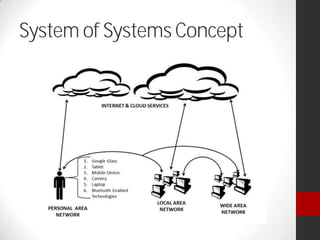
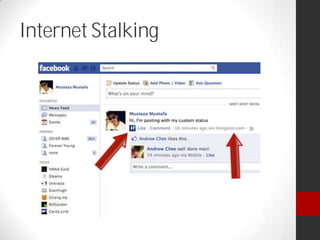
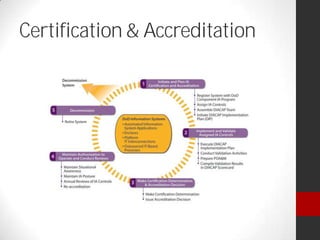
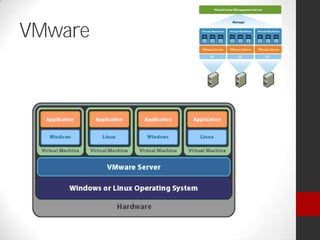
Dr. Maurice Dawson presented on cyber security. He discussed the growing trend of hyperconnectivity and how it is challenging cyber security. He covered guidance, tools, and training needed to address threats in an increasingly connected world. Dawson also outlined his background and current research focusing on cyber security, including mobile device security, cyber terrorism, and ensuring the delivery of secure systems.