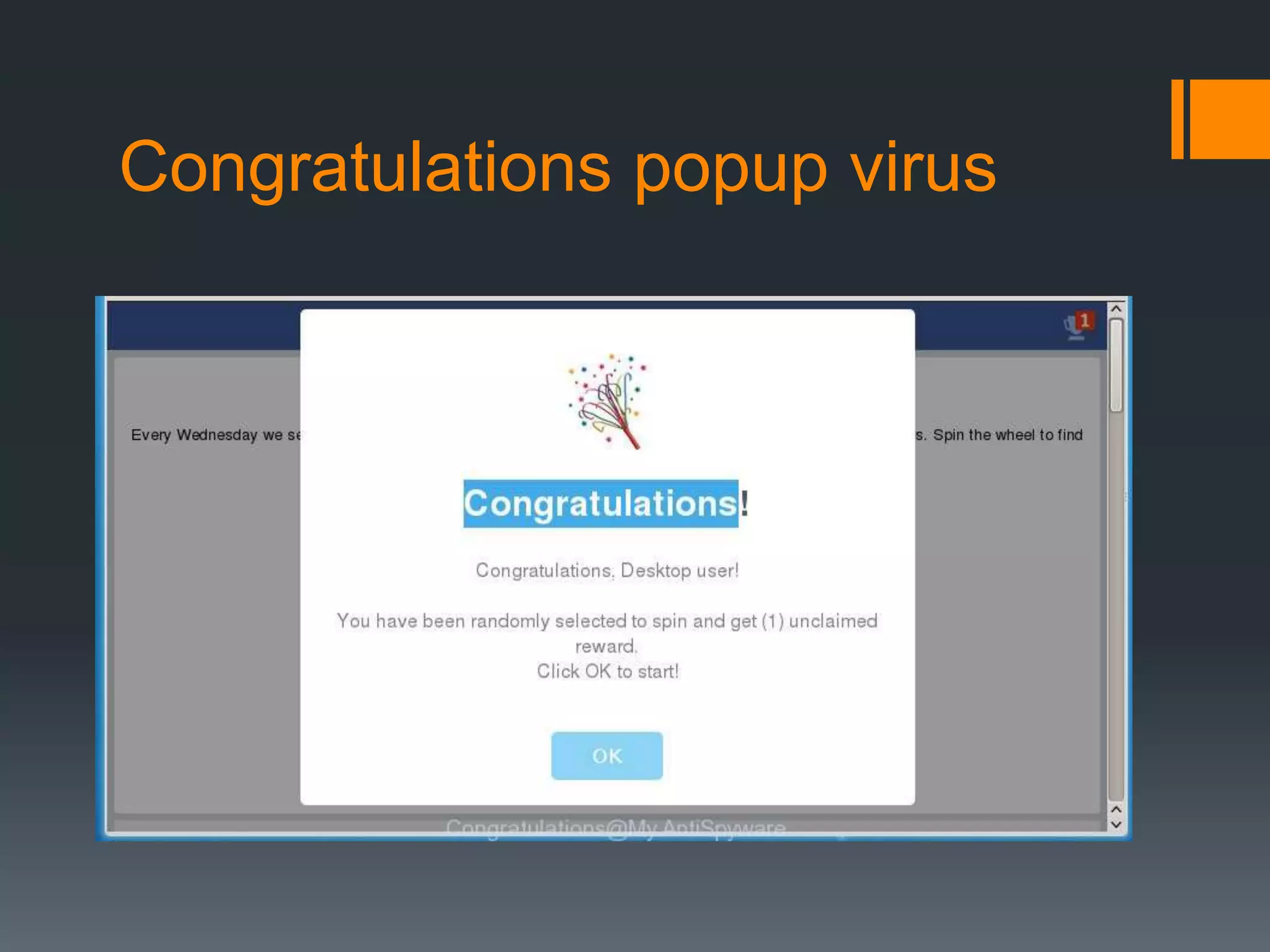
The document outlines the growing issue of cyber crime in India, highlighting its definition, types, and the evolution of threats as technology advances. It emphasizes the rapid increase in attacks, particularly targeting small businesses, and stresses the importance of implementing robust cyber security measures to protect against data theft and other malicious activities. Key statistics and examples of major data breaches further illustrate the urgent need for effective security practices to safeguard sensitive information.