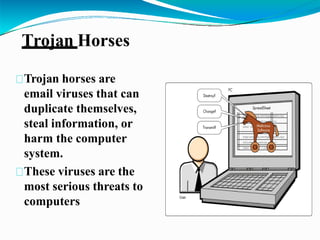
This document discusses cyber security and cyber crimes. It begins by explaining why we should be aware of cyber crimes given how connected the world is today through technology. It then provides a brief history of cyber crimes, defining cyber security as technologies and processes to protect computers and networks from unauthorized access. The document outlines some major cyber security problems like viruses, malware, trojan horses, password cracking, and hackers. It explains these threats and provides tips on cyber security best practices to prevent attacks and data theft. In conclusion, it emphasizes that cyber security is everyone's responsibility and outlines India's national cyber security strategy.